March honeypot report
First, the data from our Telnet & SSH honeypot. The big picture looks like this. As usual, most attacks have come from the USA - more than twice than from the next contender, the Netherlands:
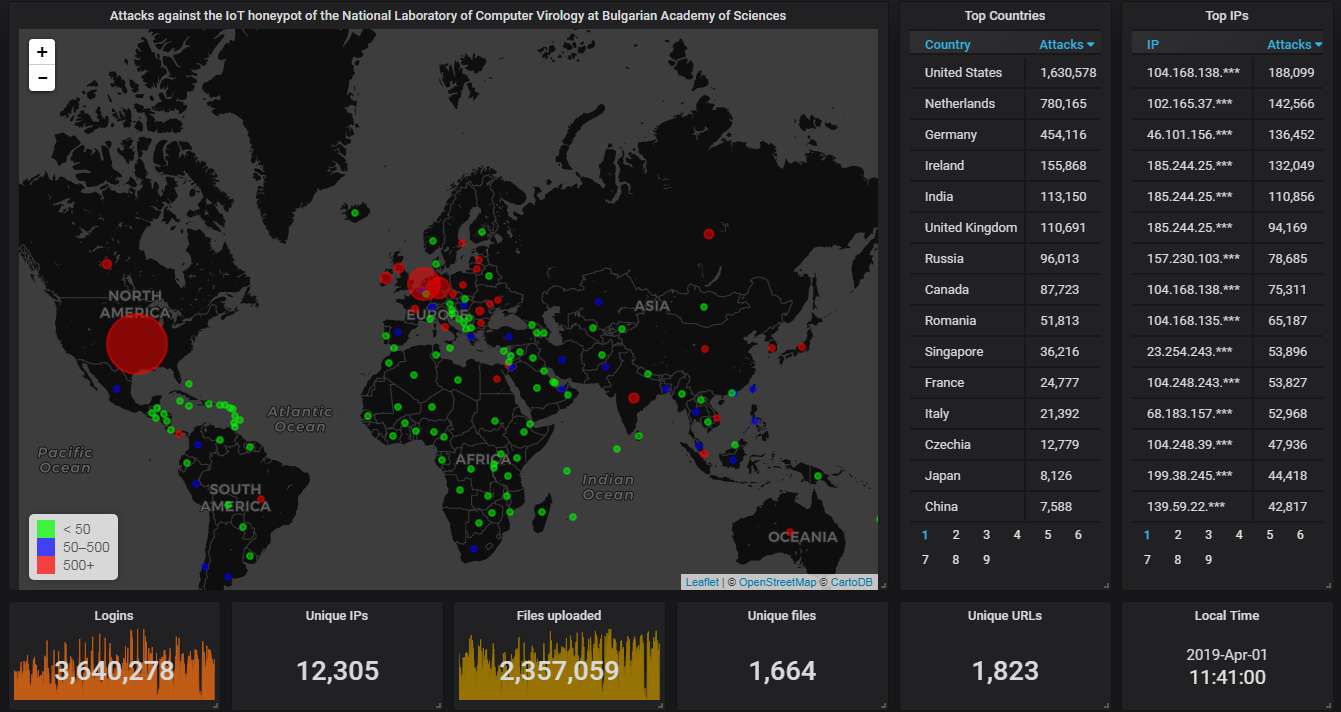
Here is how the hourly activity looks like. Pretty steady traffic, nearly 1.4 attacks per second. The gaps are caused either by maintenance, or because the power has been off, or because of some other mishap preventing the honeypot from working.
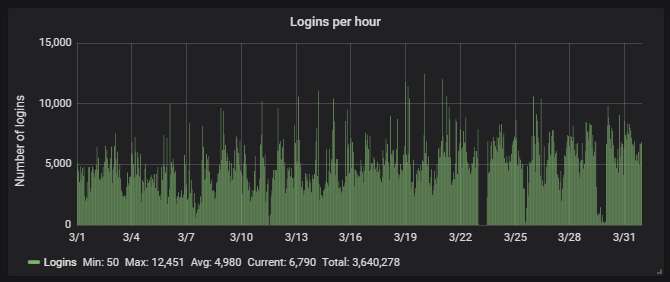
As usual, about 94% of the attacks are via Telnet, the rest are via SSH:
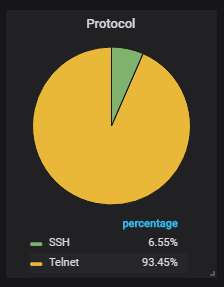
The top-5 URLs from which malware was most actively uploaded to the honeypot. Mirai variants all of them, as usual, although the original variant is not among them.
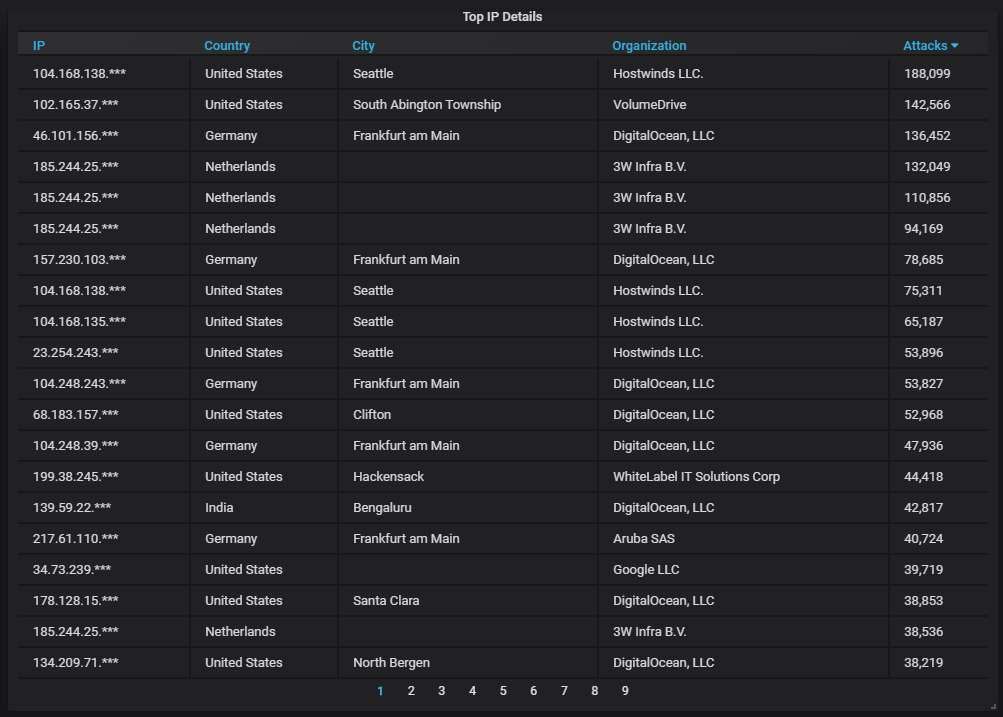
Details about the top-20 most actively attacking IPs. As usual, DigitalOcean is heavily present. Hostwinds is a hoster I don't remember seeing before. And, of course, a significant number of attacks from a Google-owned IP is the odd curiosity.
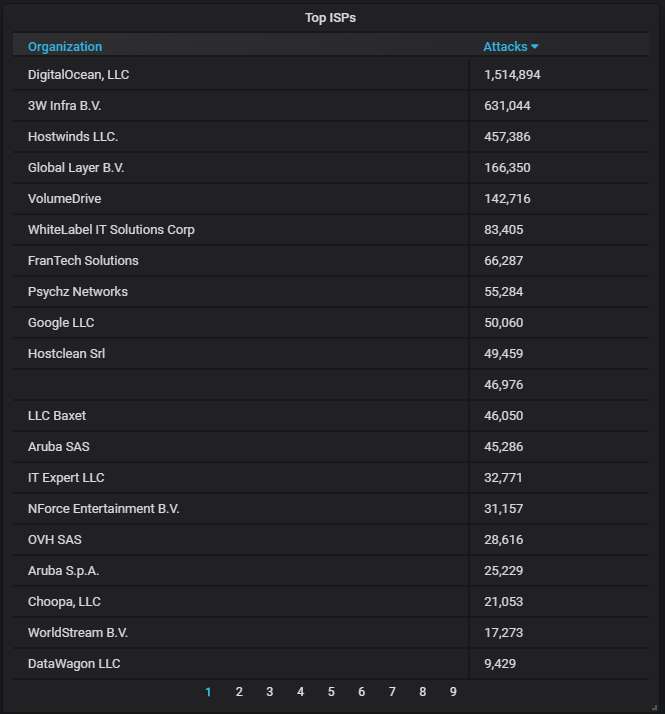
The top-20 most actively attacking organizations. DigitalOcean is at the top, as usual, causing nearly three times more attacks than the next contender:
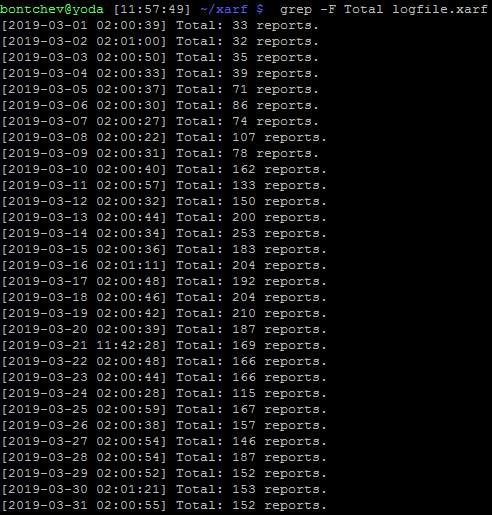
As you can see, I've been sending 100-200 automated abuse reports to DigitalOcean every day - but it doesn't seem to be helping very much:
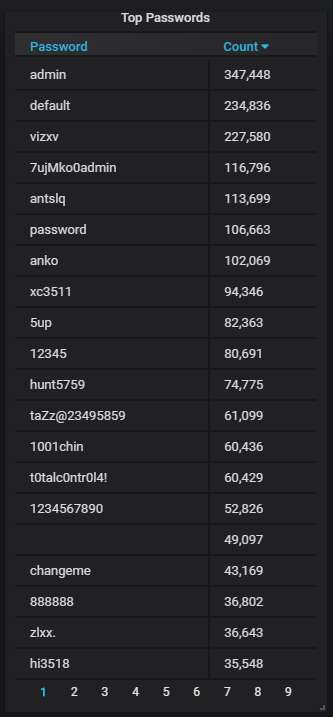
The top-20 passwords that are the most often used by the attackers; nothing unusual here:
Moving on to our SMB honeypot.
First, the big picture. Here Hong Kong holds to top spot, overtaking Russia from the last month, followed by the USA, which is unusual:
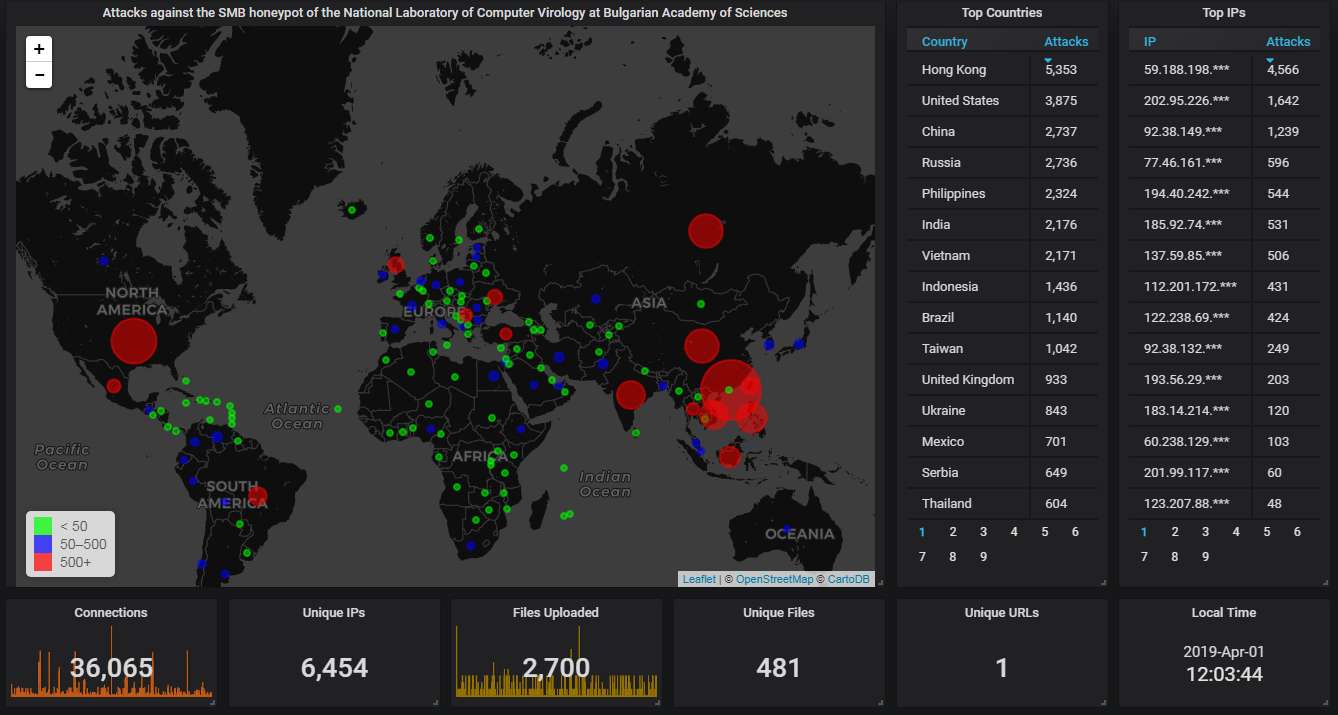
Hourly activity, showing averagely an attack minute. Everything is dominated by a huge spike of 4000+ connections coming from a single IP in Hong Kong on March 5. Maybe I should switch to a log scale on this graph, in order to account for such spikes and prevent them from suppressing the normal traffic chart to the point of making it barely visible.
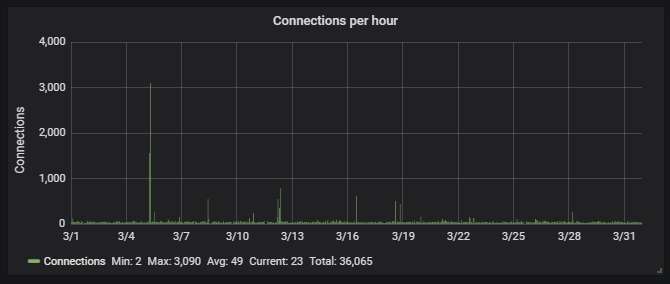
Unique uploaded malware variants, according to Symantec's scanner. Yup, those are 400+ different WannaCry variants. All of them have been patched so that they don't check the kill switch. They also don't encrypt because the ransomware part is corrupted.
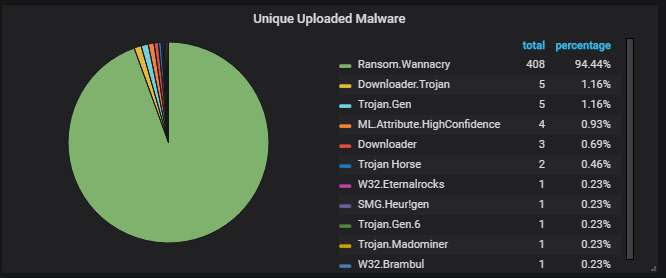
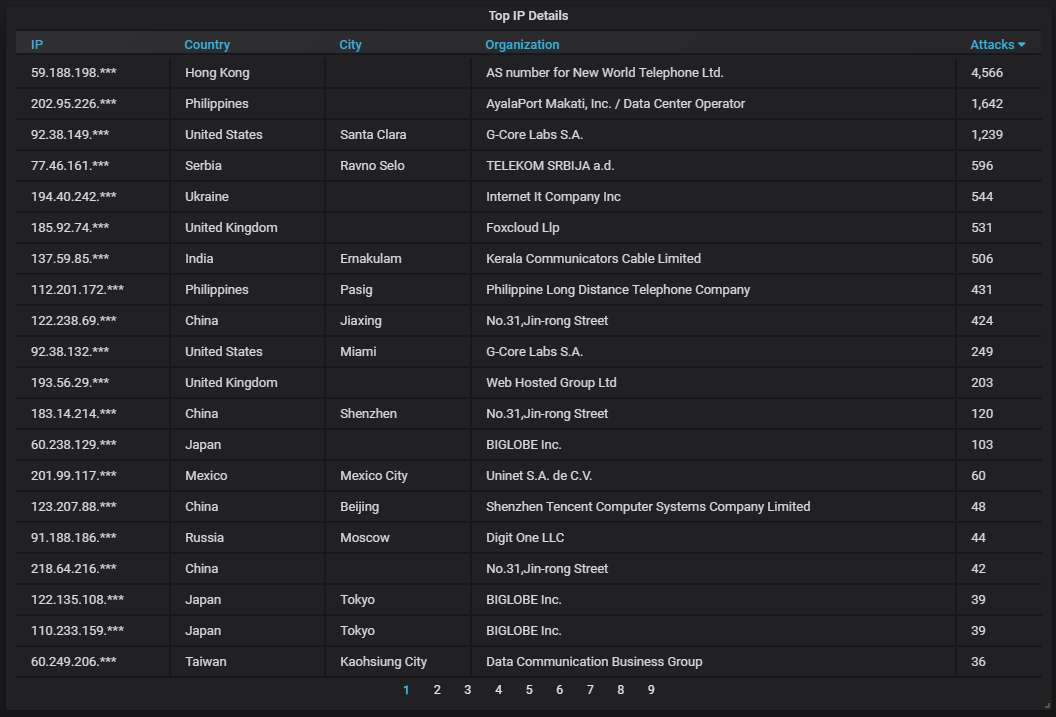
Details about the top-20 most actively attacking IPs. You can see the one from Hong Kong, responsible for the spike on March 5:
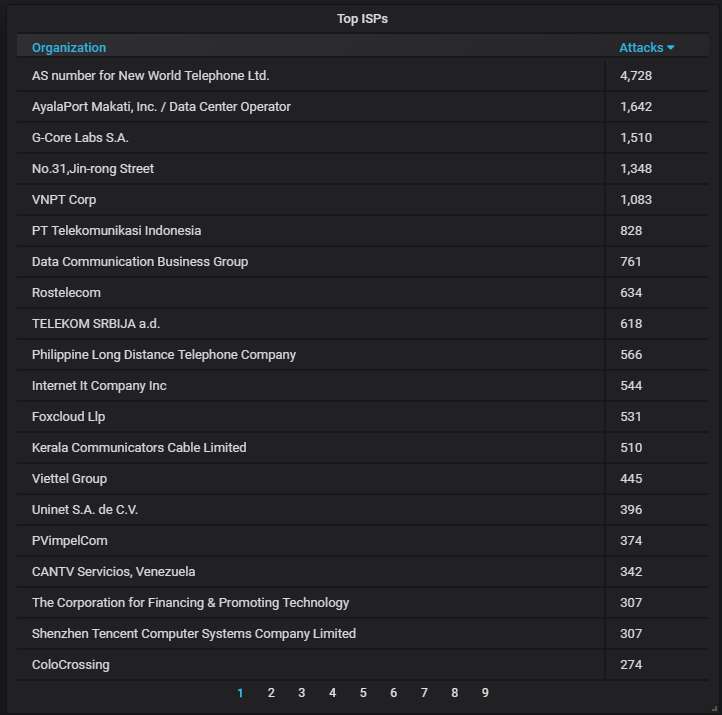
The top-20 organizations from which most of the attacks are coming from:
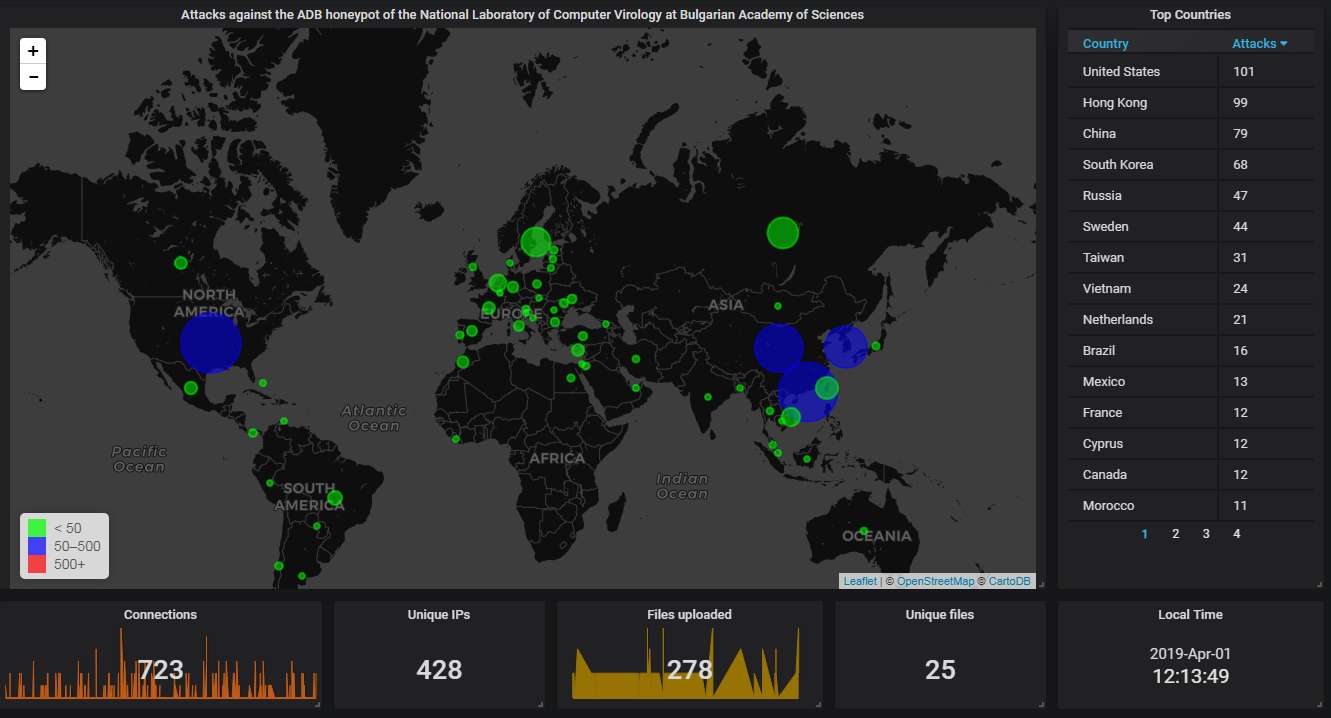
Finally, the data from our ADB honeypot.
The big picture shows the USA at the top spot this time, which is somewhat unusual; normally China, Hong Kong, Korea, and Russia dominate the attacks coming via this protocol:
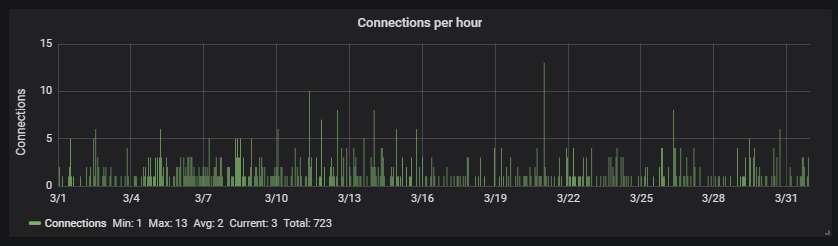
The hourly connection data, showing averagely one attack every half an hour:
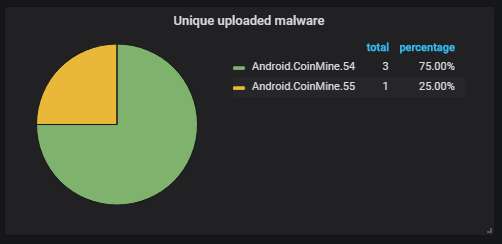
The unique malware uploaded to the honeypot, according to Dr. Web. Pretty much the same shit is being uploaded over and over - the ADB monero mining worm that's causing most of the ADB traffic:
Details about the top-20 most actively attacking IPs:
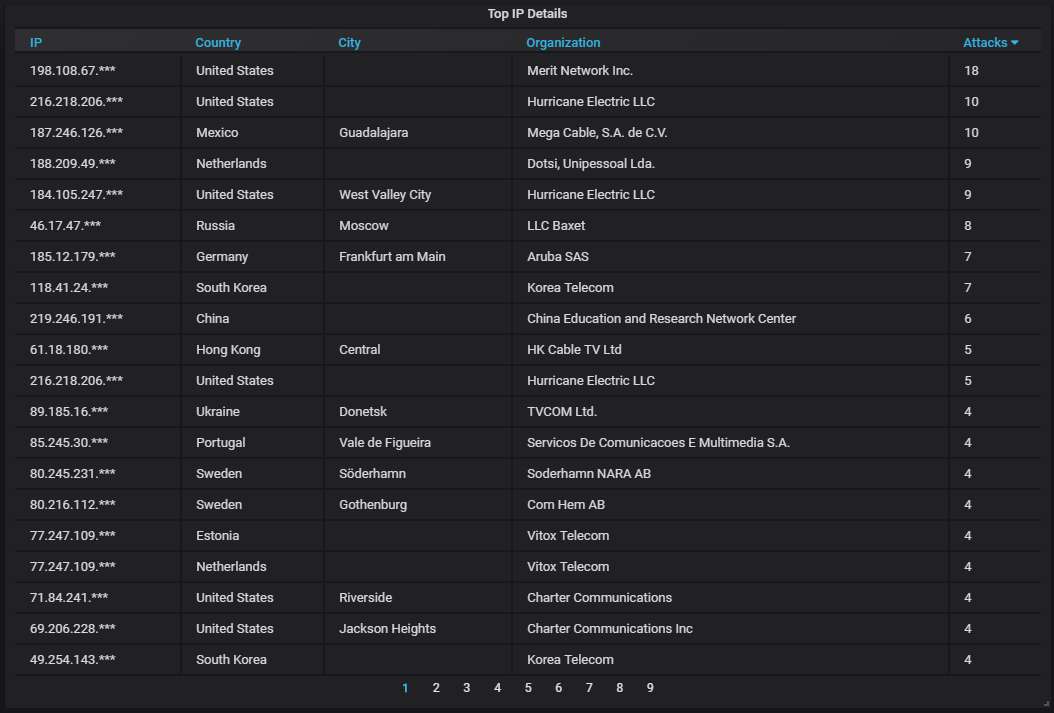
The top-20 organizations that own the IP addresses attacking us:
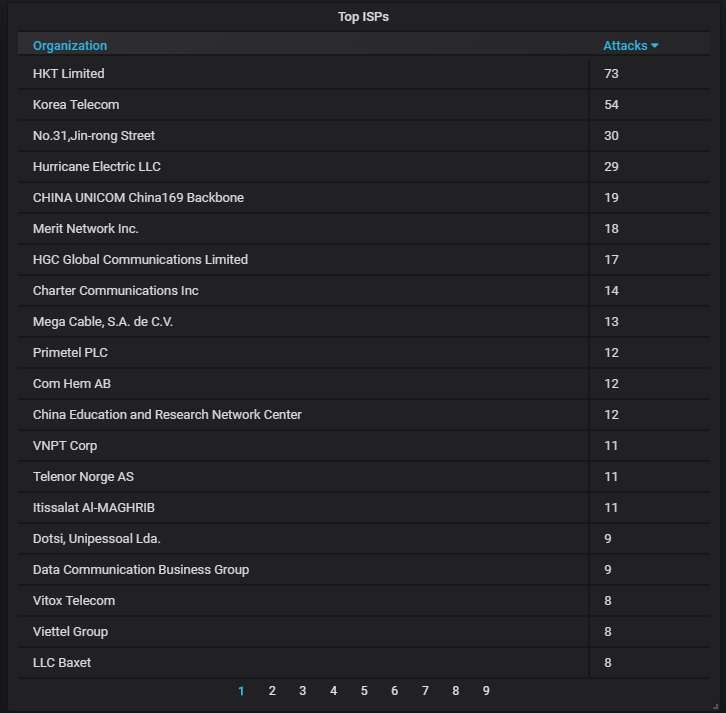
This concludes the March honeypot report.
