November honeypot report
Sorry about the delay of this month's honeypot report but our database is quite full (data going back to 2017 for averagely 2 attacks per second), some tables have 72 million rows, the MySQL server takes forever to execute the queries and the visualization simply times out. I finally figured out how to do it, but make no mistake, this is a temporary solution. The database server simply cannot cope with so much data. I'd have to delete it eventually or even the honeypots will stop working because of the slowdown.
First, the data from our Telnet & SSH honeypot. The big picture looks like this. As usual, most attacks have come from the USA. This time, however, our county (Bulgaria) firmly holds the second place. This is caused by a single infected machine, as you'll see in a moment.
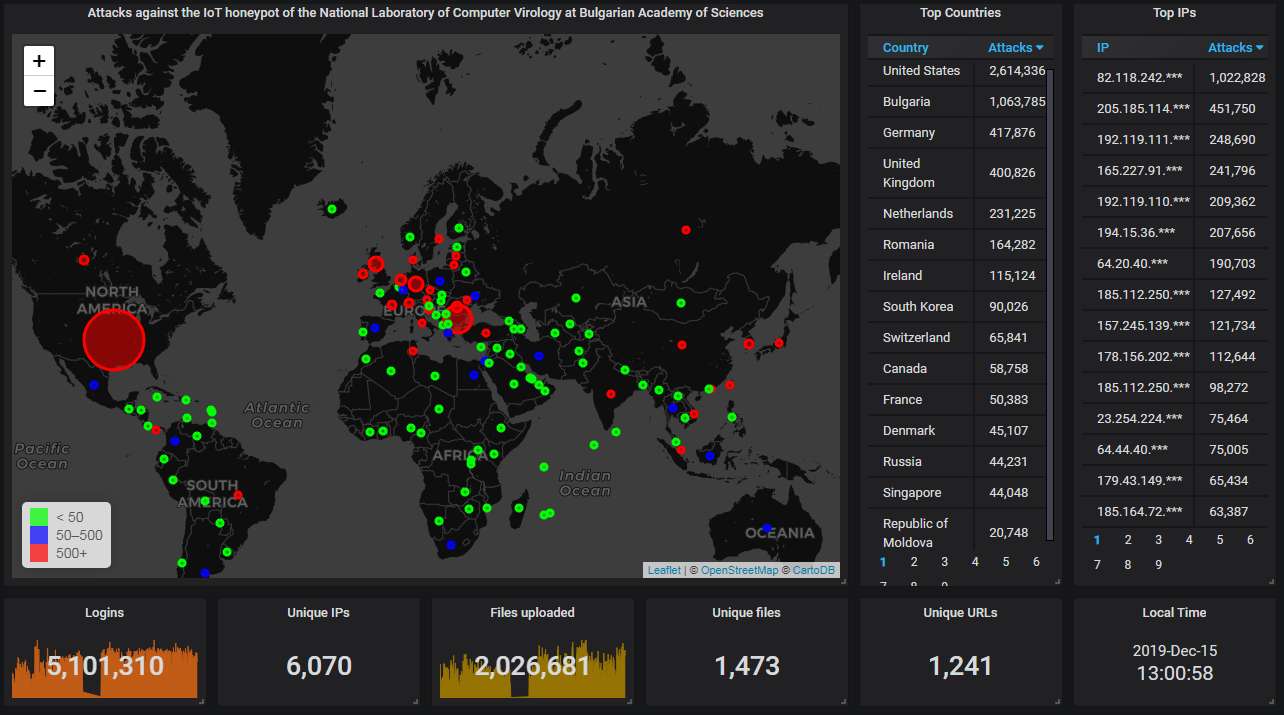
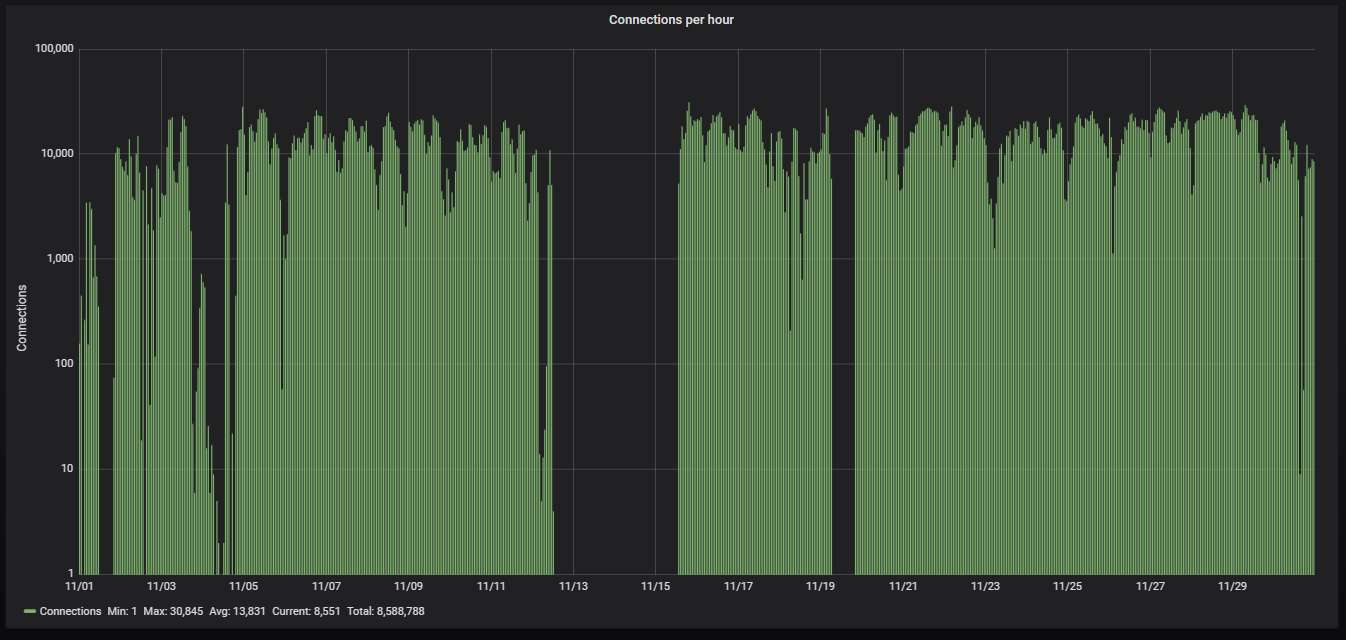
Here is how the hourly activity looks like. The honeypot is being attacked on the average nearly 2.2 times per second. Sorry about the two-day gap; the router that the honeypot machine is connected to decided to hang just when I was attending a conference and there was nobody around to reboot it.
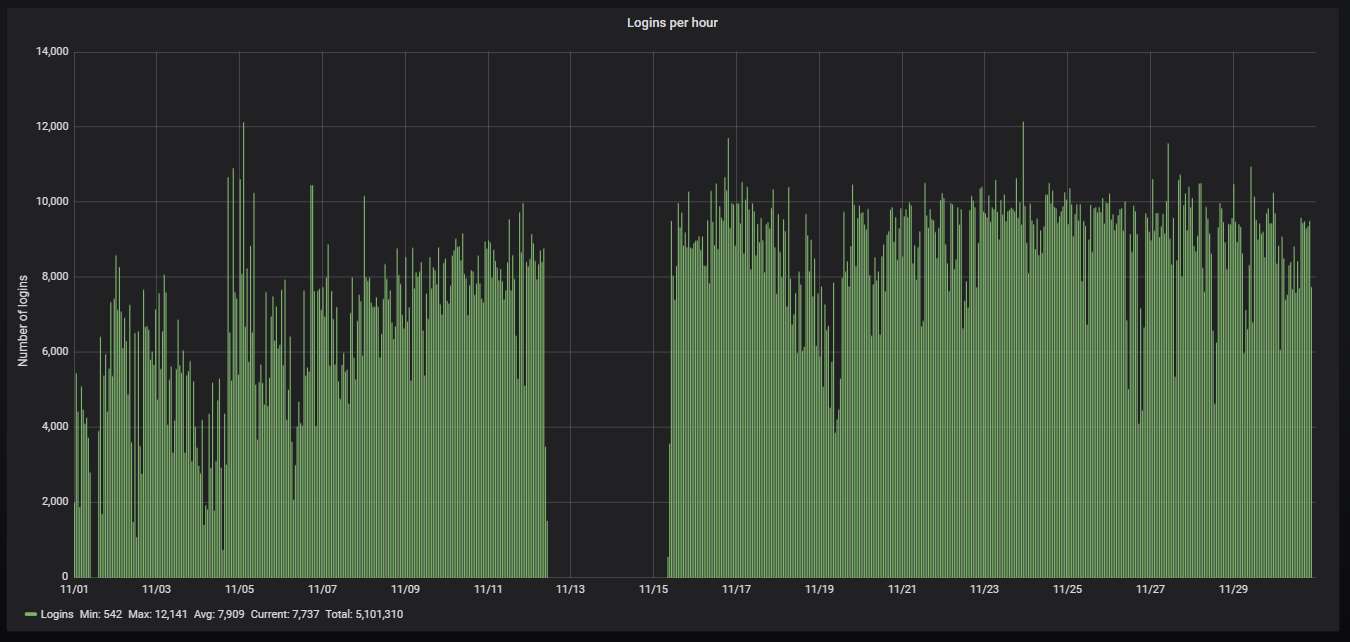
Nearly 96% of the attacks are via Telnet, the rest are via SSH:
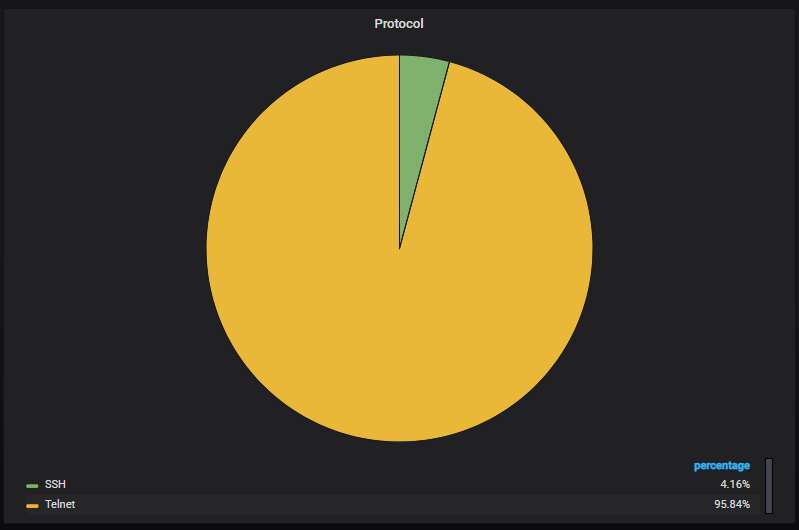
The top-5 URLs from which malware was most actively uploaded to the honeypot. Mirai variants all of them, as usual, although the original variant is not among them.
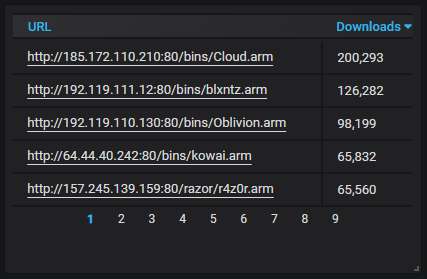
Details about the top-20 most actively attacking IPs. You can see now why Bulgaria is on 2nd place. Almost all of the attacks coming from there are caused by a single IP address, belonging to Verdina Ltd. The company is registered in Belize but this particular machine is hosted in Bulgaria. All attempts to reach them and make them stop the abuse of their resources have failed.
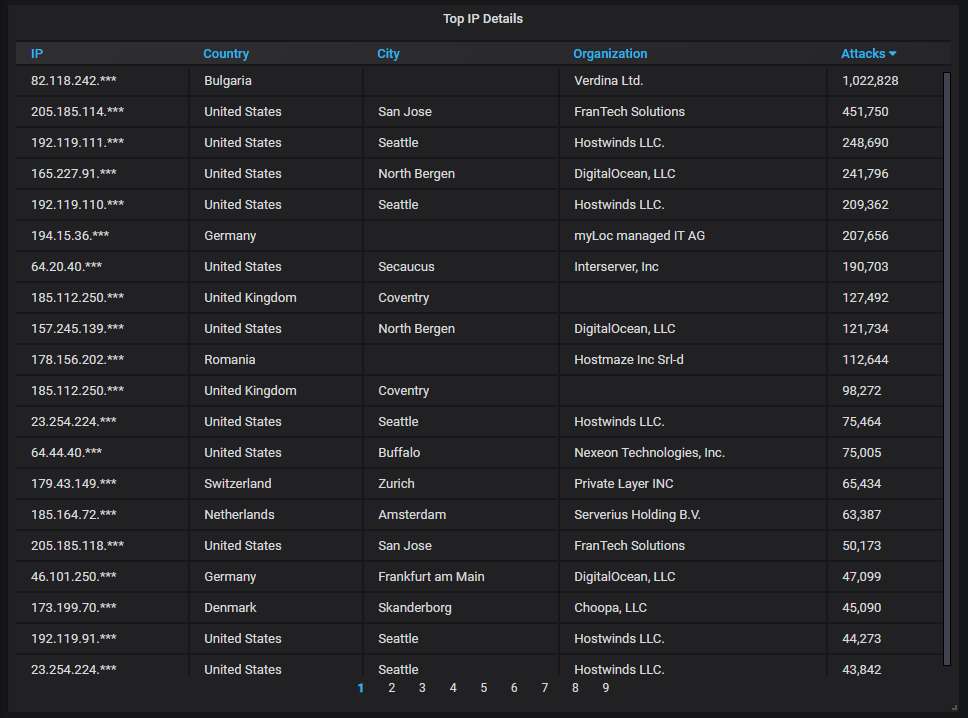
The top-20 most actively attacking organizations. Naturally, Verdina mentioned above occupies the top spot, surpassing even such a serial offender as DigitalOcean.
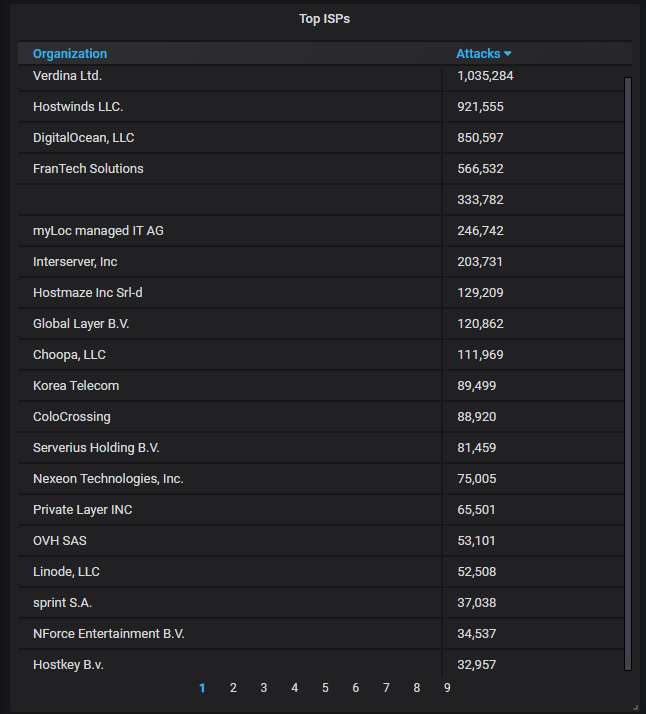
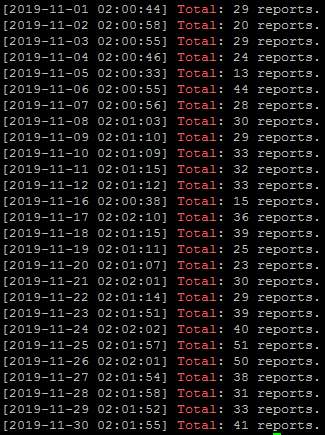
Speaking of DigitalOcean, as you can see, I've been sending them averagely 32 abuse reports every day - but it doesn't seem to be helping very much:
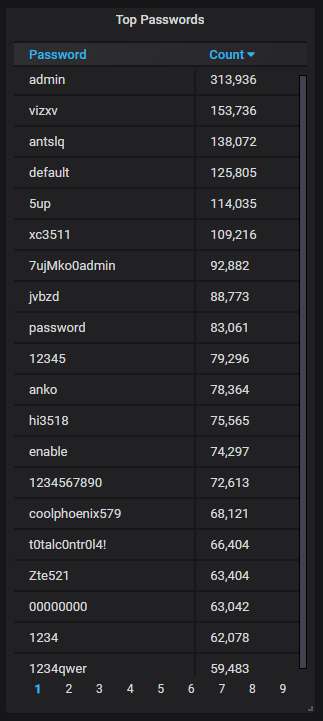
The top-20 passwords that are the most often used by the attackers; nothing unusual here:
Moving on to our SMB honeypot.
First, the big picture. Most of the action is in Russia and Ukraine again, although Vietnam is also well-represented. For the first time, we get more attacks against our SMB honeypot than against our Telnet & SSH honeypot. Most of them are just scans, though - the number of uploaded files is relatively small. It seems that there is a botnet out there that is looking for vulnerable hosts without actually attacking them:
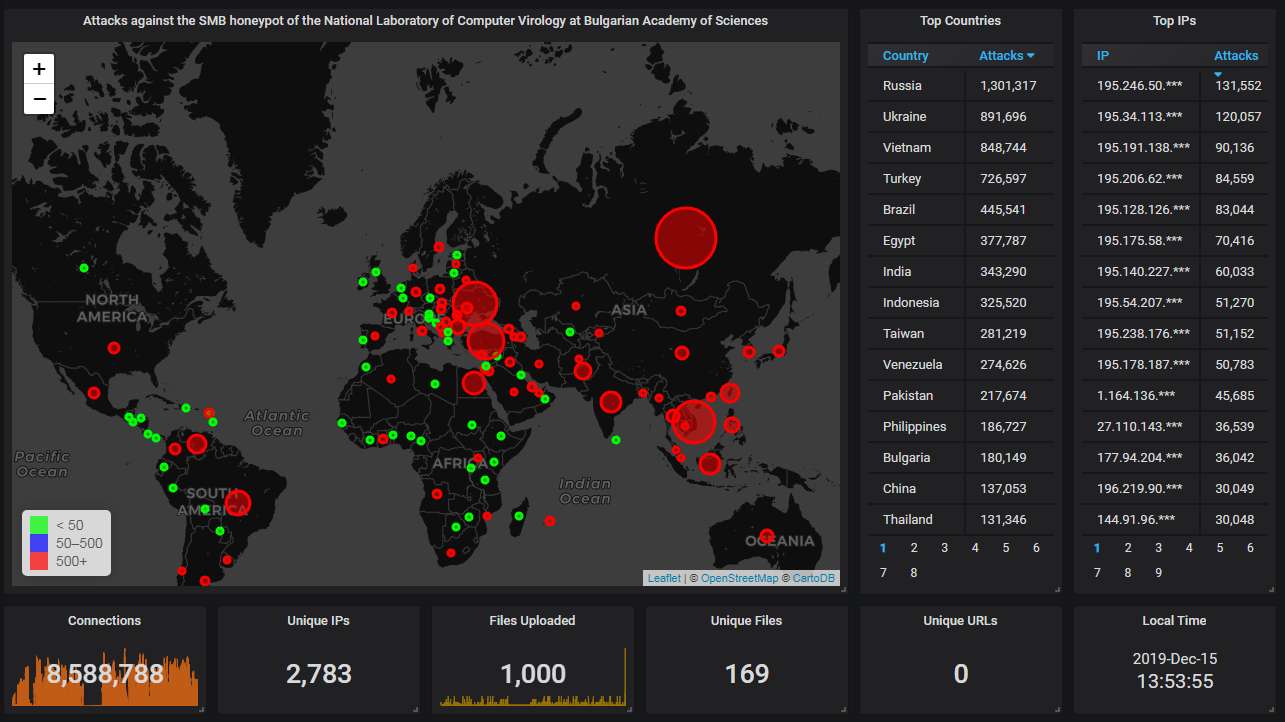
Hourly activity, showing on average more than 3.2 attacks per second. (For comparison, it used to be once per minute in the past.) Again, the big gap was caused by a router failure while nobody was around to fix it, while the small ones are the result of the honeypot being down for maintenance:
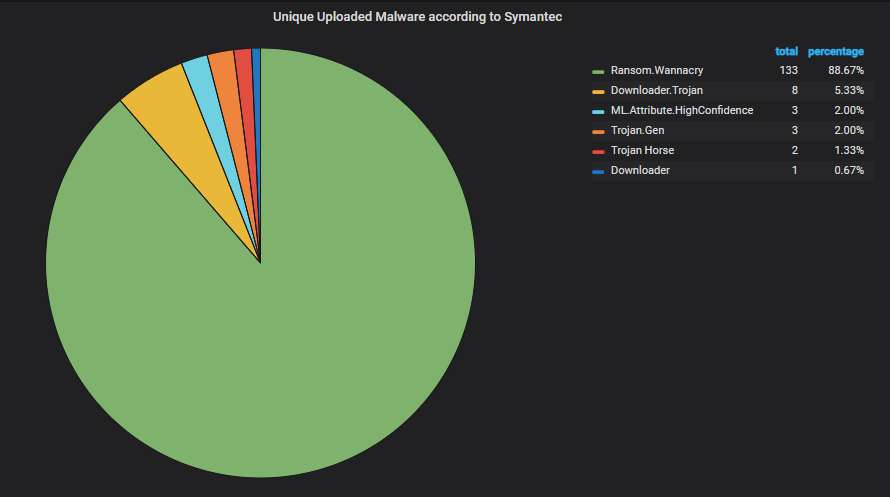
Unique uploaded malware variants, according to Symantec's scanner. Lots of corrupted WannaCry variants, as usual (no kill switch check, no encryption).
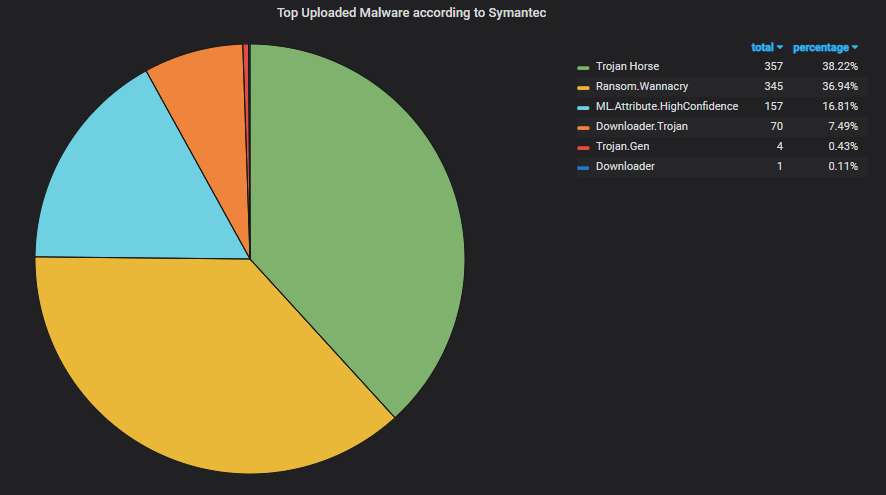
Even if we don't count only the unique variants, the WannaCry samples are quite a lot:
Details about the top-20 most actively attacking IPs. Nothing unexpected here, although an IP owned by a major Bulgarian ISP (A1) occupies one of the top places and it's somewhat funny to be attacked by a railway station in Sweden:
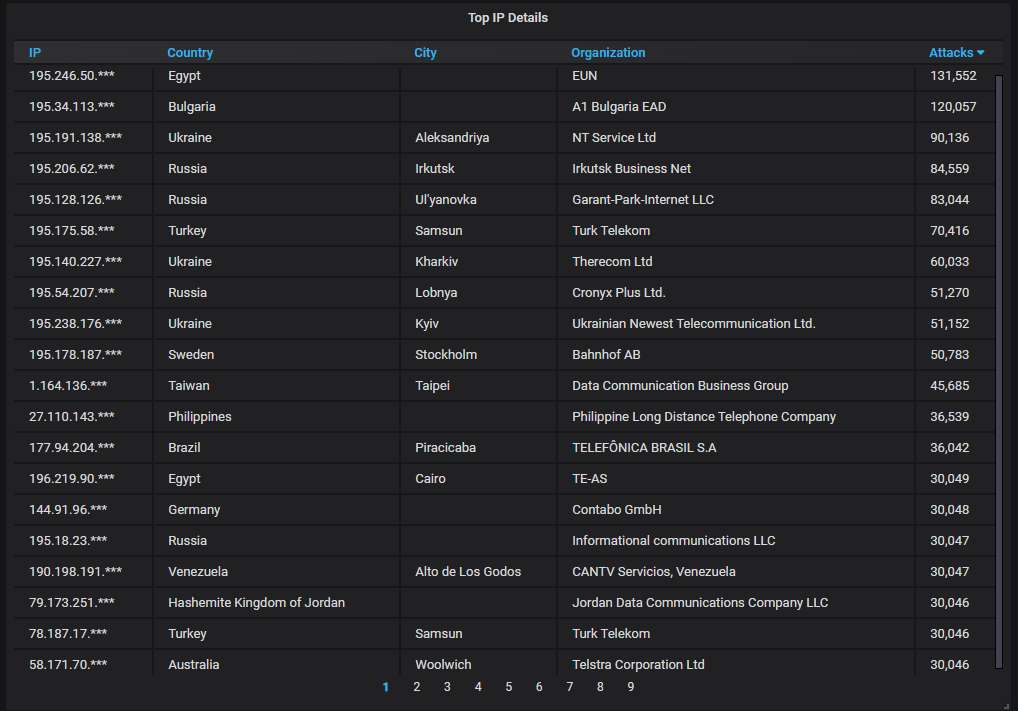
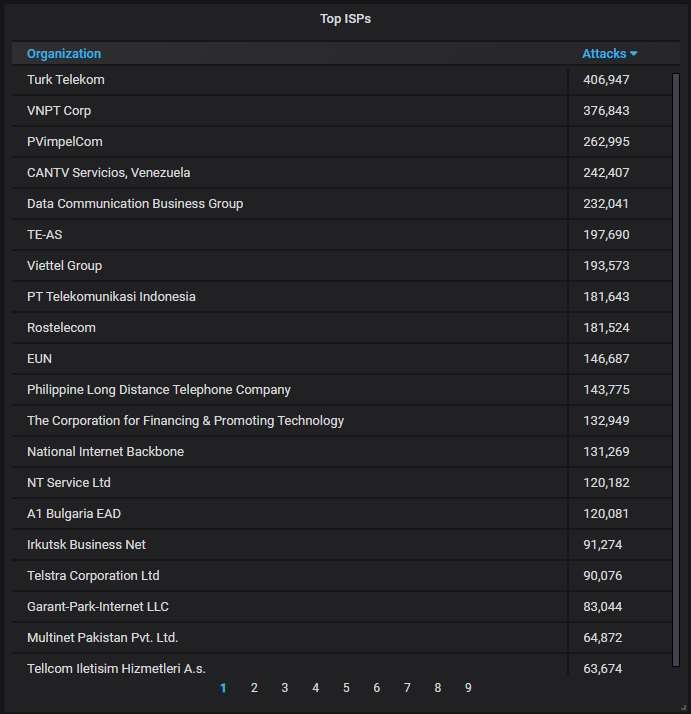
The top-20 organizations from which most of the attacks are coming from. Nothing unexpected here:
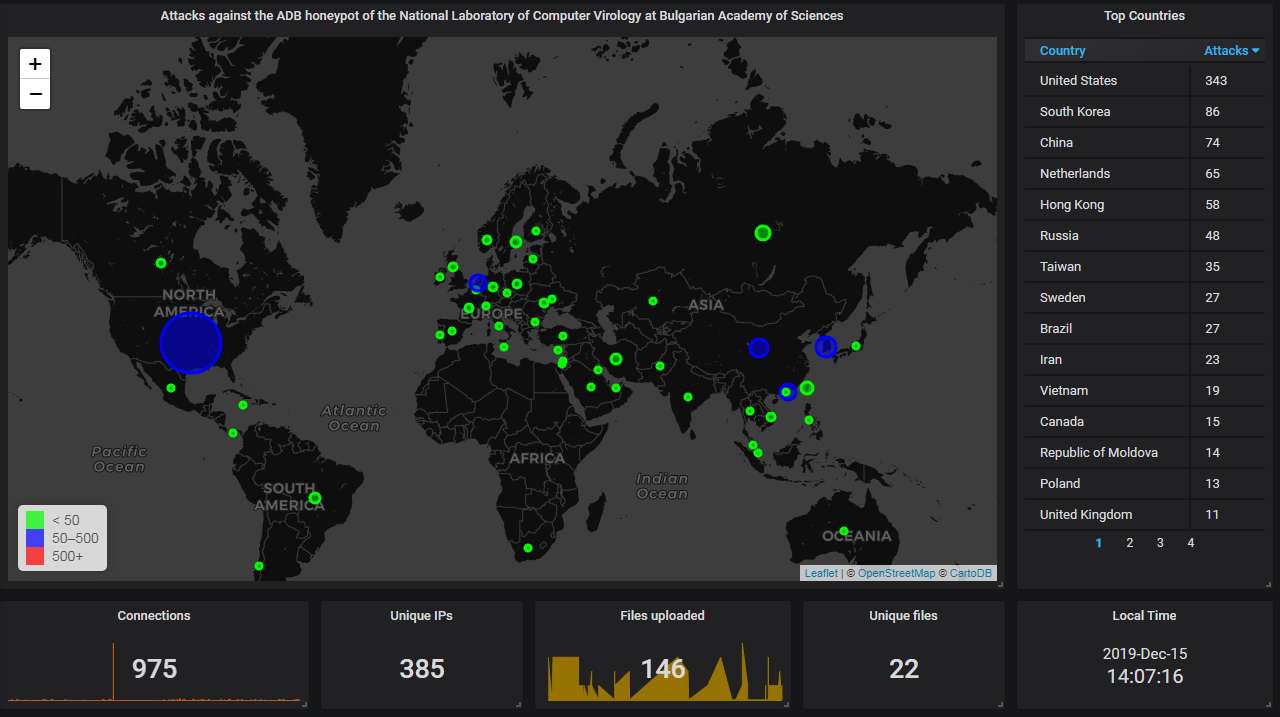
Finally, the data from our ADB honeypot.
The big picture. The USA, South Korea, and China dominate:
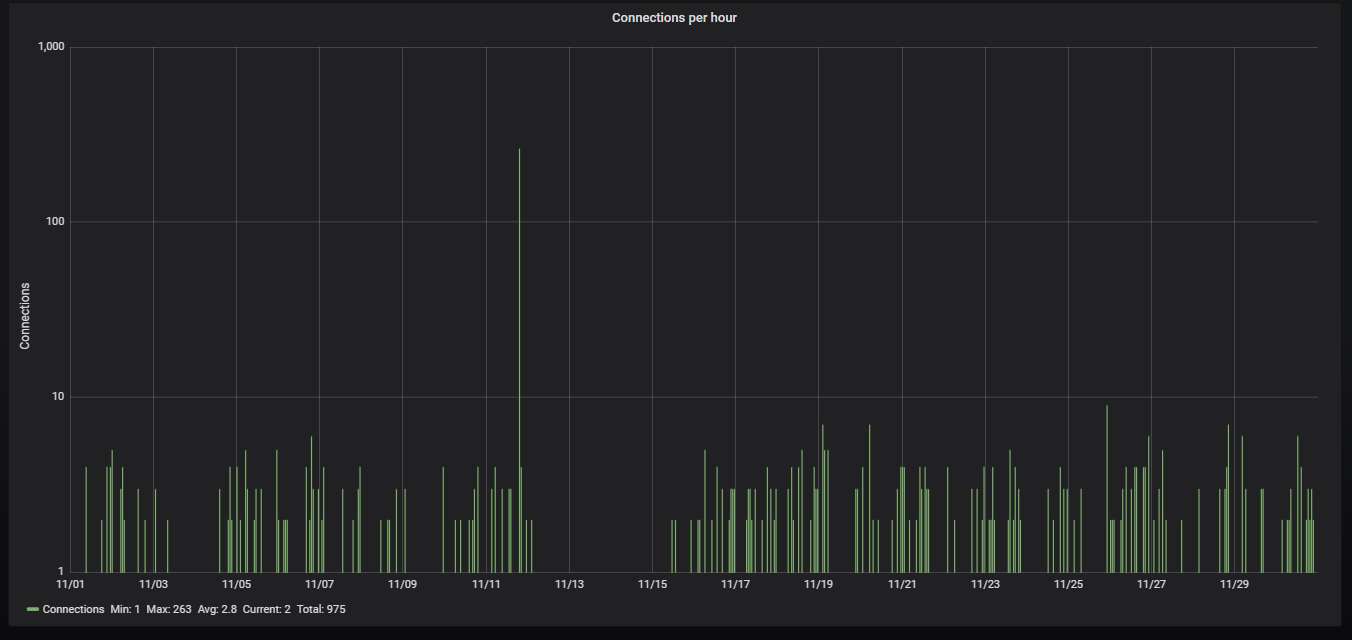
The hourly connection data, showing averagely one attack every half an hour:
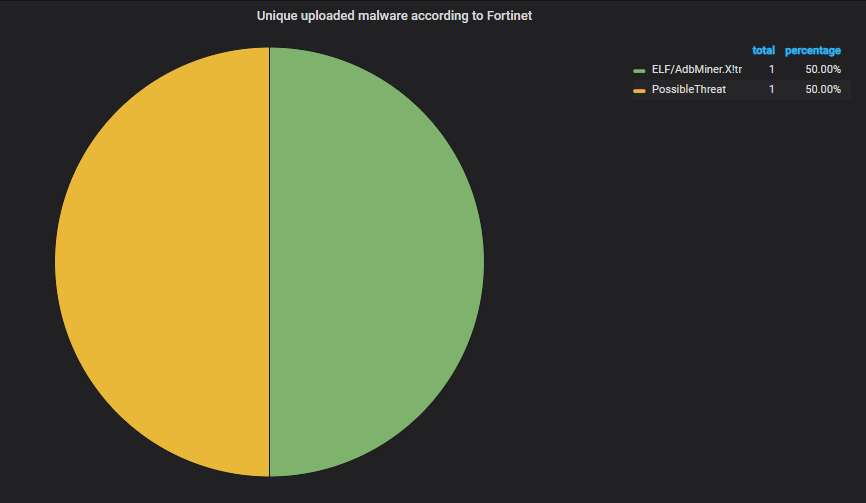
The malware uploaded to the honeypot, according to Fortinet's scanner. The same old Monero mining worm (Trinity) is causing most of the ADB traffic, plus something that is uploading a shell script that looks vaguely Mirai-like:
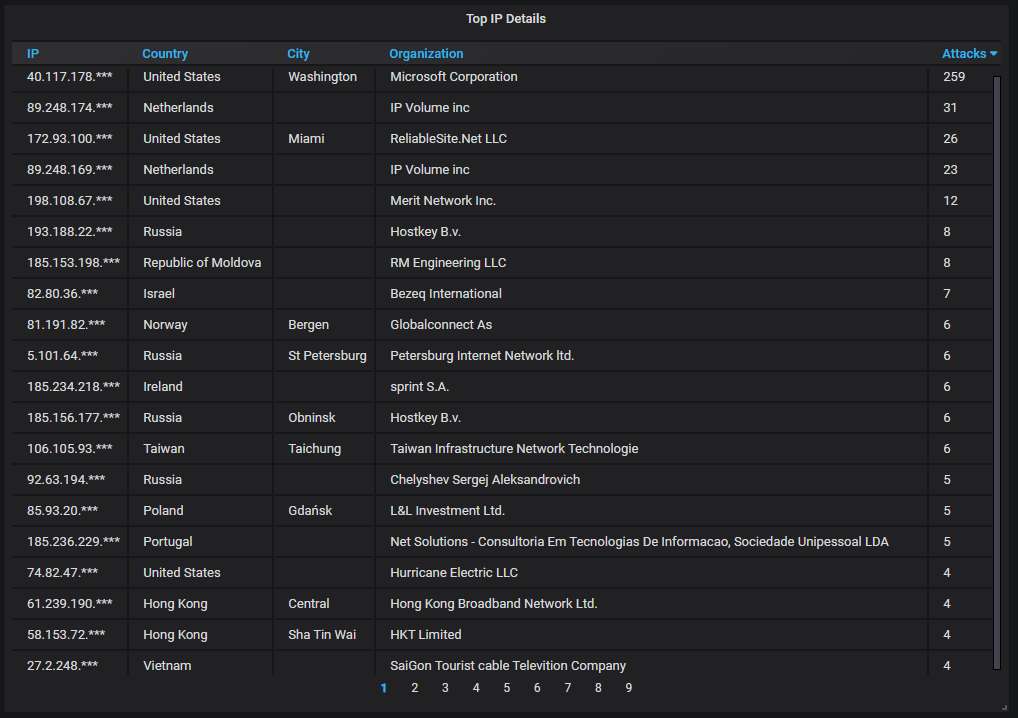
Details about the top-20 most actively attacking IPs. The top spot is firmly occupied by an IP that belongs to Microsoft. It is also the cause for the huge lonely spike on the hourly chart.
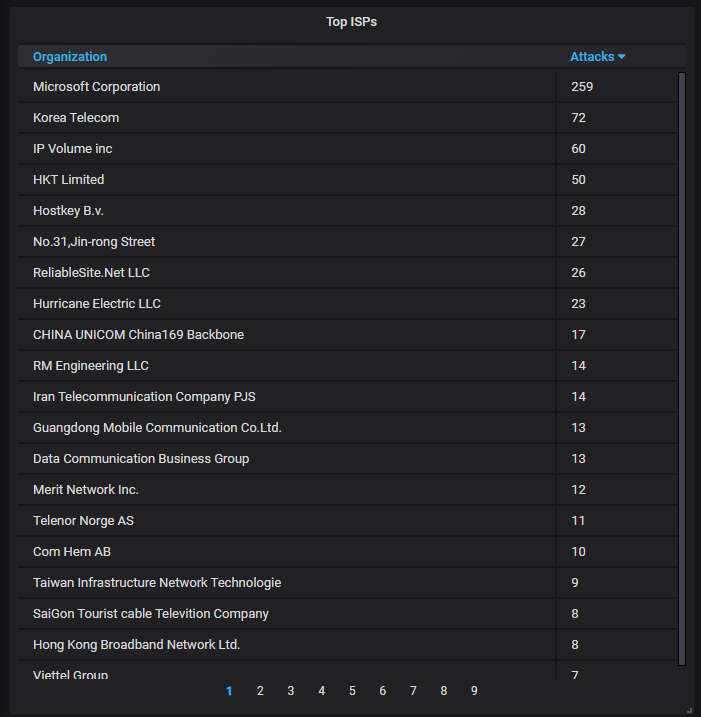
The top-20 organizations that own the IP addresses attacking us. Again, Microsoft holds the top spot because of the rogue IP mentioned above:
This concludes the November honeypot report.
