January honeypot report
OK, the month of January is over, so it's time for my monthly report from our honeypots.
We couldn't figure out a fast way to query the database containing our Telnet & SSH honeypot data, but we found another solution.
Basically, I wrote a scrip which, at the end of the month, copies the relevant data for the previous month only into temporary tables. Then I created a new visualization that uses only these temporary tables. 4-mil row tables are easier to handle than 30-mil ones.
So, here is the big picture from our Telnet & SSH honeypot for the month of January. As always, the USA holds the top spot:
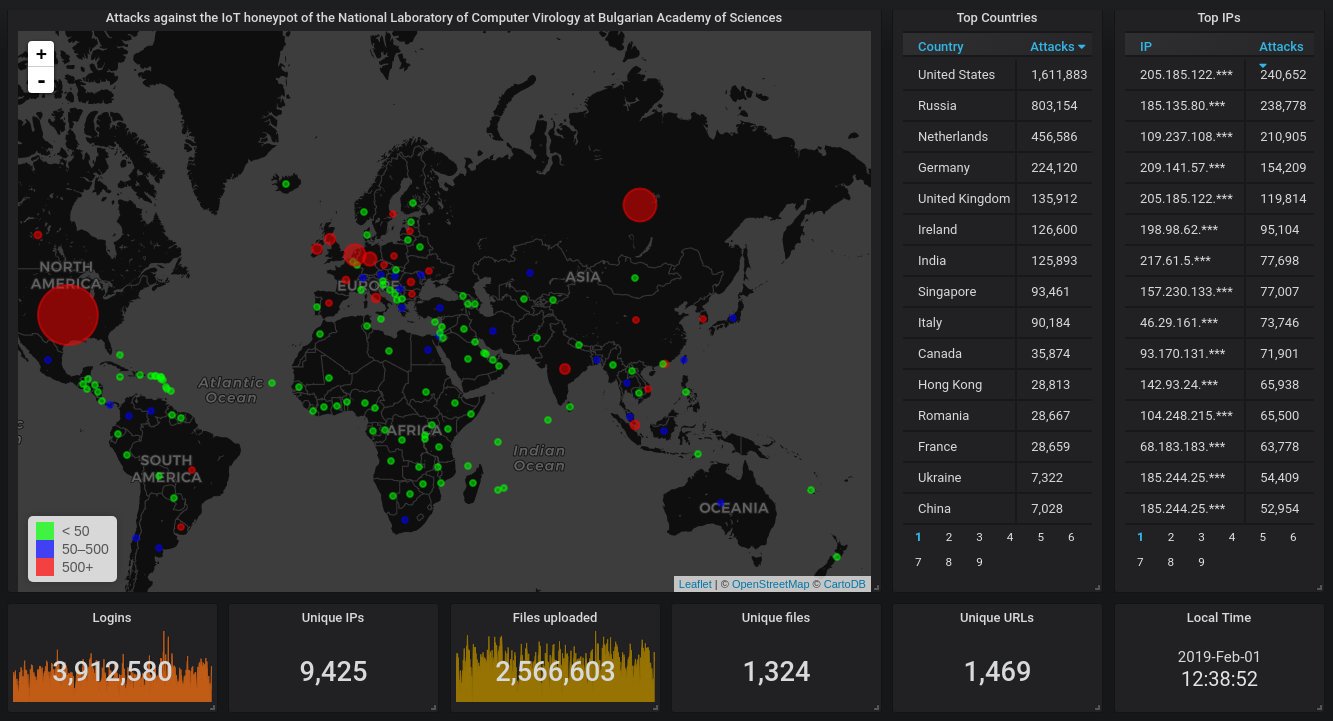
Picture of the hourly activity. We're getting hit averagely 1.6 times per second:
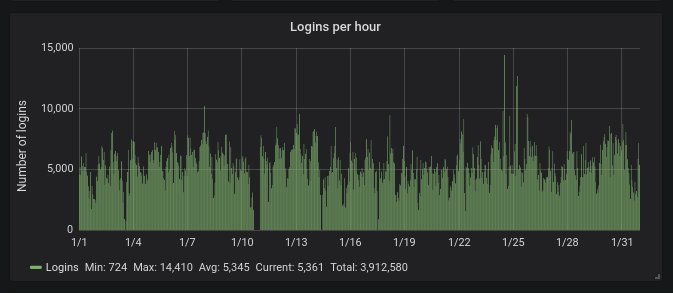
More than 93% of the attacks are via Telnet; the rest is via SSH:
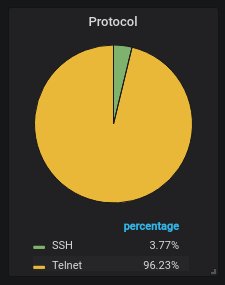
The top URLs from which malware is most often uploaded to the honeypot. Mirai variants all of them, as always:
Details about the top-20 IP addresses that have attacked us the most, in decreasing order of attacks. I'm surprised that DigitalOcean isn't at the top. That dubious honor belongs to FranTech, another often-abused cloud provider.
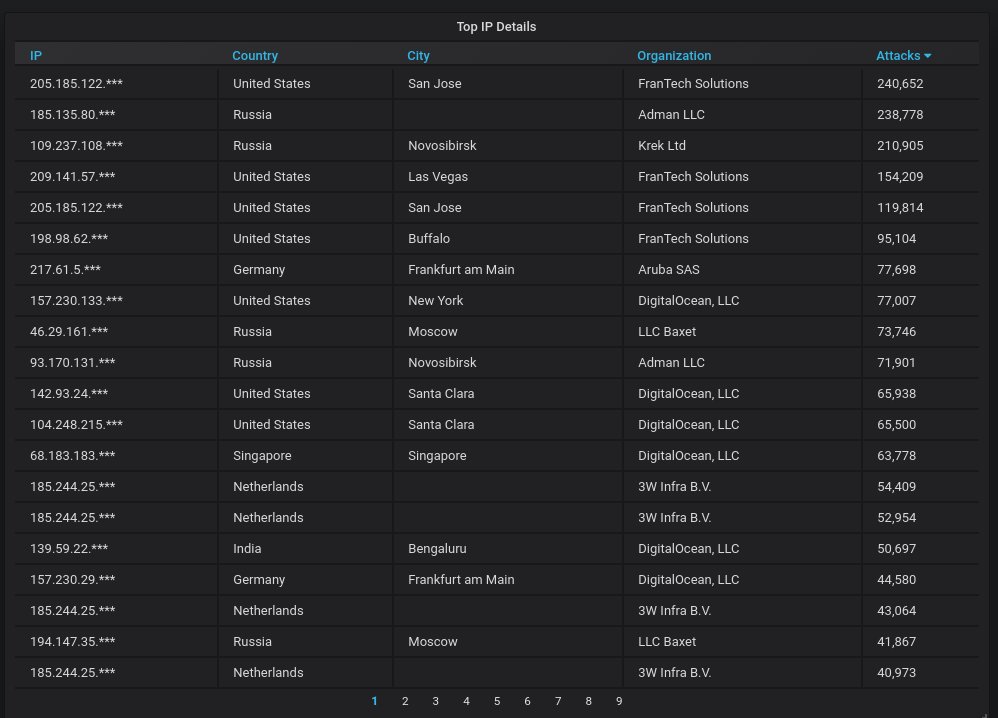
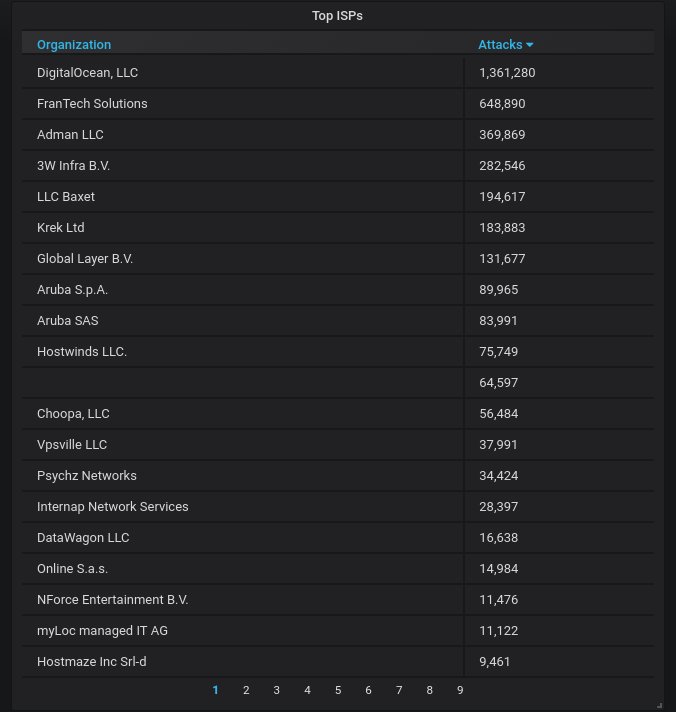
Details about the top-20 organizations that own the most actively attacking IPs. No surprises here - DigitalOcean and FranTech hold the top spots, with everybody else far behind.
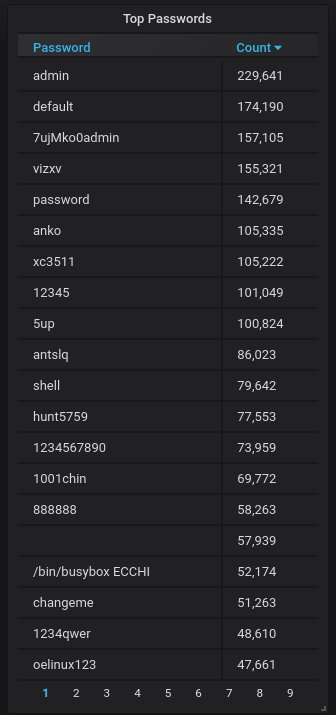
Finally, the top-20 most often used passwords when trying to break into the honeypot. Again, nothing particularly unusual here.
Next, the report from our SMB honeypot, starting with the big picture. The top spot this month belongs to the Netherlands instead of Russia, as is usually the case.
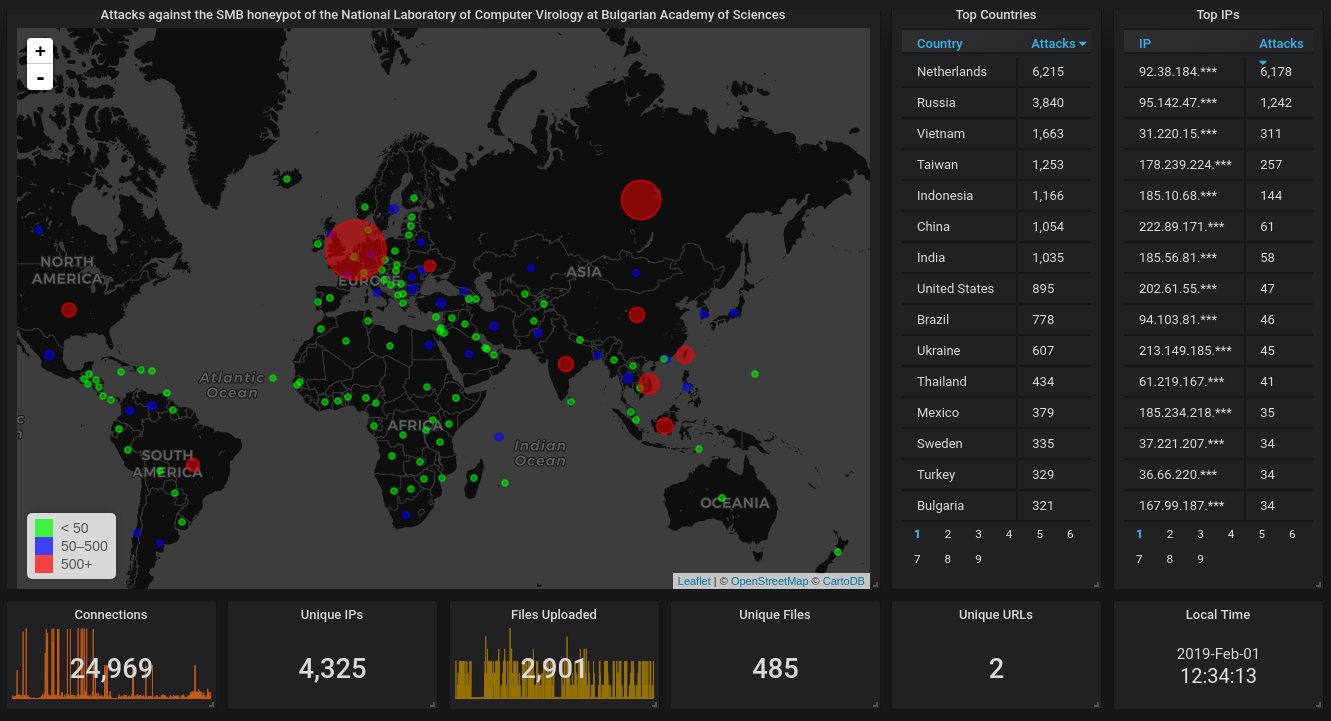
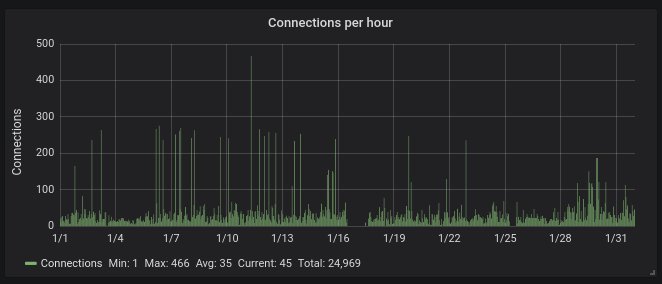
Next, hourly activity. Averagely one hit every couple of minutes. The spikes you see on the chart are caused by that bizarre IP in the Netherlands.
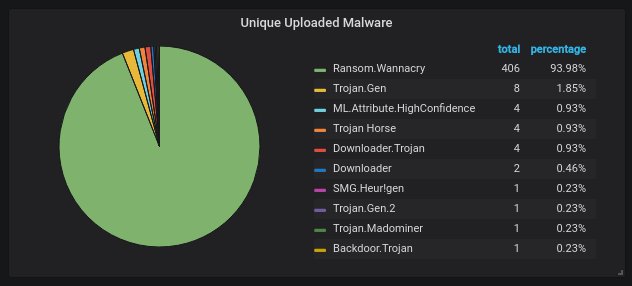
The unique malware variants uploaded, according to Symantec's scanner. 94% are corrupted WannaCry variants (no kill switch check, no encryption), the rest is various crypto miners. No Conficker this month, either.
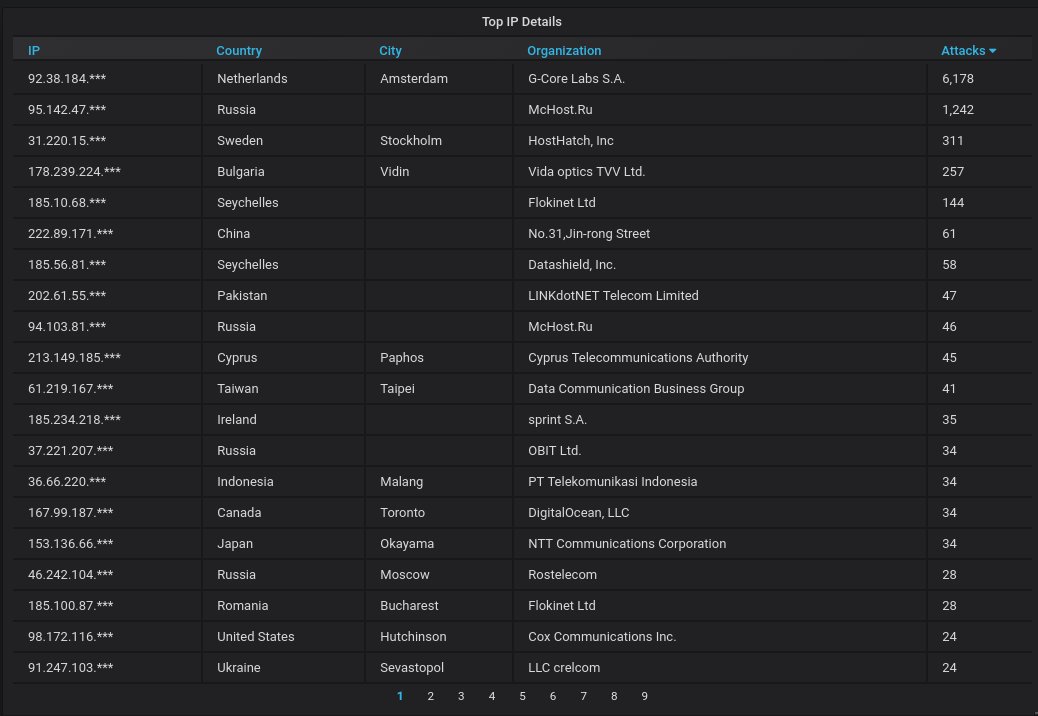
The top-20 most actively attacking IPs. That Dutch IP has the top spot, of course, followed by a Russian one. A Bulgarian one occupies the 4th spot, ugh.
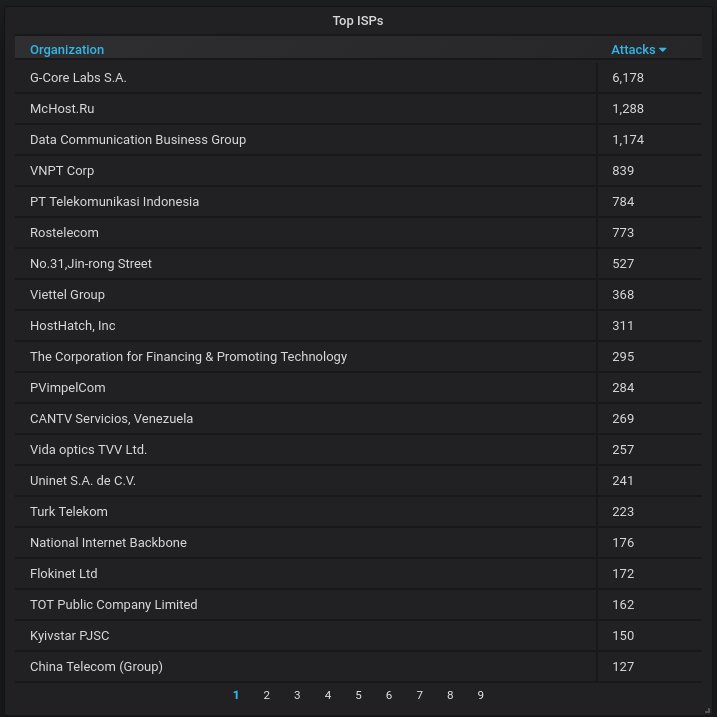
Finally, the top-20 organizations that own the most aggressively attacking IPs. Yep, that Dutch cloud provider has the top spot because of that IP.
Last, the information from our ADB honeypot. Much lower activity there. Starting with the big picture, China and Hong-Kong hold the top spots, as usual for this protocol:
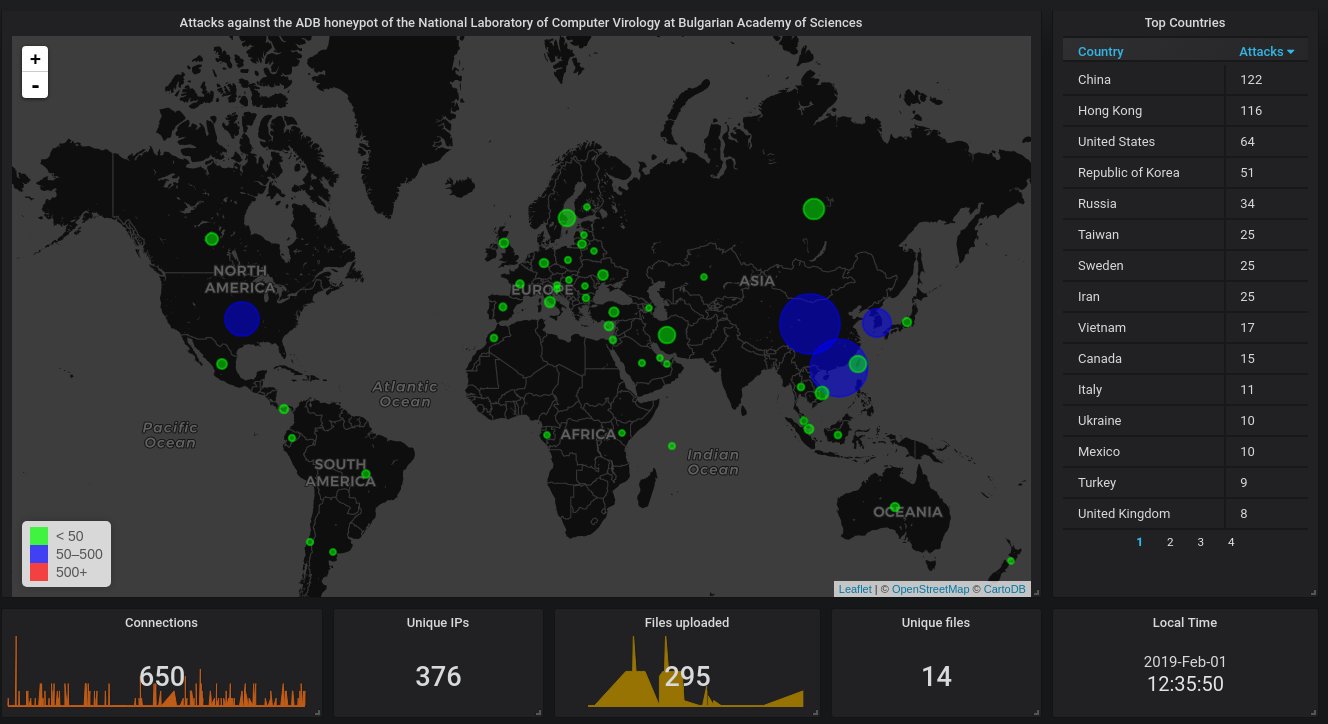
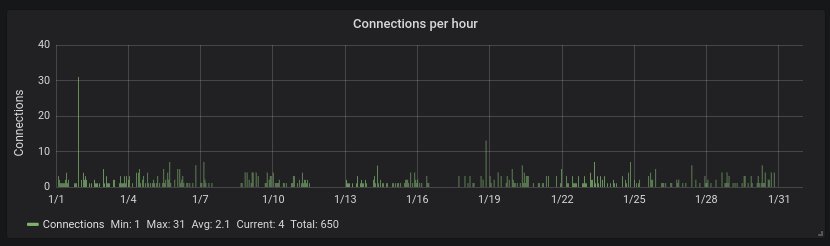
Hourly activity. We're hit averagely once every half an hour.
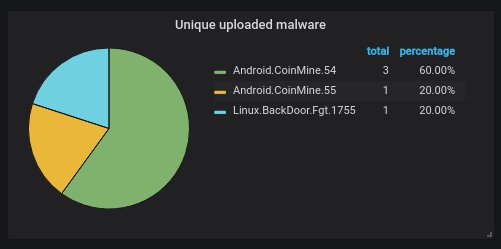
Unique malware variants uploaded, according to DrWeb's scanner. Basically, the same shit is being uploaded over and over - mostly crypto miners.
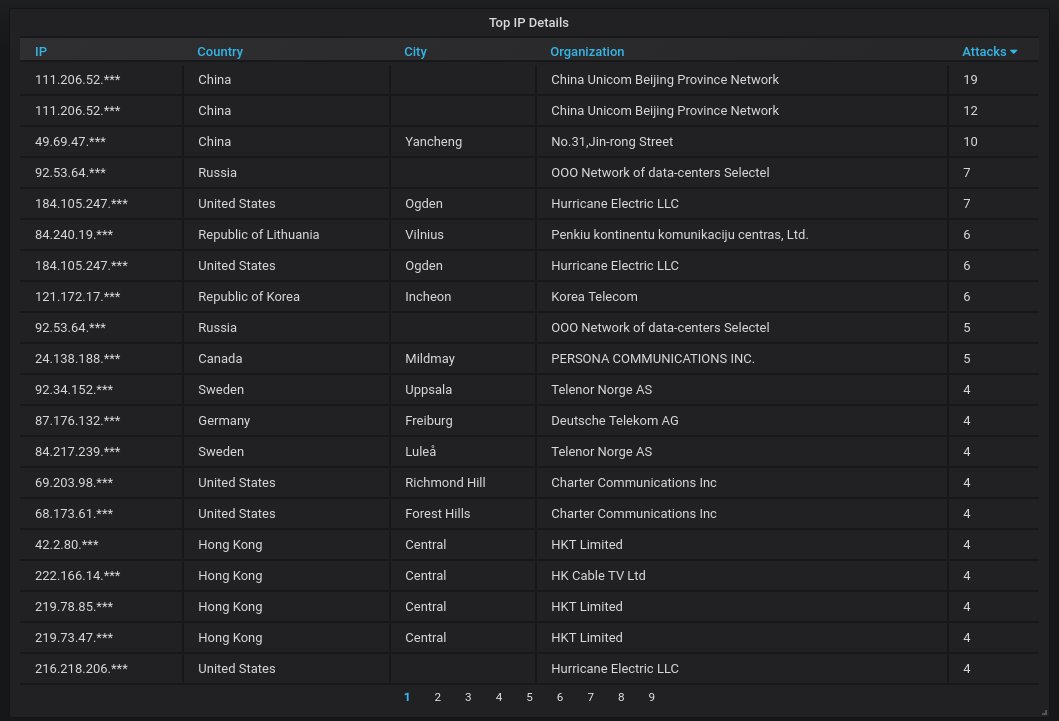
Details about the top-20 most aggressively attacking IPs. Unsurprisingly, most of them reside in China and Hong-Kong.
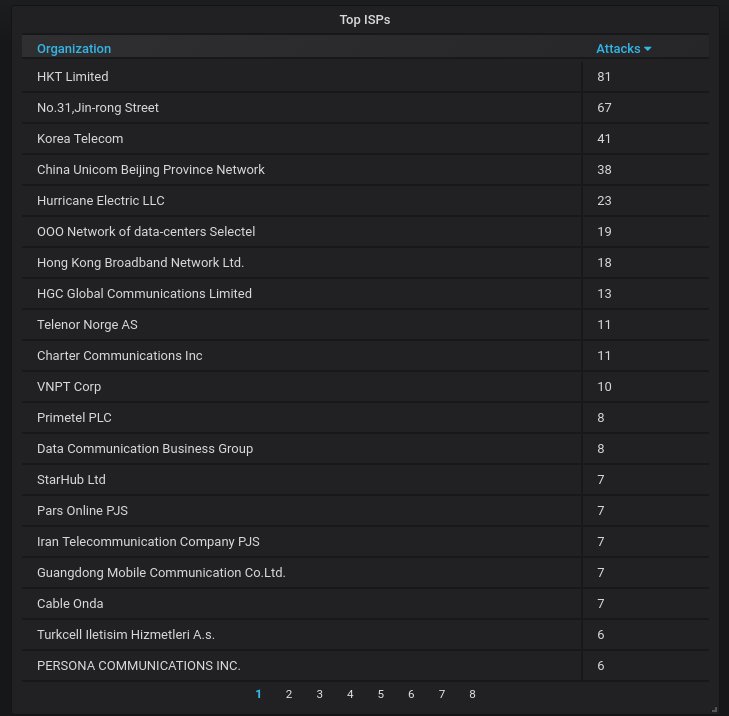
Finally, the top-20 organizations from which most of the attacks are coming from. Chinese ones occupy the top spots.
Wait a sec, Hurricane Electric? Ugh, that's our DNS provider... Wouldn't have expected such stuff from them.
Anyway, this concludes the monthly report.
