May honeypot report
First, the data from our Telnet & SSH honeypot. The big picture looks like this. As usual, most attacks have come from the USA, although the Netherlands is close behind:
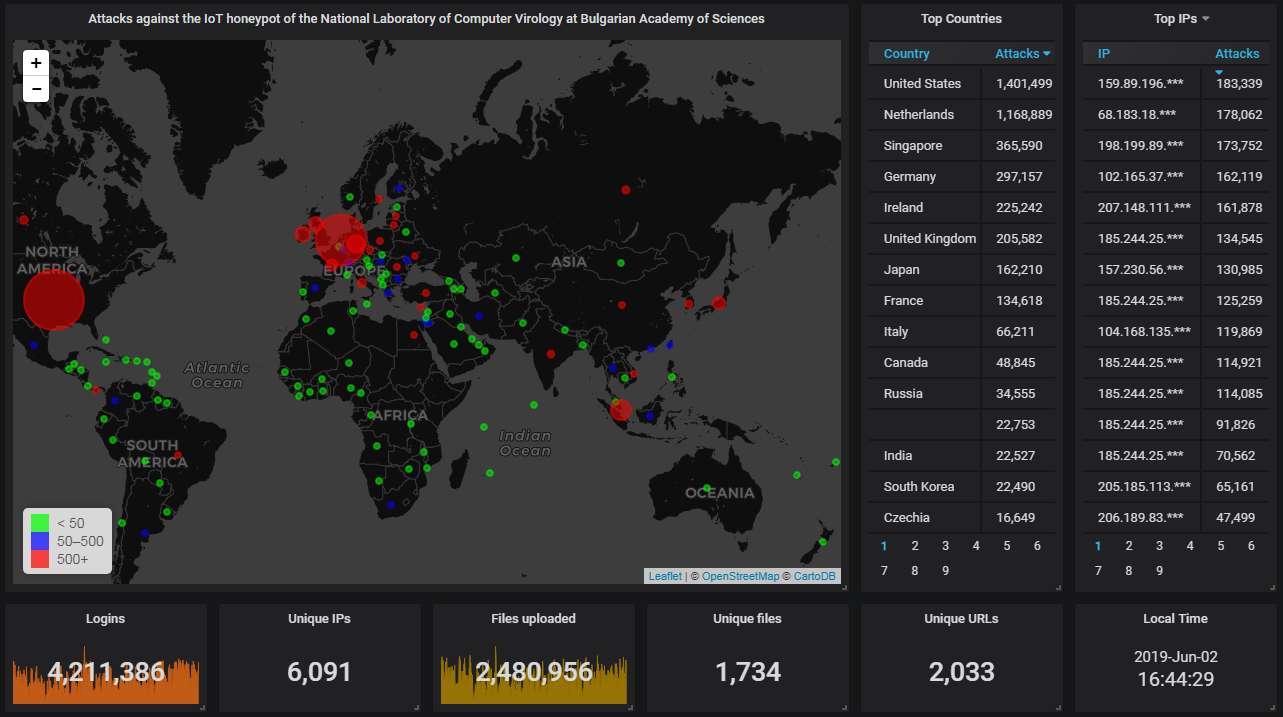
Here is how the hourly activity looks like. Pretty steady traffic, almost 1.6 attacks per second. The gaps are caused us taking the honeypot down for backup purposes.
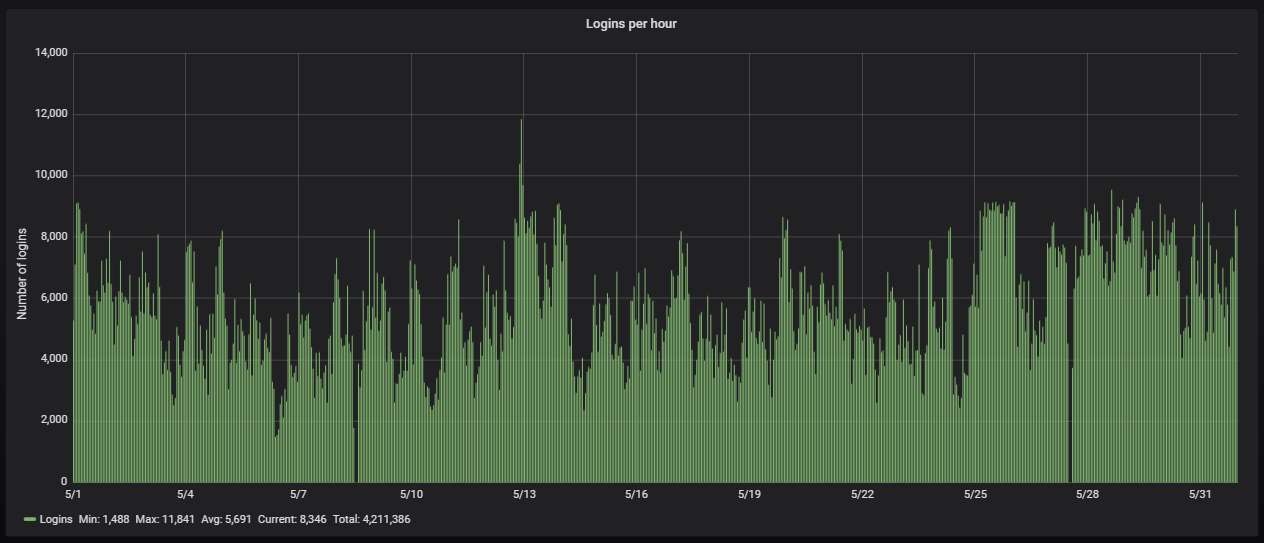
As usual, more than 90% of the attacks are via Telnet, the rest are via SSH:
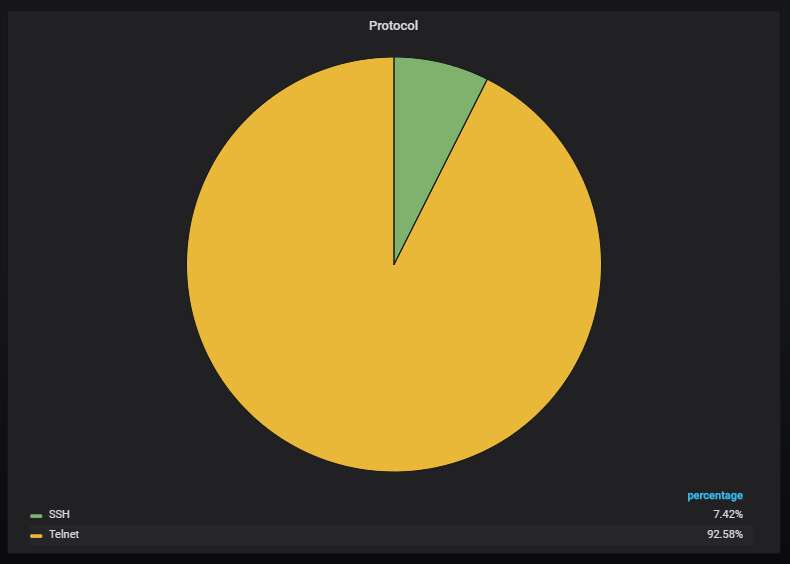
The top-5 URLs from which malware was most actively uploaded to the honeypot. Mirai variants all of them, as usual, although the original variant is not among them.
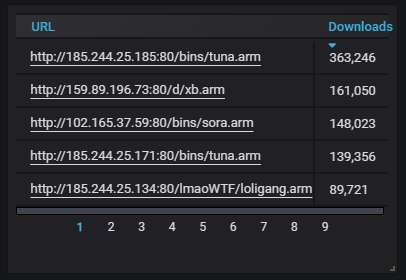
Details about the top-20 most actively attacking IPs. As usual, DigitalOcean is heavily present. The Dutch KV Solutions is playing catch-up but still noticeably behind overall.

The top-20 most actively attacking organizations. DigitalOcean is at the top, as usual. You see what I meant when I said that KV Solutions is trying to catch up but still noticeably behind:

As you can see, I've been sending averagely about a hundred automated abuse reports to DigitalOcean every day - but it doesn't seem to be helping very much.
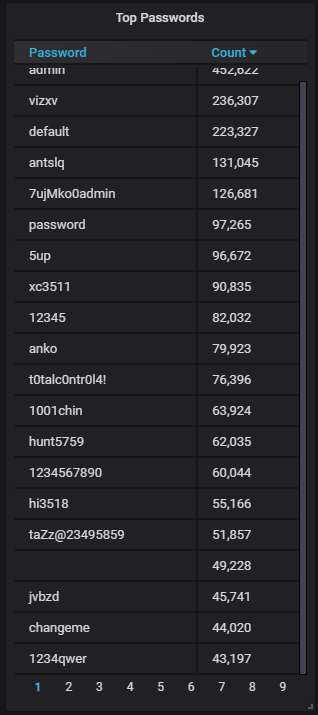
The top-20 passwords that are the most often used by the attackers; nothing unusual here:
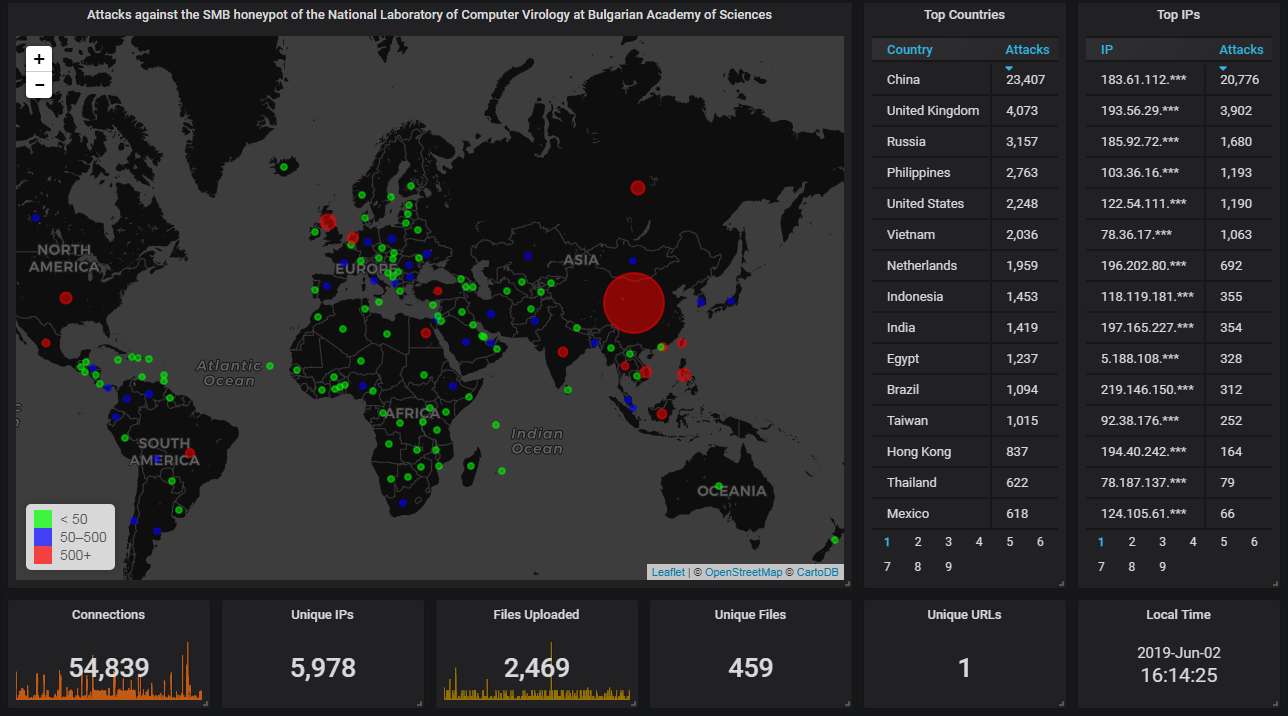
Moving on to our SMB honeypot.
First, the big picture. Here China firmly holds the top spot this month:
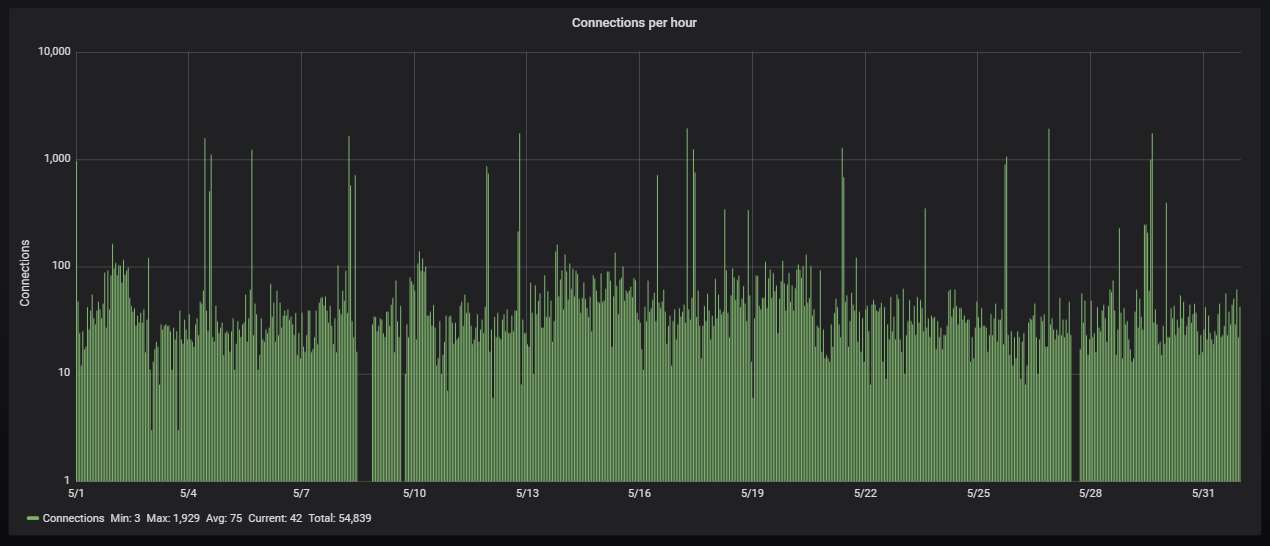
Hourly activity, showing averagely a bit more than one attack per minute. I've switch to a logarithmic scale, otherwise the lonely spikes of more than a thousand attacks coming from a single IP (usually infected with a WannaCry variant) tend to drown out everything else. Otherwise the traffic is pretty steady, albeit much lower than the one that the Telnet honeypot gets.
The big gap is caused by the problem that, once the machine is turned off, the SMB honeypot would take hours to start working. Thankfully, my colleague managed to solve that problem a few days ago, so hopefully we won't be seeing gaps caused by it any more.
Unique uploaded malware variants, according to Symantec's scanner. Lots of corrupted WannaCry variants, as usual (no kill switch check, no encryption).
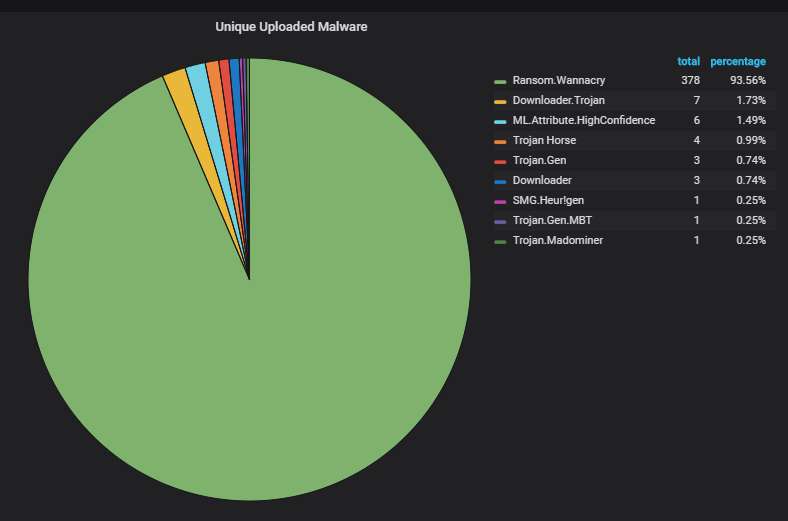
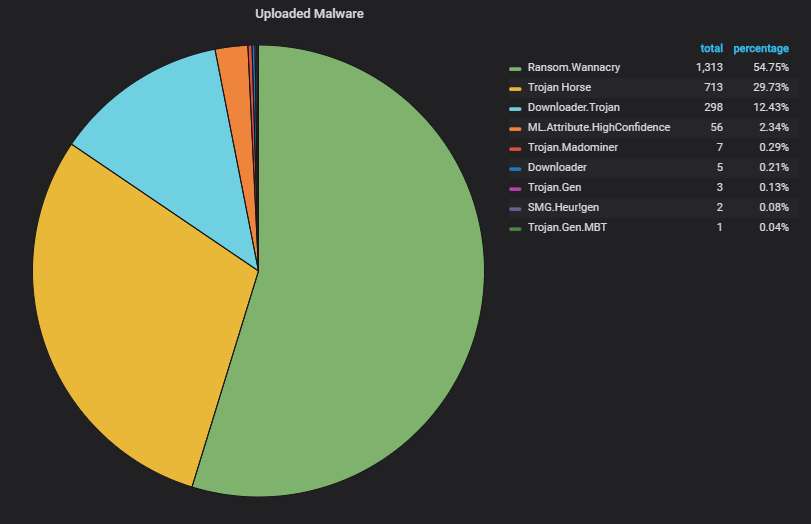
Note that WannaCry uploads dominate, although not as overwhelmingly, even if we don't count only the unique variants:
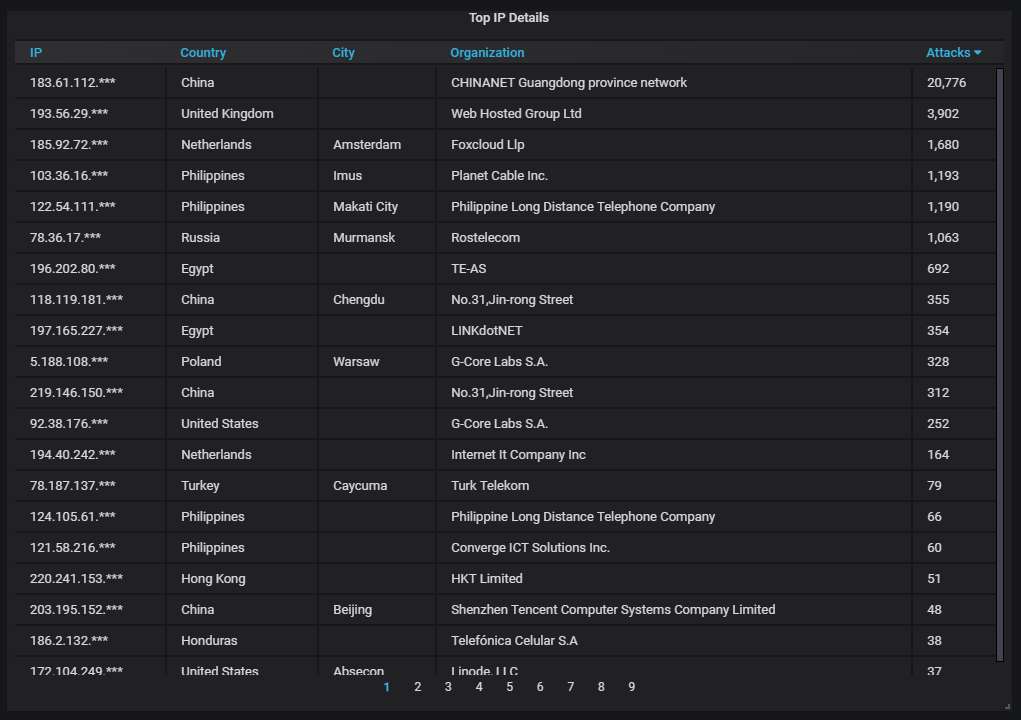
Details about the top-20 most actively attacking IPs. Somebody Guandong, China, definitely has a bit of a WannaCry problem...
The top-20 organizations from which most of the attacks are coming from. Nothing unexpected here:

Finally, the data from our ADB honeypot.
The big picture shows this time Hong Kong holds the top spot, again, which is not unusual. Generally, the Far Eastern countries (China, Hong Kong, South Korea) seem to have a huge population of devices with the ADB port open to the Internet with no authentication.
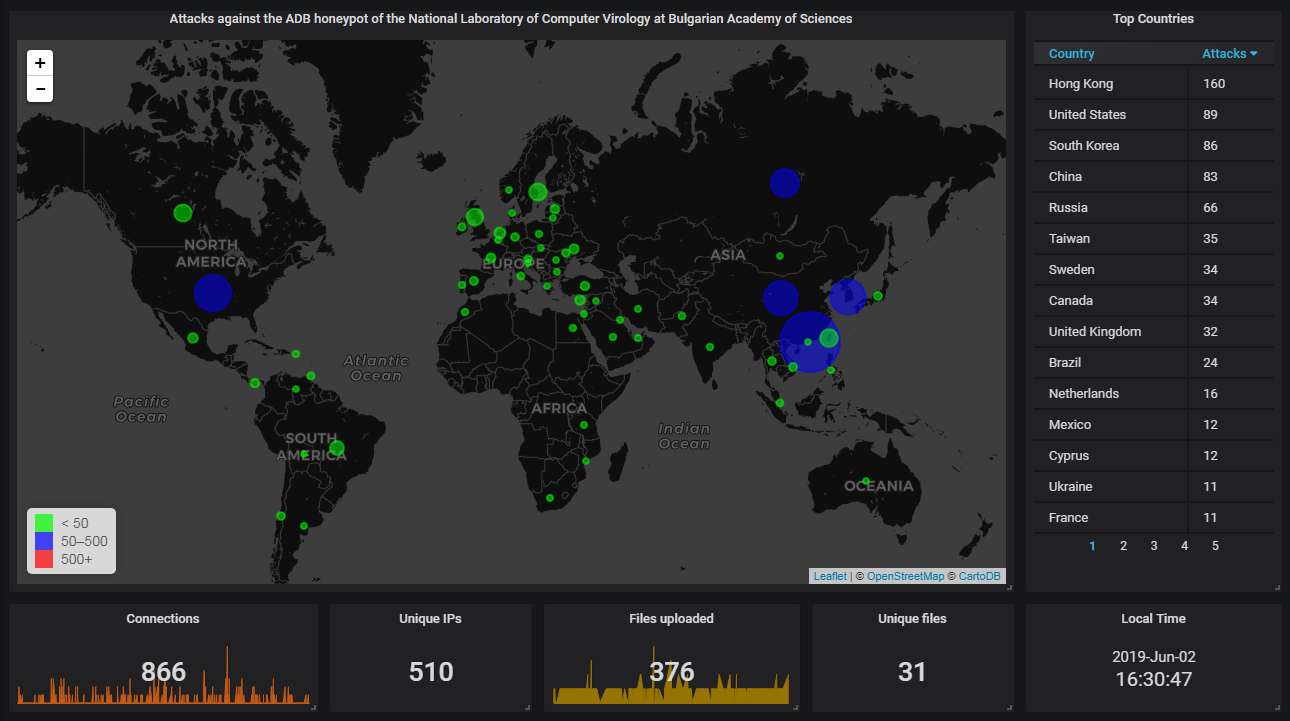
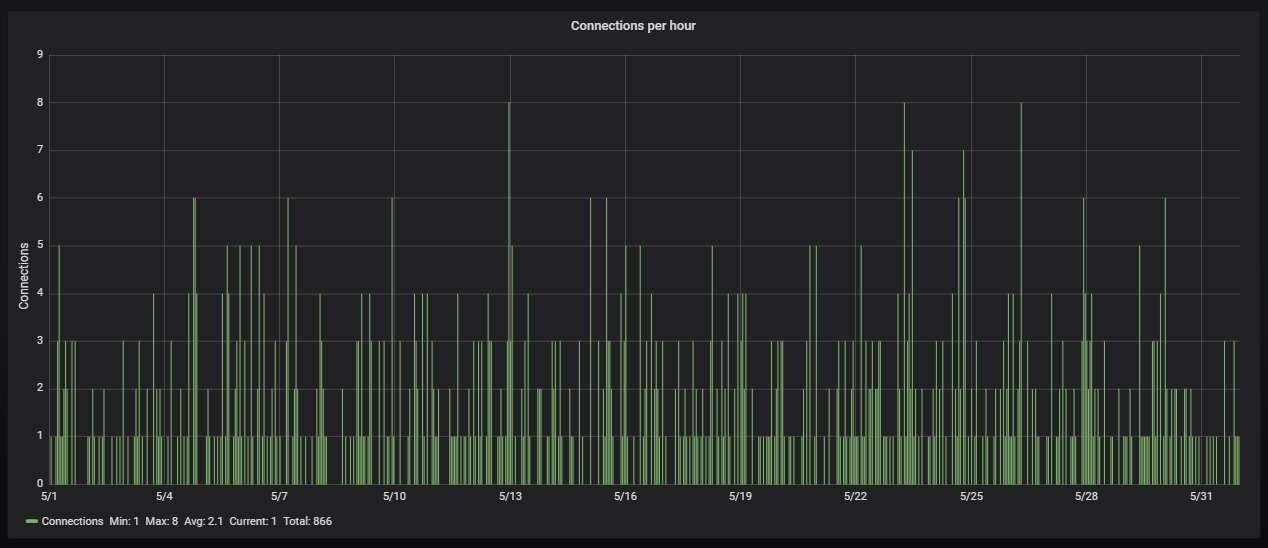
The hourly connection data, showing averagely slightly more than one attack every half an hour:
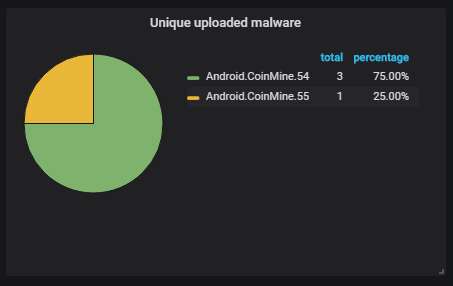
The unique malware uploaded to the honeypot, according to Dr. Web's scanner. The same old Monero mining worm (Trinity) that's causing most of the ADB traffic:
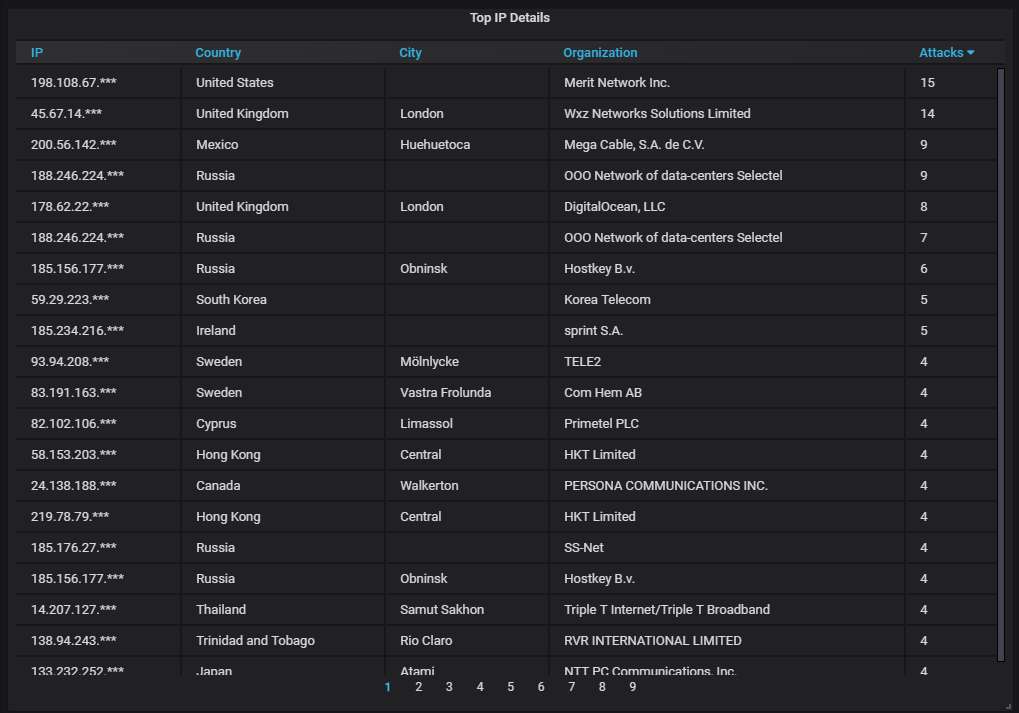
Details about the top-20 most actively attacking IPs. Nothing unusual here:
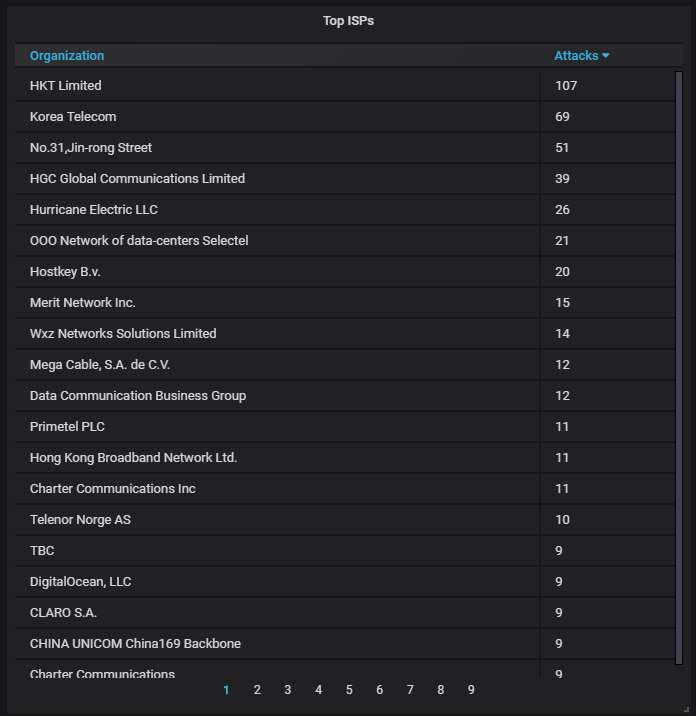
The top-20 organizations that own the IP addresses attacking us:
This concludes the May honeypot report.
