December honeypot report
I think that I'll stop posting monthly reports from our Telnet & SSH honeypot. The database has become too large, monthly data is like 4-5 million rows, and the query takes such a long time that Grafana times out on some panels:
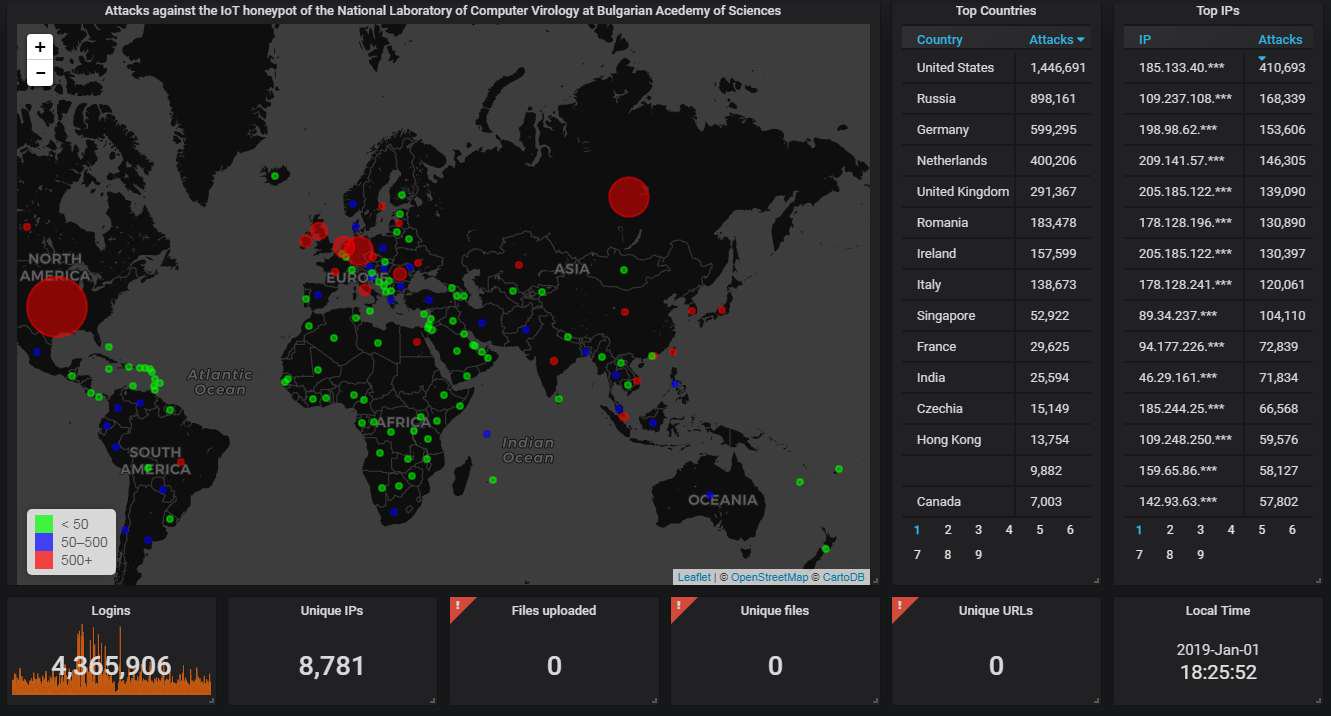
Indexing helps speed up some simple queries (like those that are responsible for the world map and the two columns to the right of it) but more complex ones that use DISTINCT and GROUP BY just take too long to complete in reasonable time.
Maybe someone who knows MySQL better than me could help me speed up these queries but, on my own, I give up.
I could still post a report from our two other honeypots (SMB and ADB), though.
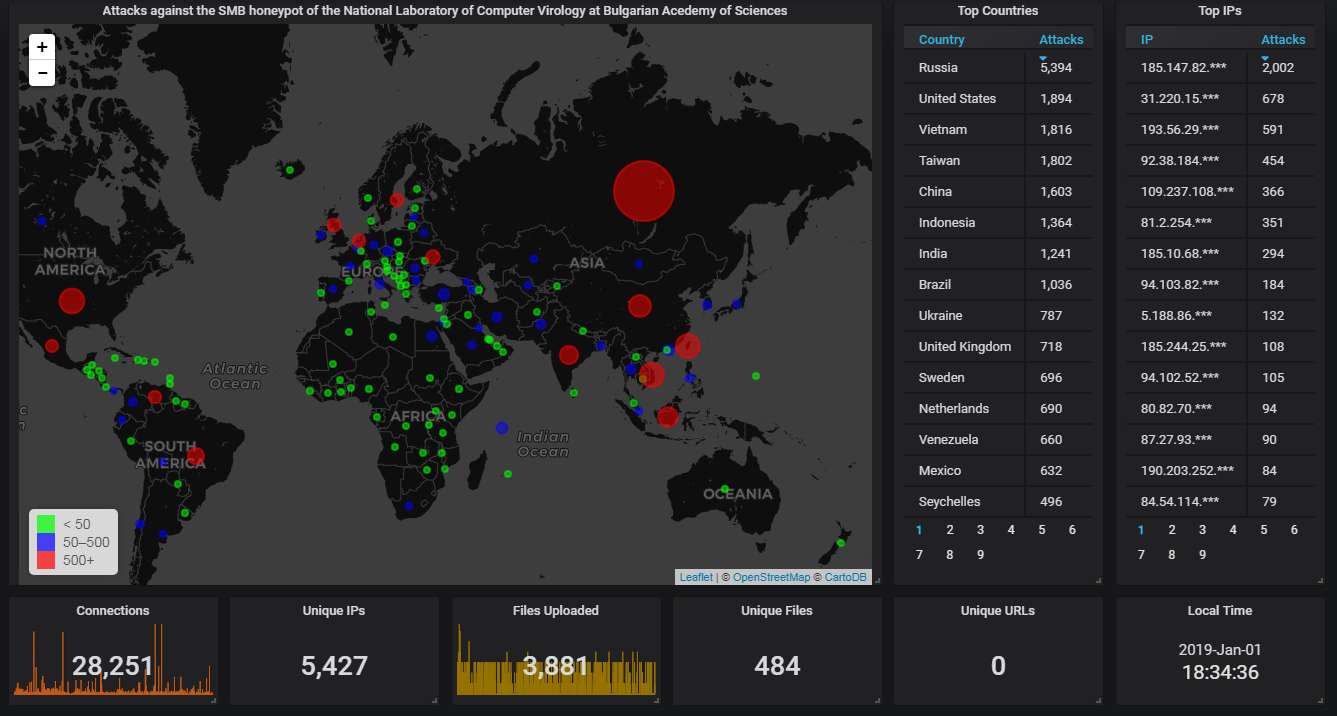
So, here is the big picture from our SMB honeypot. Unlike Telnet & SSH, where the USA is the undisputed leader, here Russia takes the first place again this month:
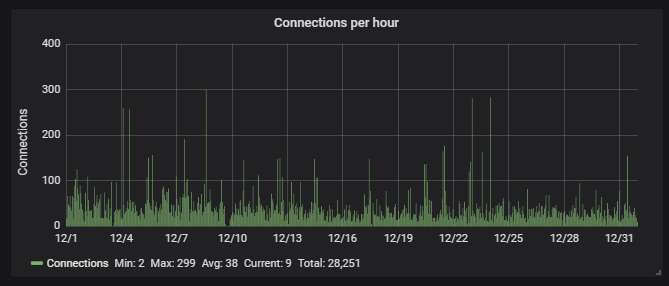
The SMB traffic is much lower than Telnet & SSH - averaging 2-3 connections per minute:
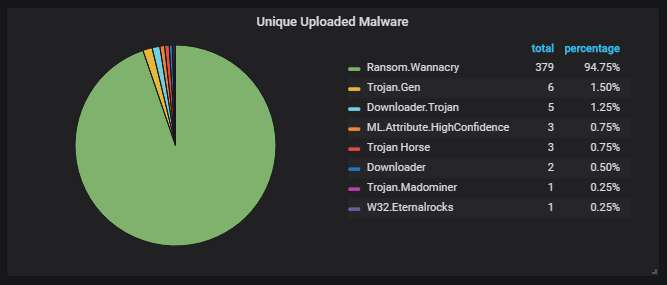
95% of the unique files are corrupted WannaCry variants (don't check the kill switch, don't encrypt, so they spread unnoticed), the rest is downloaders. Conficker is conspicuously missing this month. (Symantec's scanner was used here; it calls it "Downadup".)
Details about the top-20 most actively attacking IPs; you can see why Russia is at the top.
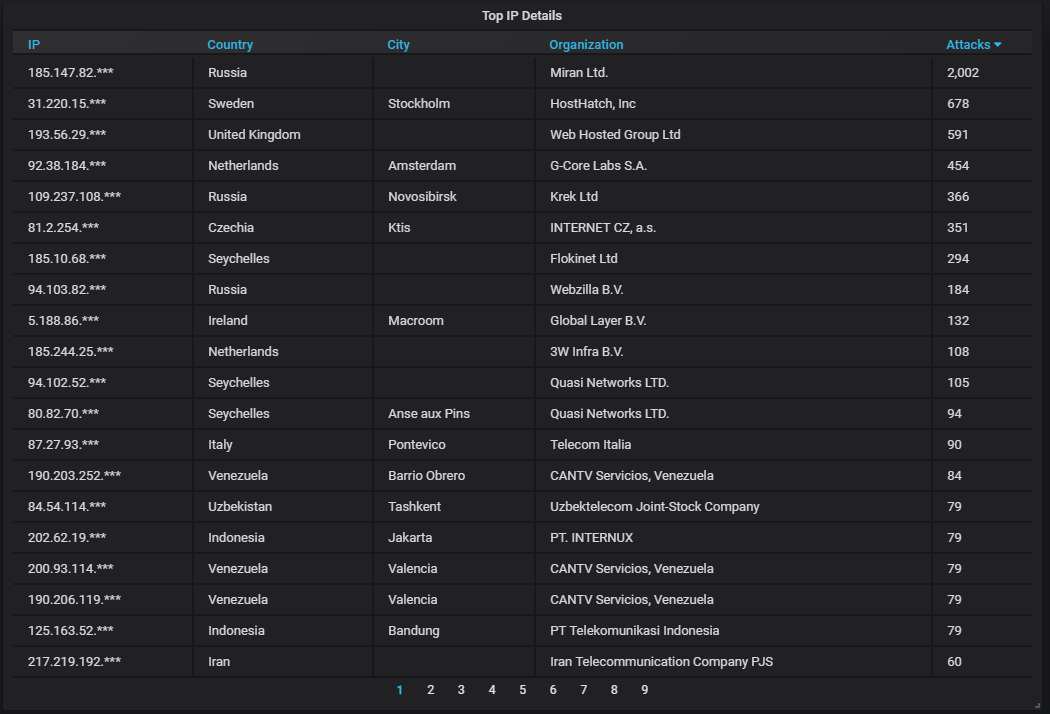
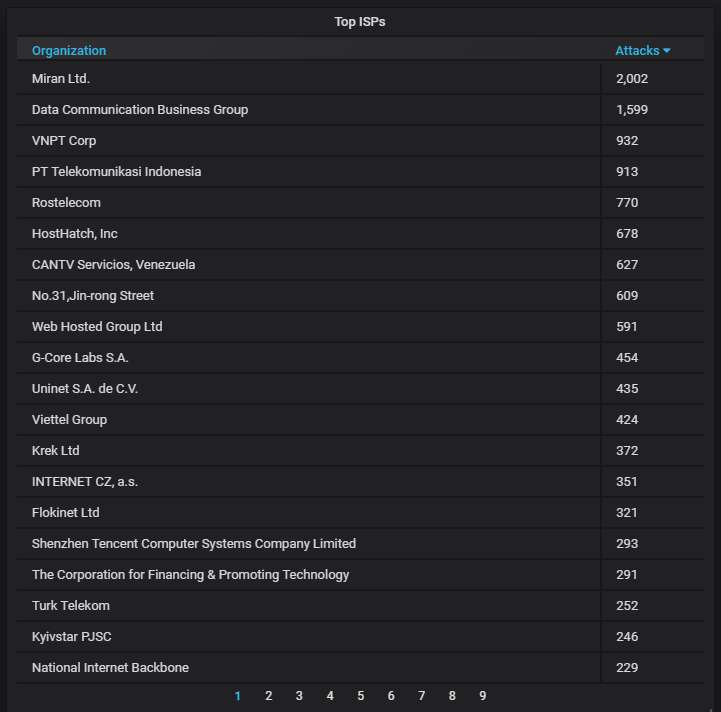
Finally, the top-20 ISPs from which the most attacks are coming; again that Russian one is responsible for most of the traffic.
Note that these are connections that could be just scanning; not necessarily malware uploads.
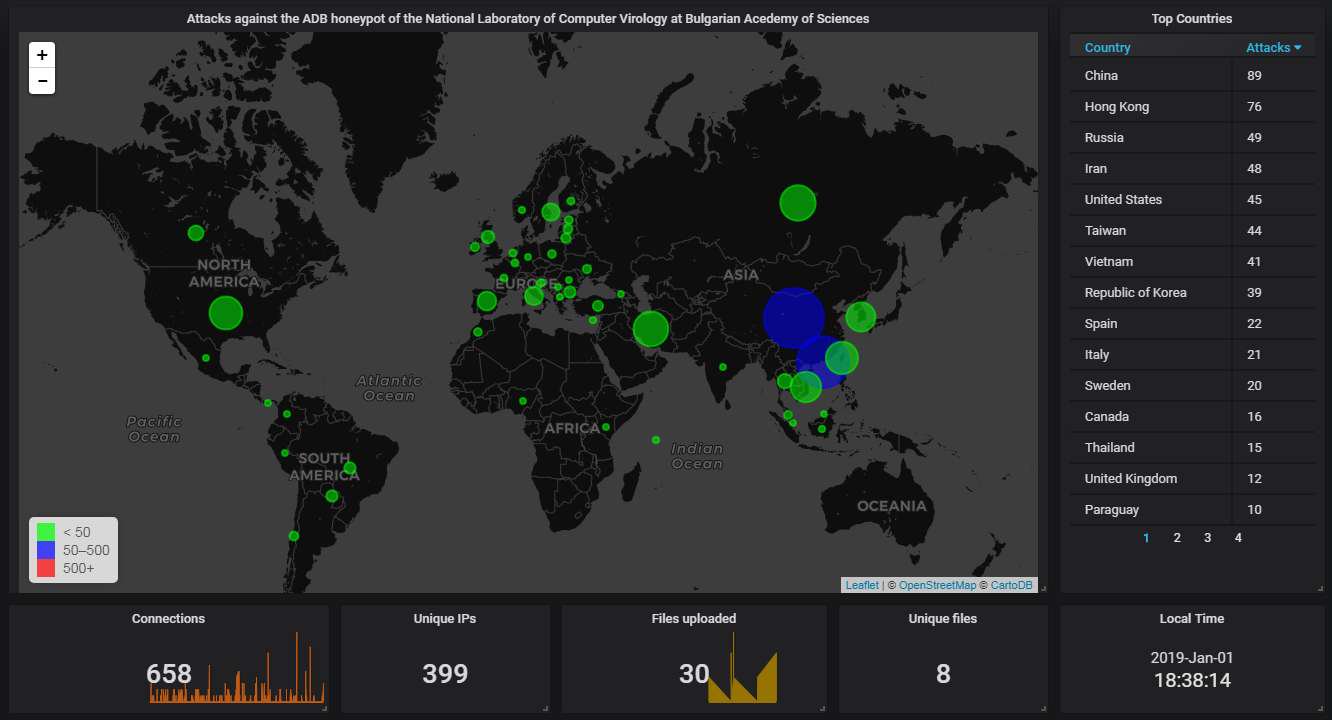
OK, now let's take a look at our ADB honeypot. It's still under development and we have less than a month's worth of data.
First, the big picture. Here China & Hong Kong are the leaders:
Very low traffic here, averaging 2.5 connections per hour. It's mostly the same thing over and over again, too - as you could see on the previous picture, only 8 different files were uploaded.
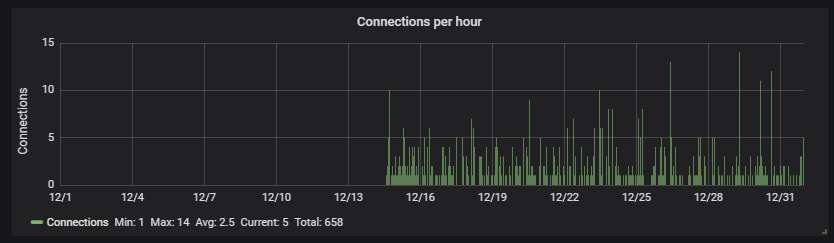
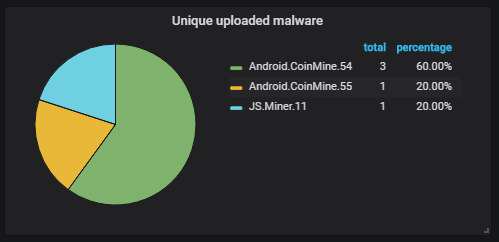
Of these 8 unique files, 5 are some kind of miners. The other 3 are not executable files; I suspect they're some kind of data files for the miner. The scanner used here was Dr. Web.
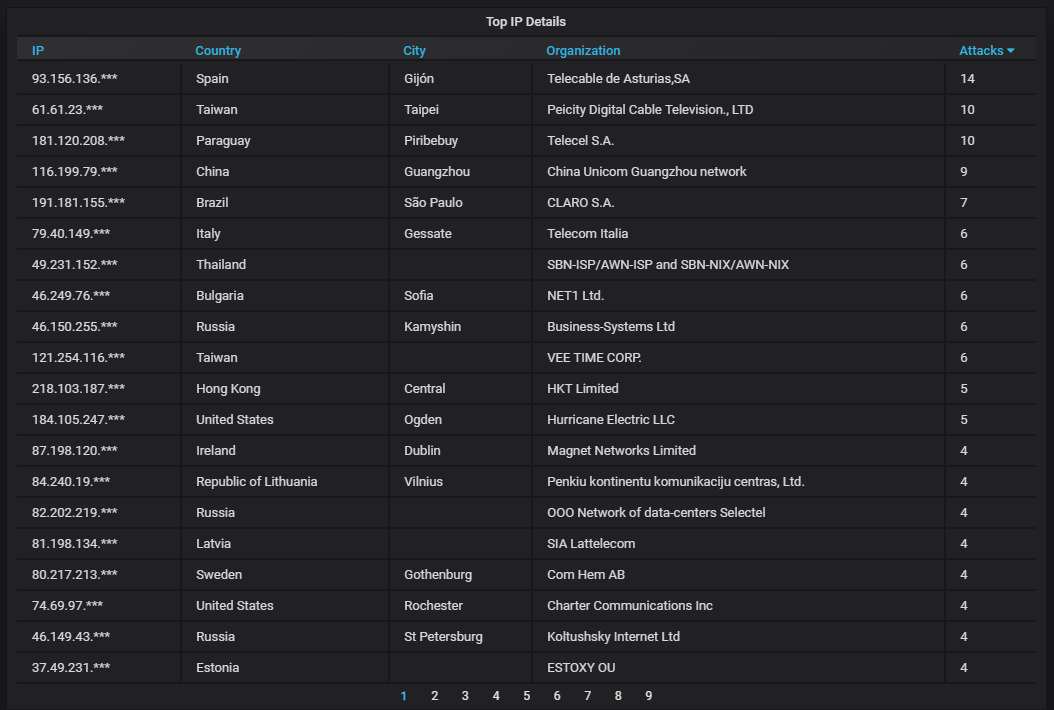
Details about the top-20 most actively attacking IPs. Yay, a Bulgarian IP is #8.
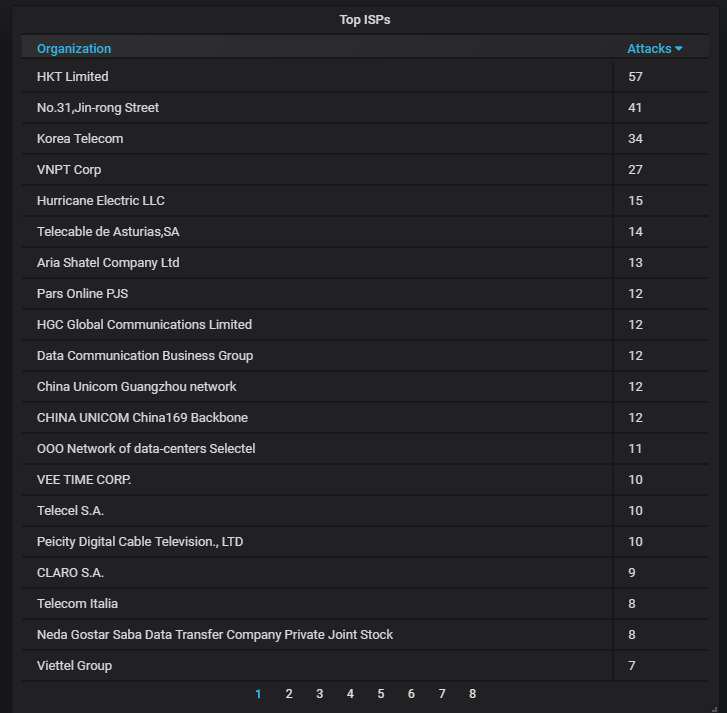
Finally, detailed information about the top-20 ISPs from which most of the attacks are coming. You can see why China and Hong Kong are at the top.
This concludes the report.
