February honeypot report
First, the data from our Telnet & SSH honeypot. The big picture looks like this. As usual, most attacks have come from the USA - 3 times more than from the next contender, Germany:
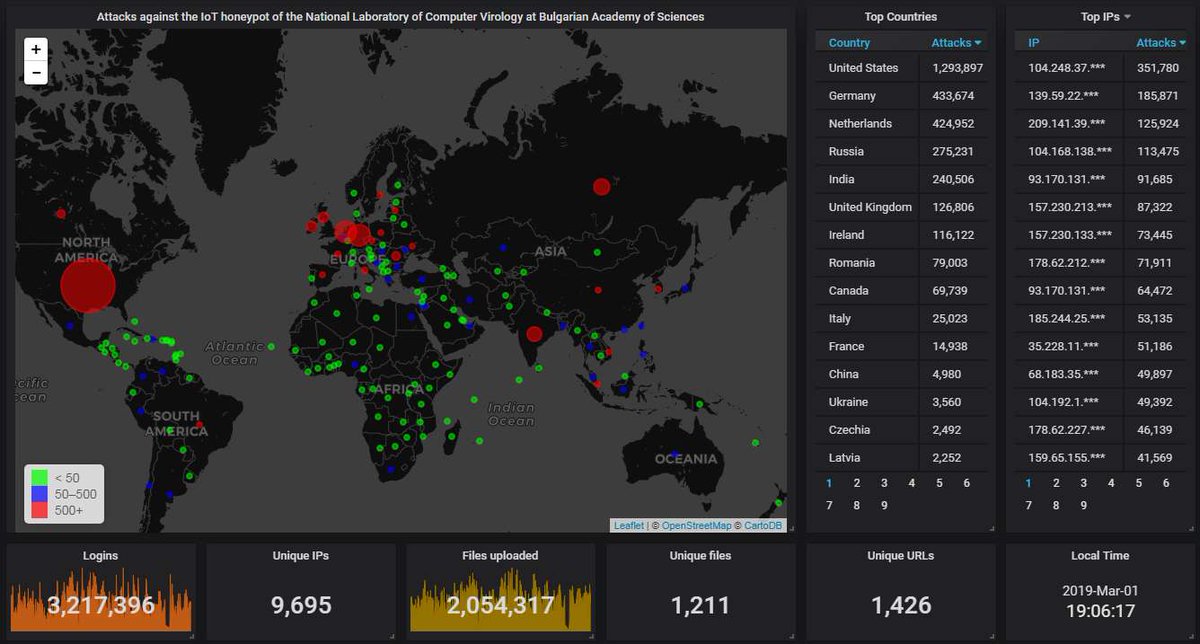
Here is how the hourly activity looks like. Pretty steady traffic, 1.4 attacks per second. The gaps are caused either by maintenance, or because the power has been off, or because of some other mishap preventing the honeypot from working.
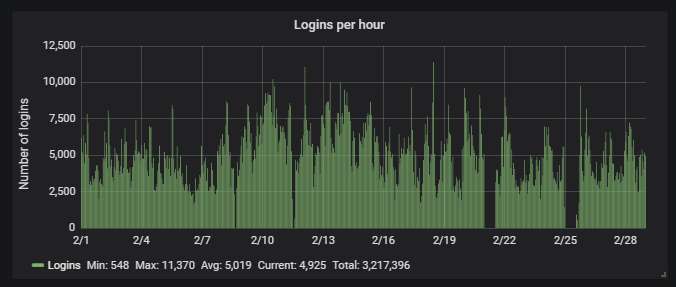
As usual, about 95% of the attacks are via Telnet, the rest are via SSH:
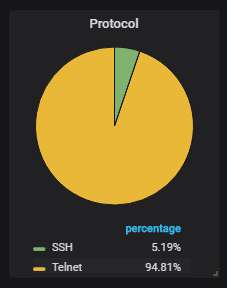
The URLs from which malware was most actively uploaded to the honeypot. Mirai variants all of them, as usual.
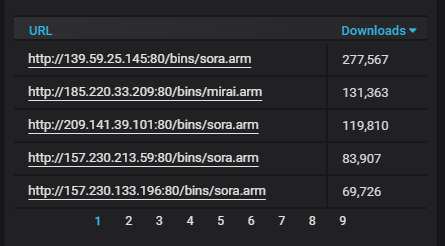
Details about the top-20 most actively attacking IPs. An ocean of DigitalOcean-owned IPs...
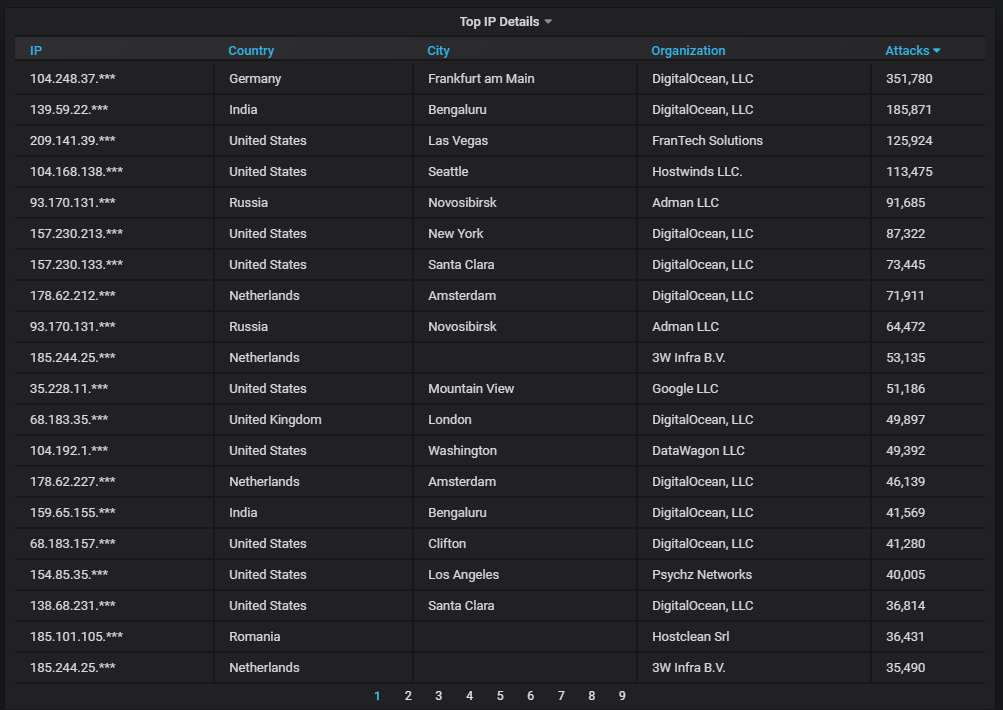
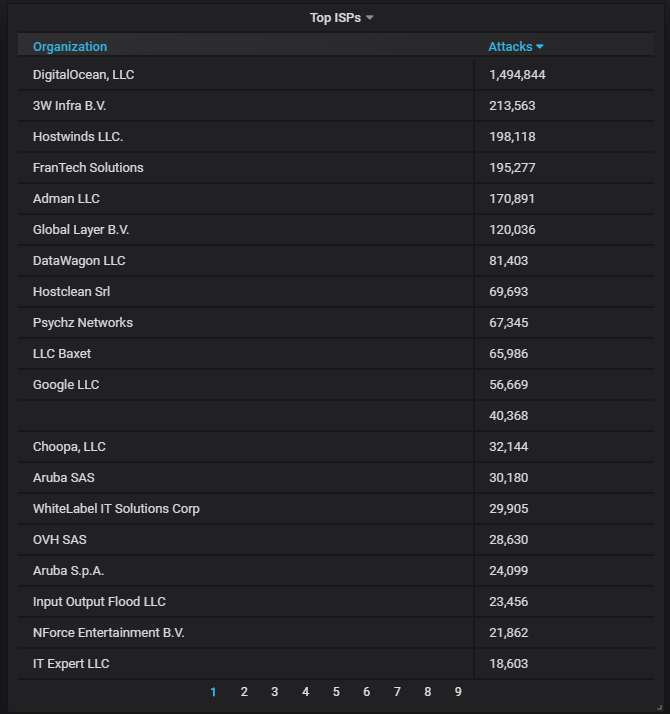
The top-20 most actively attacking organizations. DigitalOcean is at the top, as usual, causing nearly 7 times more attacks than the next contender:
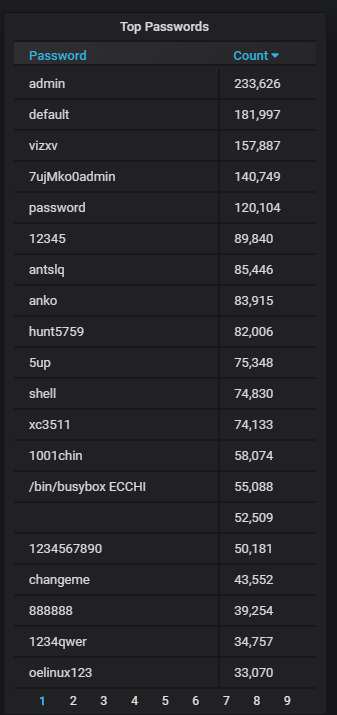
The top-20 passwords that are the most often used by the attackers:
Moving on to our SMB honeypot.
First, the big picture. Here Russia holds to top spot, which is usual, followed by Luxemburg, which is not and is mostly the fault of a single IP there. More about this later.
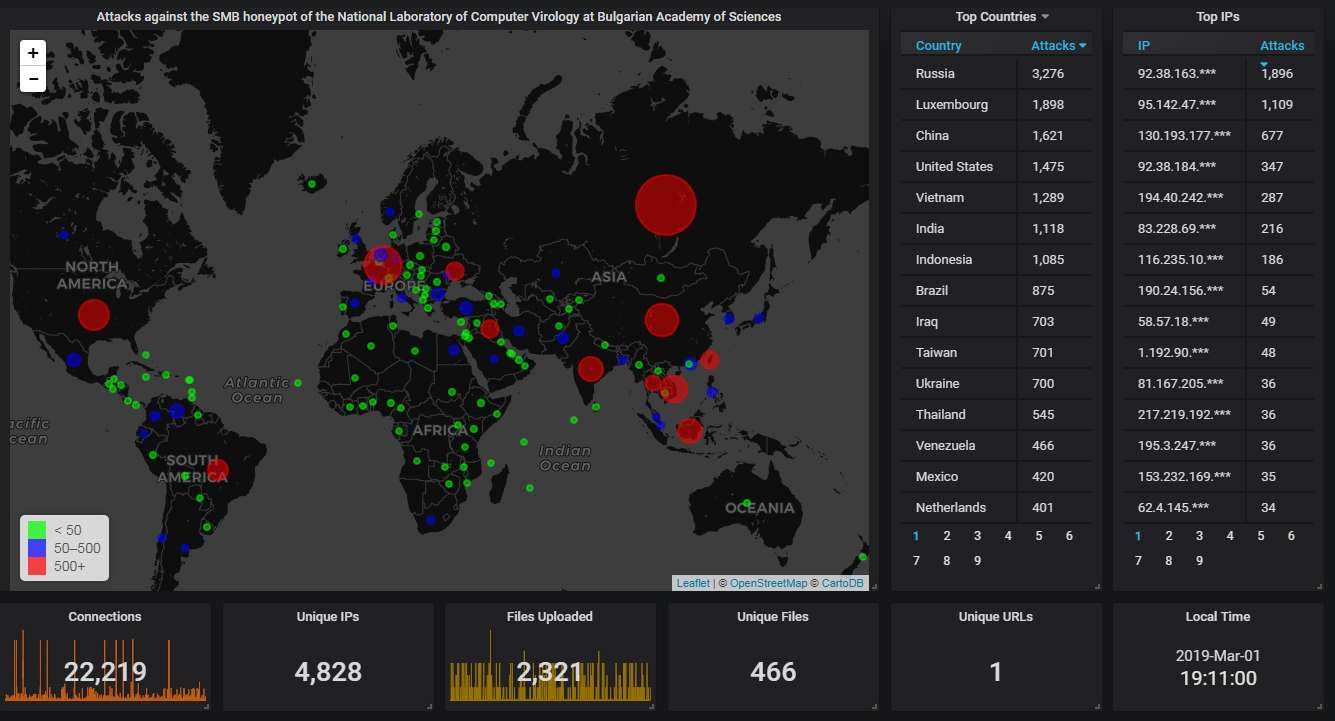
Hourly activity, showing averagely an attack every 2 min. The stand-alone spikes are caused by two mysterious IPs, from the same cloud provider, one in Luxemburg, one in the Netherlands. They don't upload any malware - just cause periodic short-lived flurries of connections.
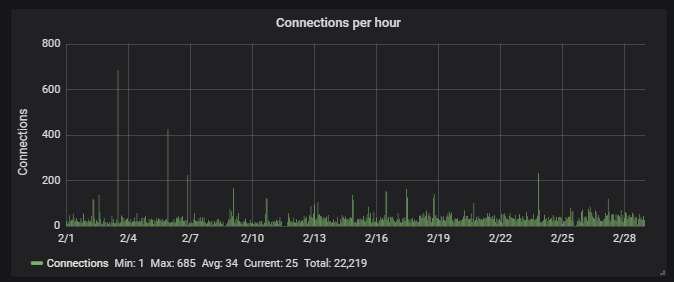
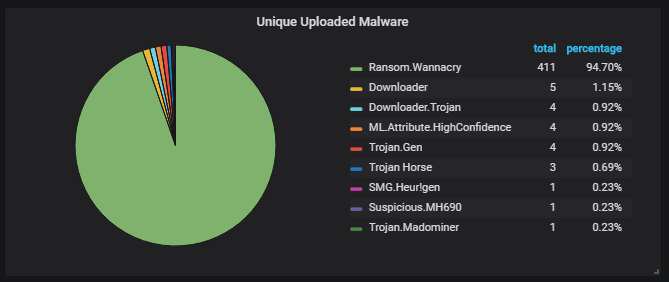
Unique uploaded malware variants, according to Symantec's scanner. Yup, those are 411 different WannaCry variants. All of them have been patched so that they don't check the kill switch. They also don't encrypt because the ransomware part is corrupted.
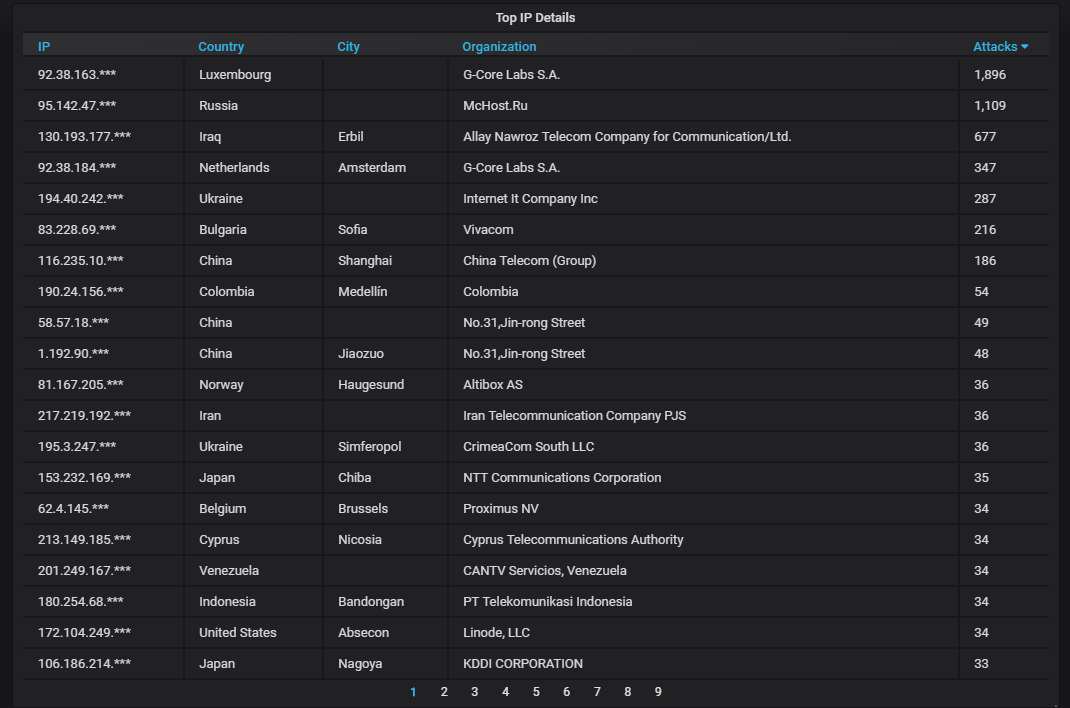
Details about the top-20 most actively attacking IPs. The two mysterious IPs mentioned above both belong to G-Core Labs.
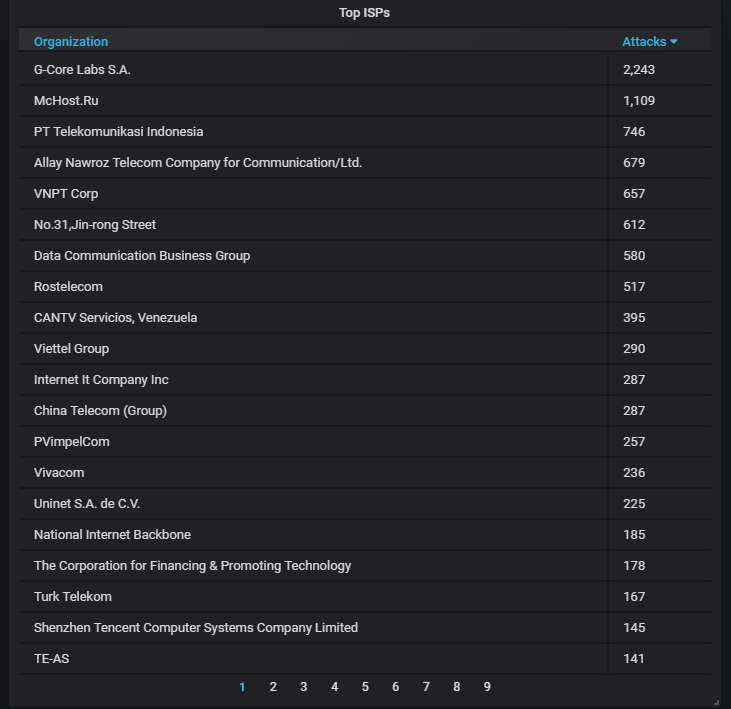
The top-20 organizations from which most of the attacks are coming from. Unsurprisingly, G-Core Labs has the top spot. Ugh, Vivacom (a Bulgarian ISP) made it to the list...
Finally, the data from our ADB honeypot.
The big picture shows Russia at the top spot this time, which is somewhat unusual; normally China dominates the attacks coming via this protocol.
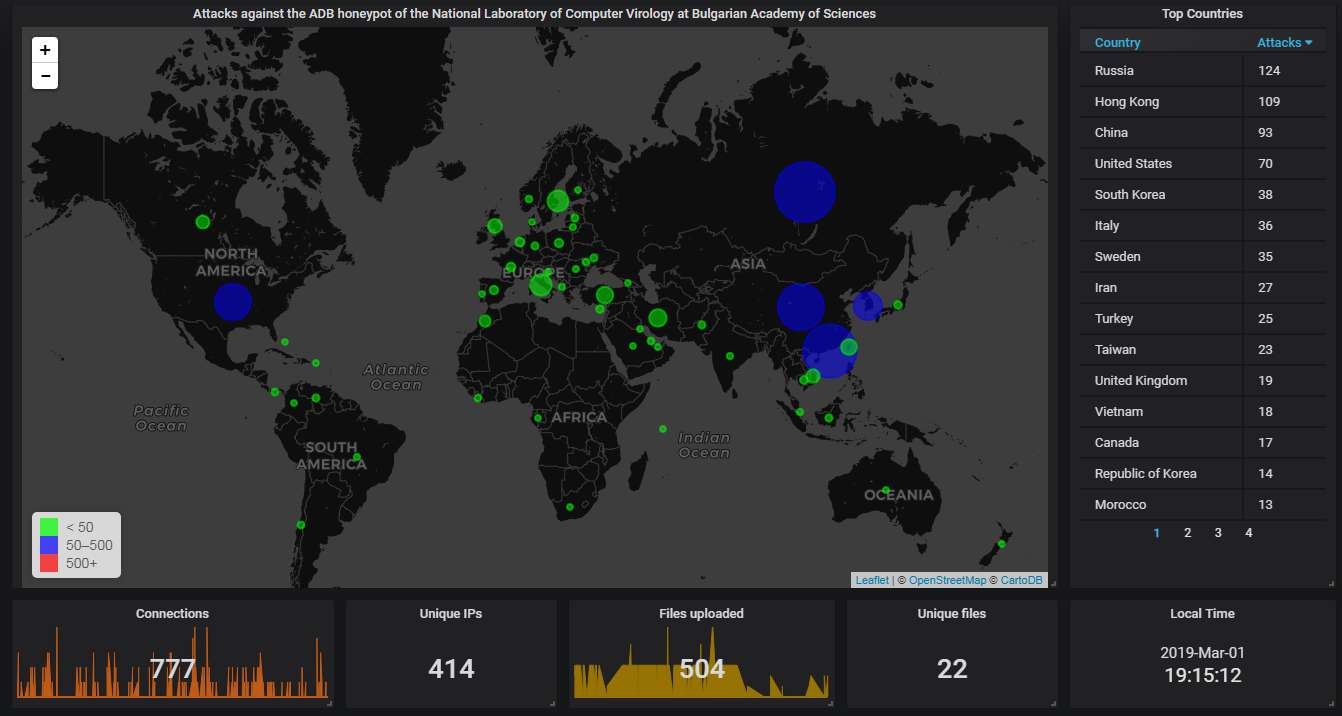
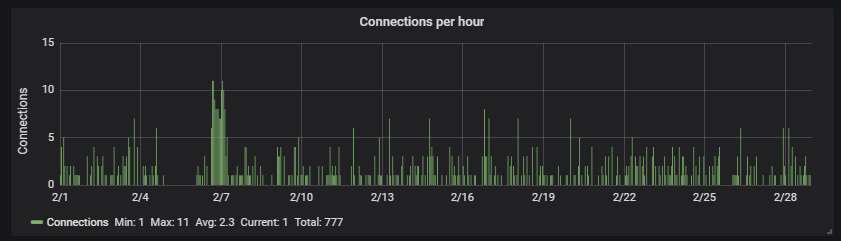
The hourly connection data, showing averagely one attack every half an hour:
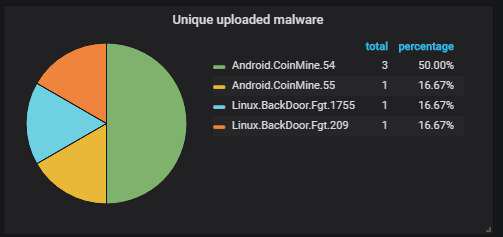
The unique malware uploaded to the honeypot, according to Dr. Web. Pretty much the same shit is being uploaded over and over - miners, plus a couple of backdoors:
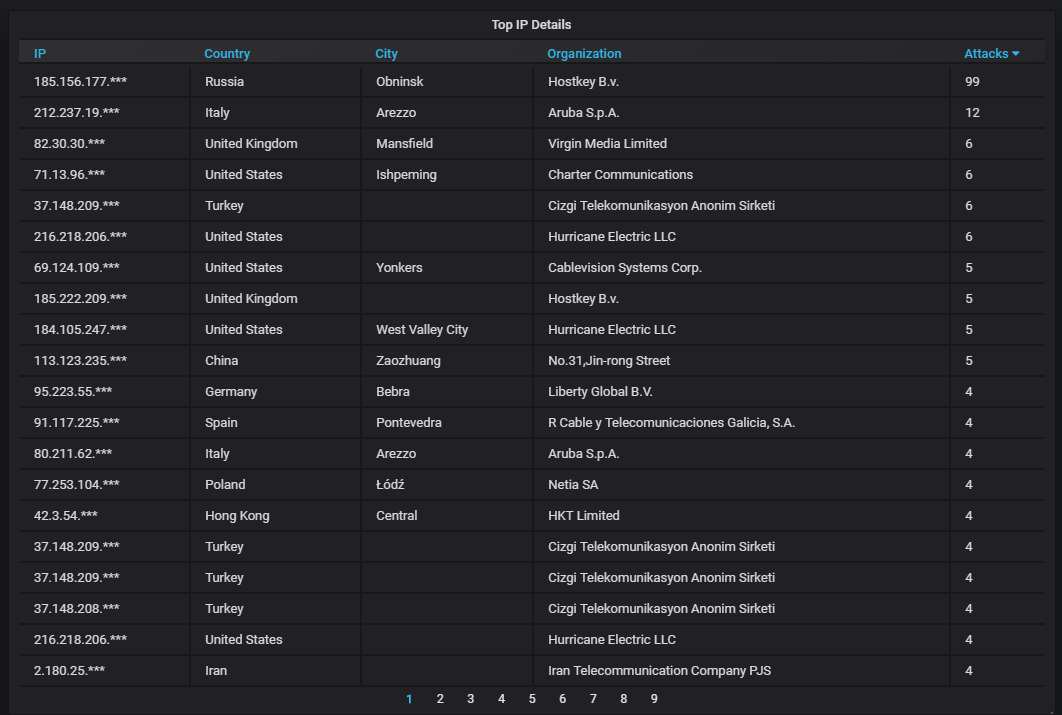
Details about the top-20 most actively attacking IPs. Nothing unusual here.
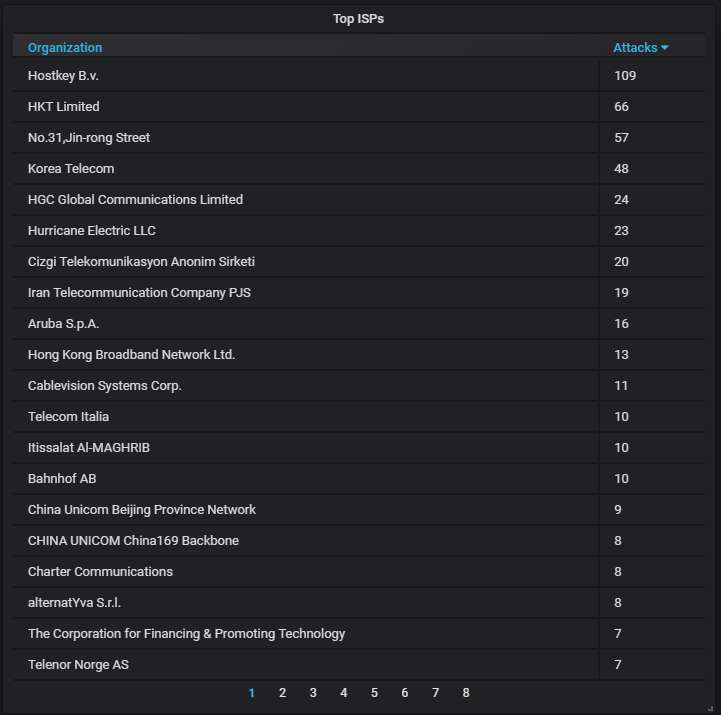
The top-20 organizations that own the IP addresses attacking us. Again, nothing special.
This concludes the February honeypot report.
