March honeypot report
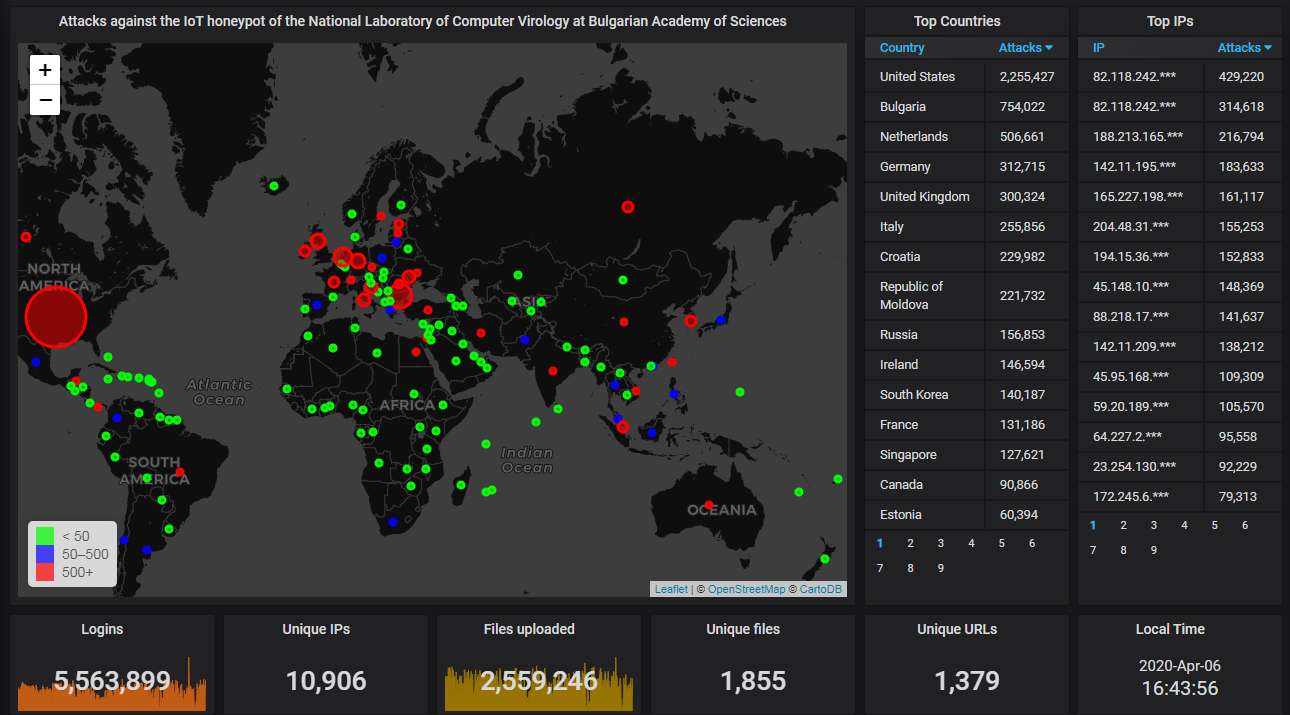
First, the data from our Telnet & SSH honeypot. As almost always, the USA holds the top spot. Sadly, our country (Bulgaria) is again among the top three:
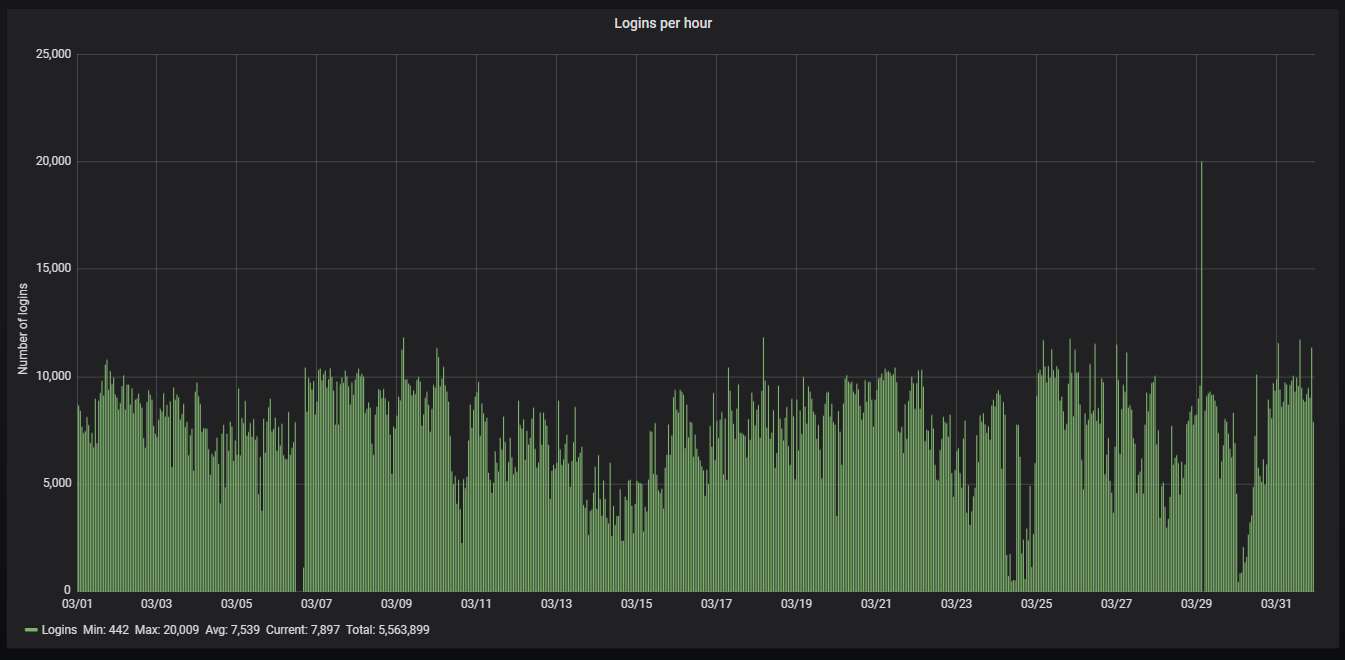
Here is how the hourly activity looks like. The honeypot is being attacked slightly more often than 2 times per second:
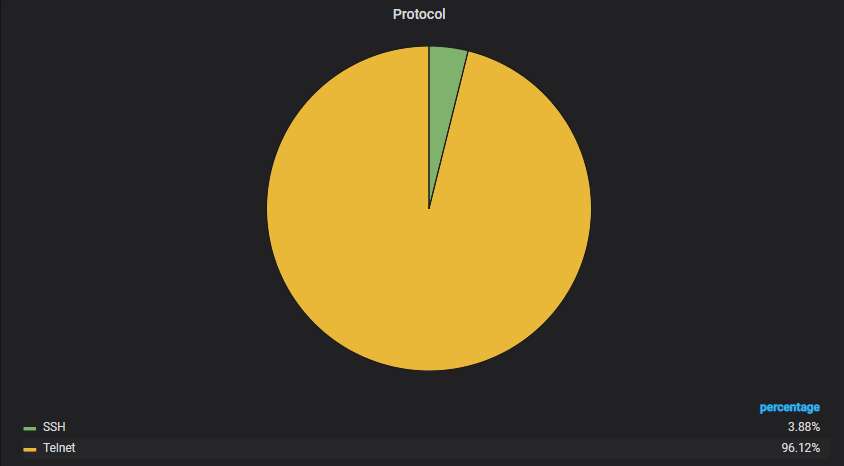
More than 96% of the attacks are via Telnet, the rest are via SSH:
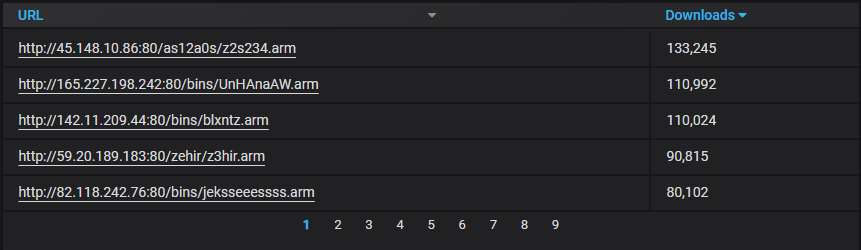
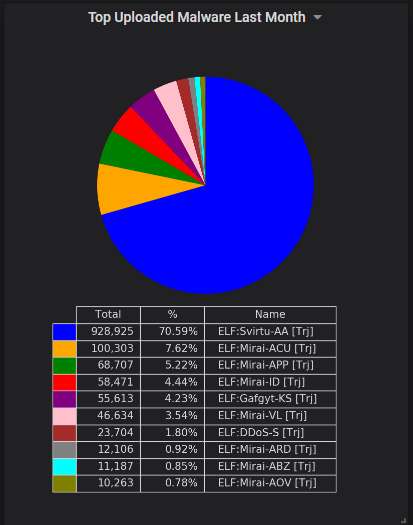
The top-5 URLs from which malware was most actively uploaded to the honeypot. Mirai variants all of them, as usual, although the original variant is not among them.
Indeed, as you can see, uploads of various Mirai variants (IMO, "Svirtu" is a Mirai variant too) dominate heavily. Gafgyt is substantially different and it accounts for only 4.23% of the uploads. Some kind of DDoS bot makes up for another 1.8% of the uploads. This is unusual diversity this month; usually everything is Mirai variants.
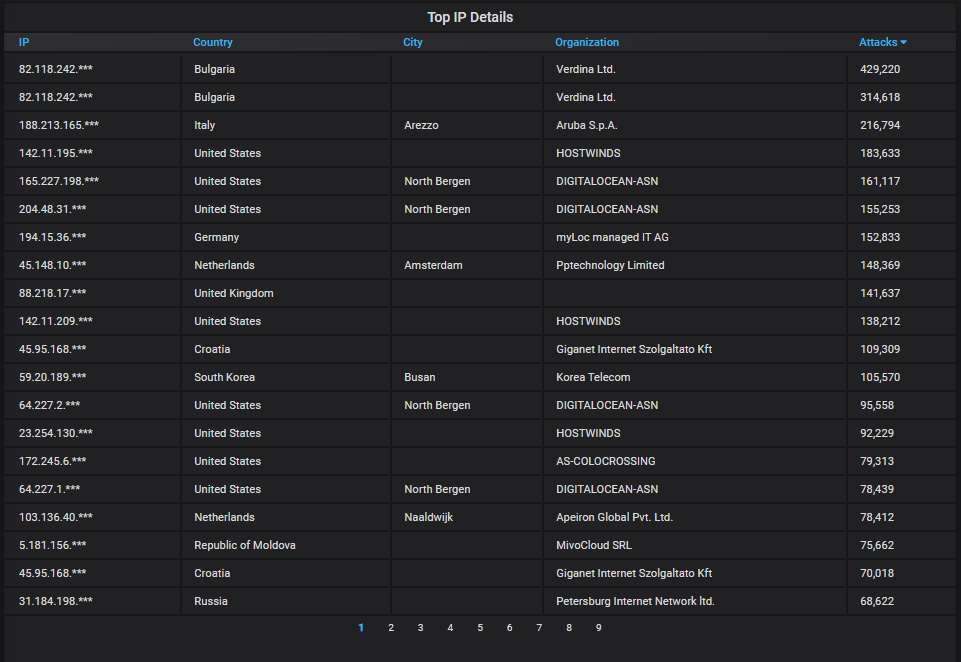
Details about the top-20 most actively attacking IPs. Again infected machines in Verdina Ltd. are causing most of the attack traffic coming from Bulgaria:
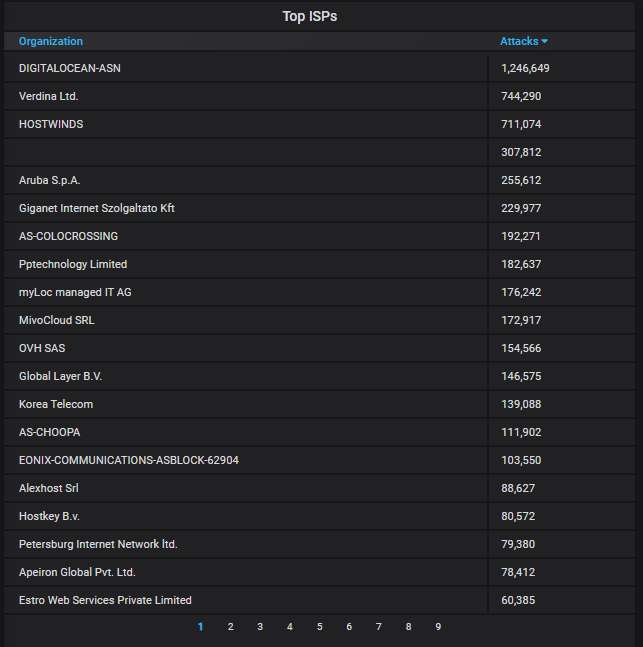
The top-20 most actively attacking organizations. DigitalOcean is again at the top spot, followed by the Bulgarian company that is responsible for placing our country at the 2nd place of the top attacking countries:
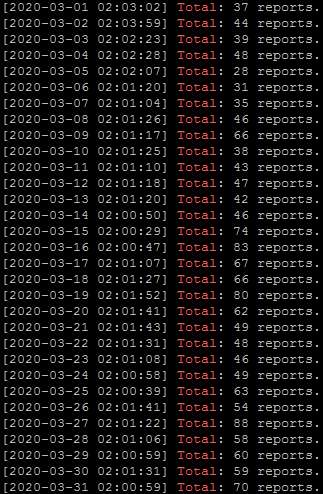
Speaking of DigitalOcean, as you can see, I've been sending them averagely naerly 54 abuse reports every day - but it doesn't seem to be helping very much:
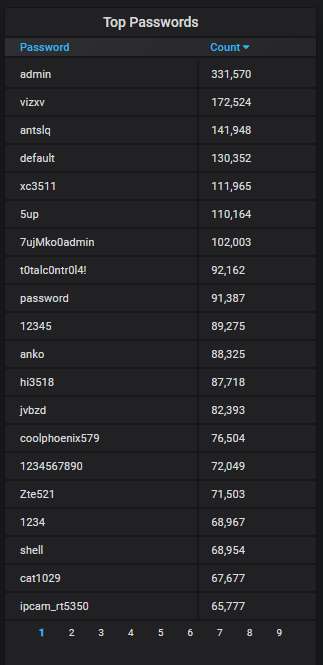
The top-20 passwords that are the most often used by the attackers; nothing unusual here:
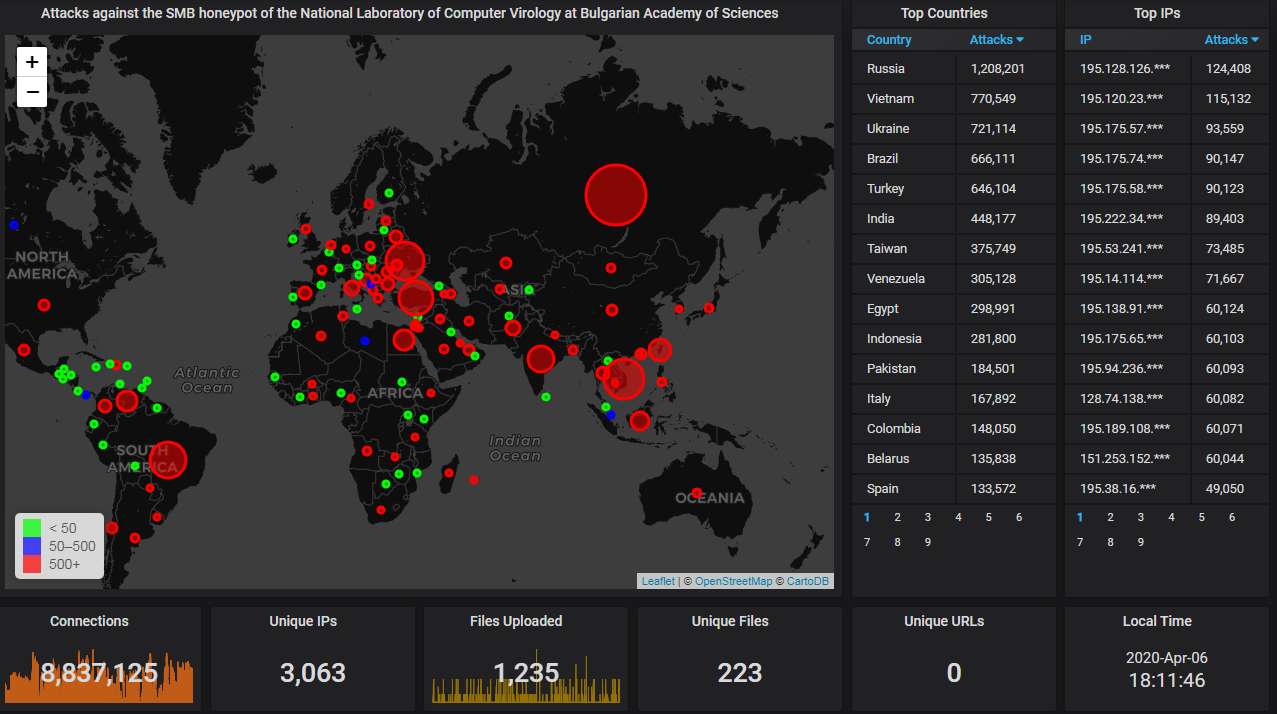
Moving on to our SMB honeypot.
First, the big picture. Most of the action is in Russia again, although Vietnam is again well-represented too. This month the number of attacks against our SMB honeypot exceeds nearly 1.6 times the combined number of attacks against our Telnet and SSH honeypots:
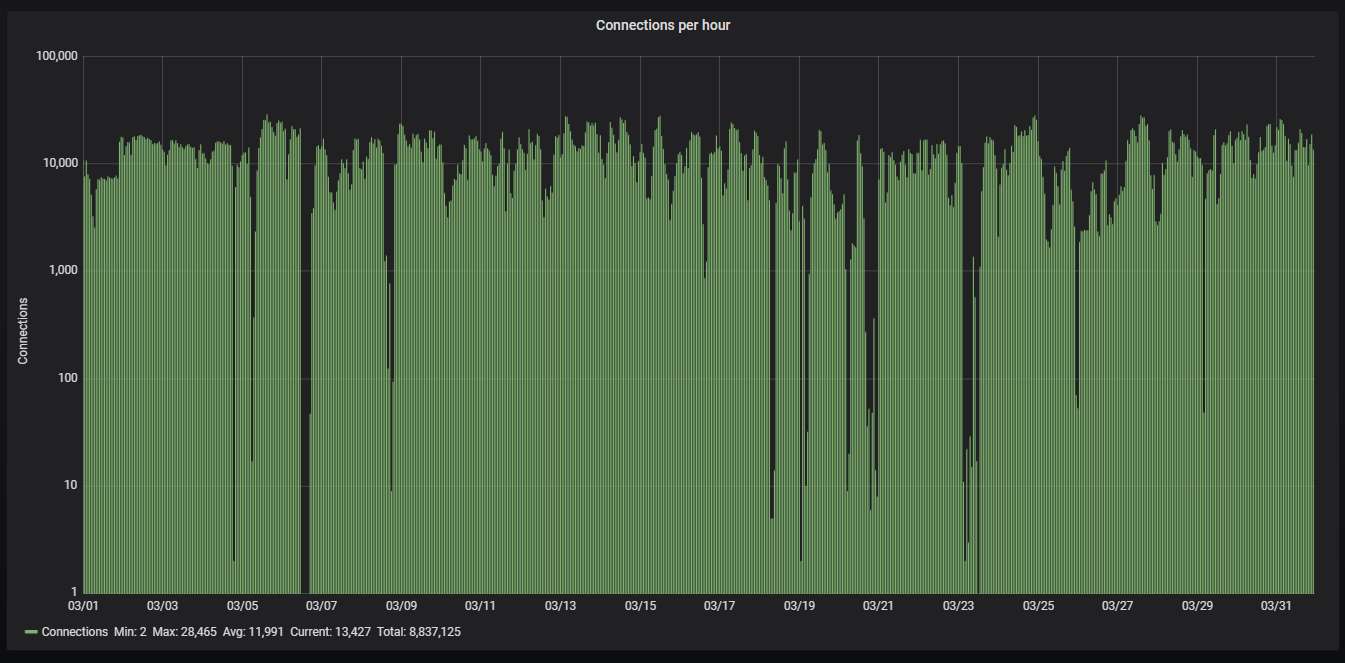
Hourly activity, showing on average more than 3.3 attacks per second; pretty steady traffic, with some very short-timed pauses:
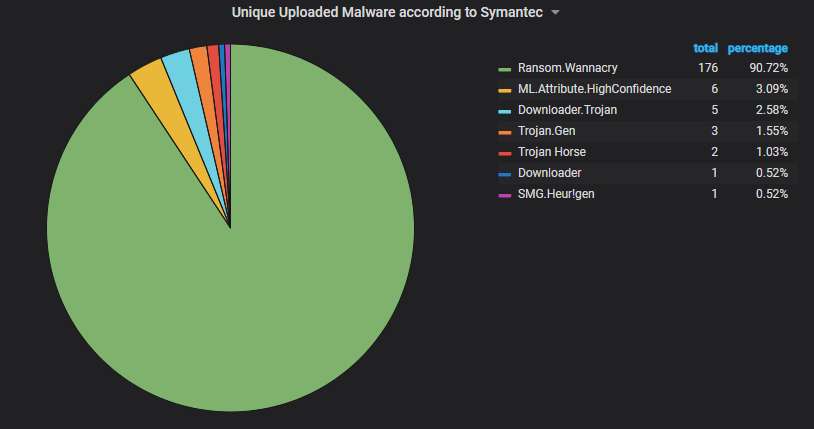
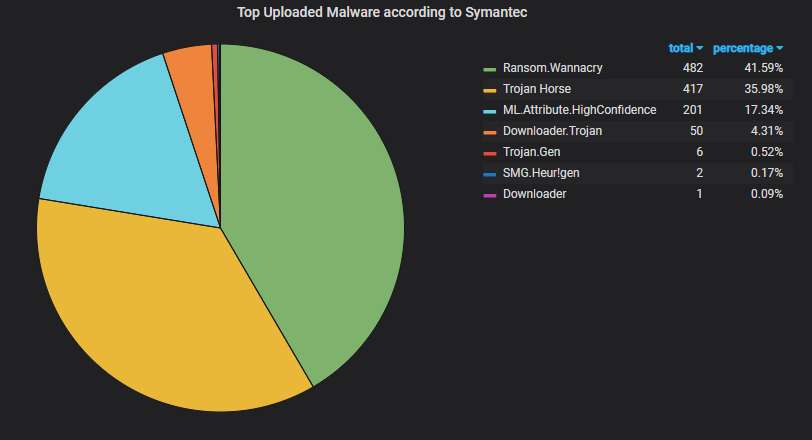
Unique uploaded malware variants, according to Symantec's scanner. The corrupted WannaCry variants (no kill switch check, no encryption) dominate, as usual, although their total number seems to be abating:
Even if we don't count only the unique variants, the WannaCry samples dominate:
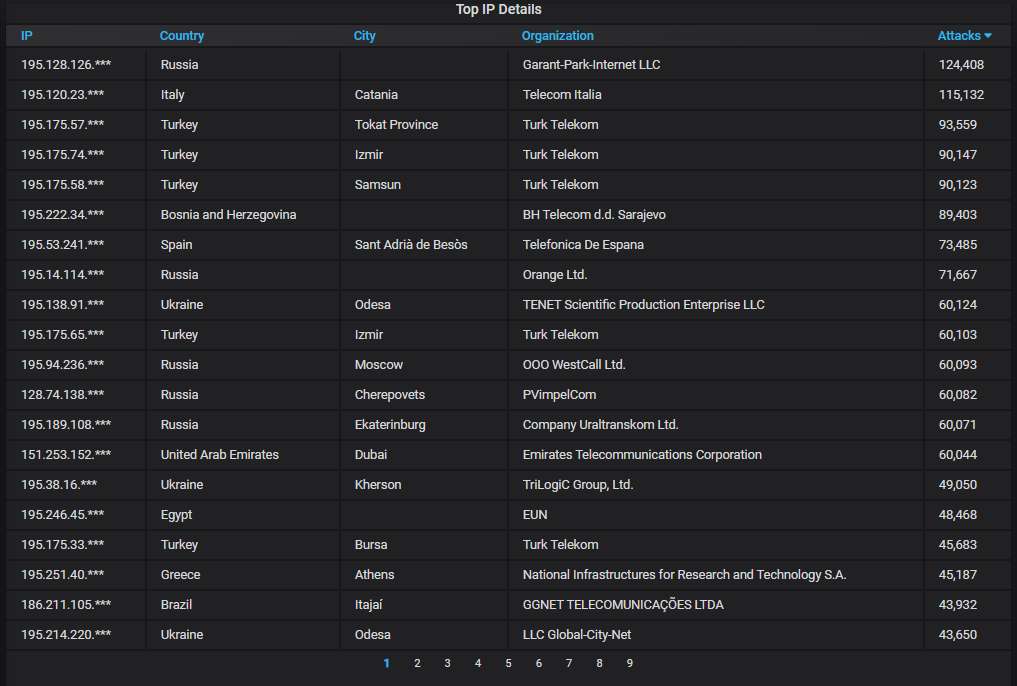
Details about the top-20 most actively attacking IPs. Nothing unusual here:
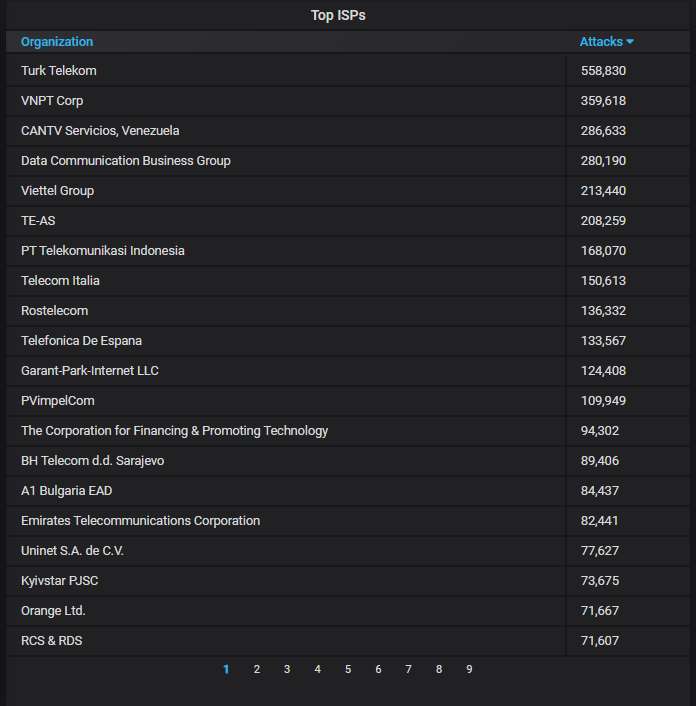
The top-20 organizations from which most of the attacks are coming from. Nothing unusual here, either:
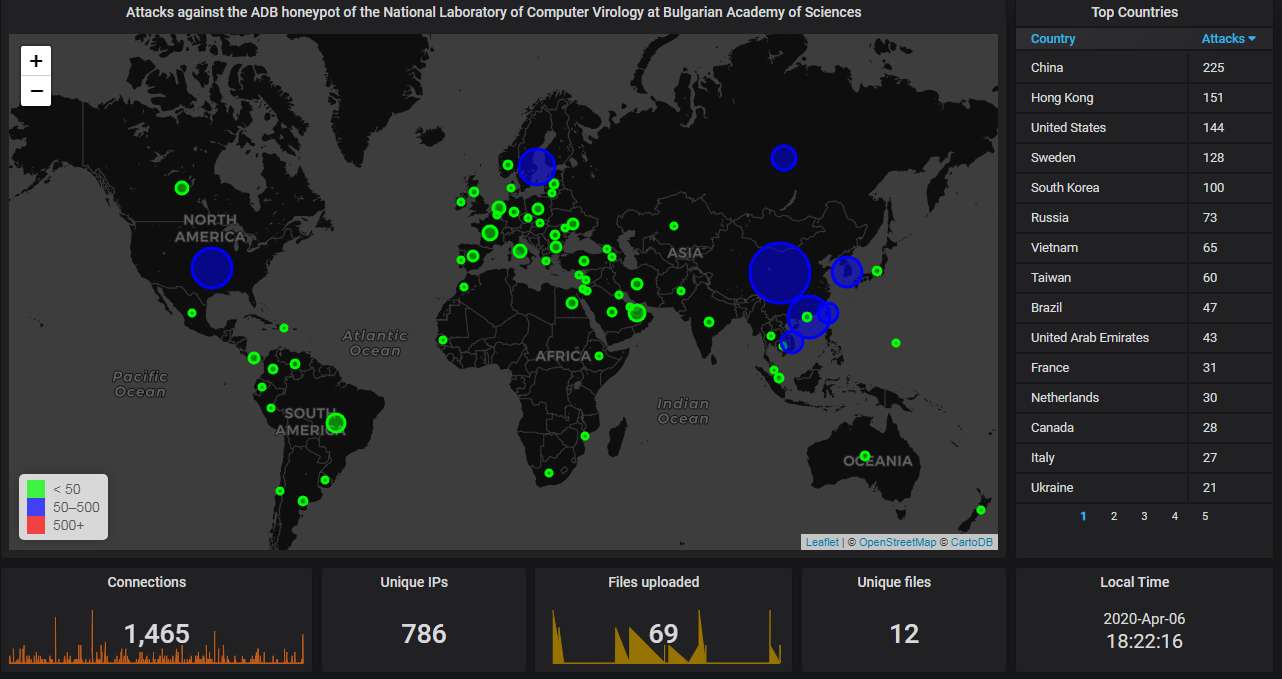
Finally, the data from our ADB honeypot.
The big picture. The Far East (China, Hong Kong, South Korea) dominates as usual, but the USA and this time, surprisingly, Sweden figure prominently, too:
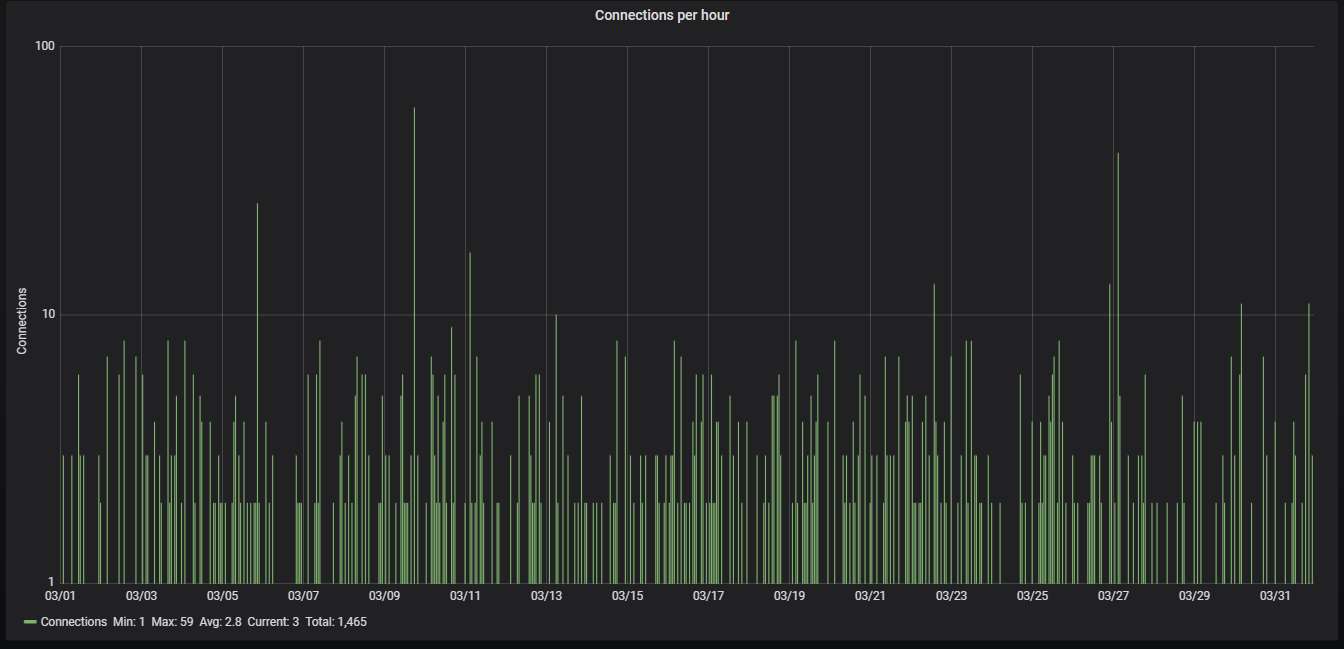
The hourly connection data, showing averagely 1.4 attacks per hour:
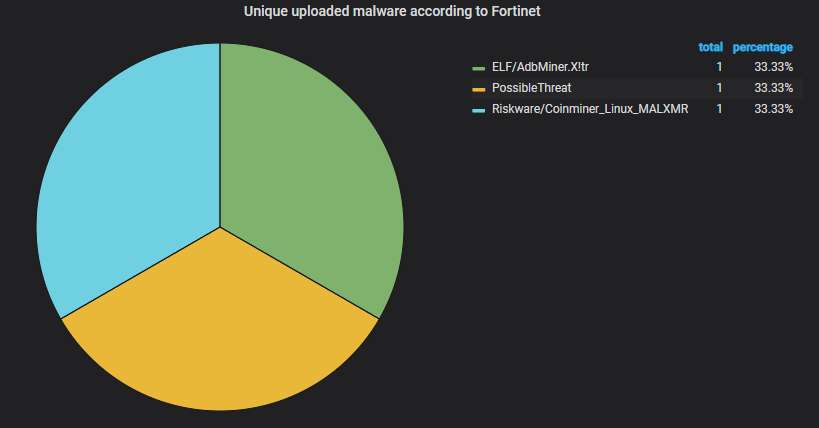
The unique malware uploaded to the honeypot, according to Fortinet's scanner. The two parts of same old Monero mining worm (Trinity) is causing almost all of the malicious uploads but this month we see some other cryptomining bot make an appearance too:
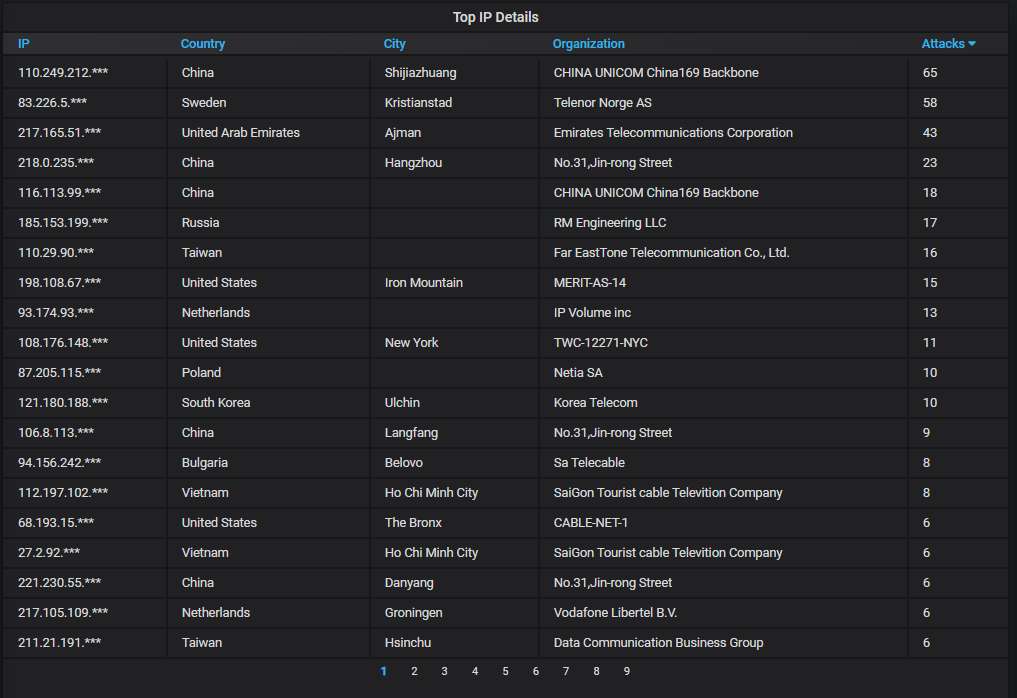
Details about the top-20 most actively attacking IPs:
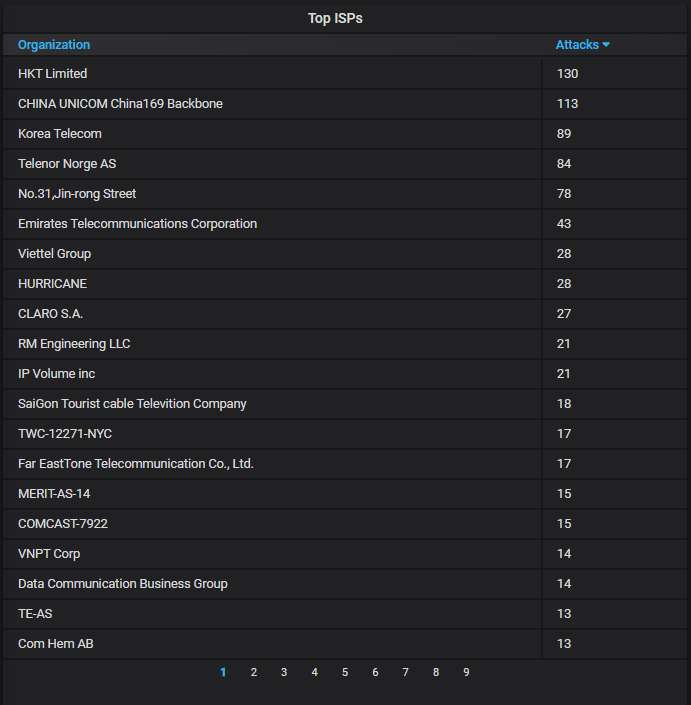
The top-20 organizations that own the IP addresses attacking us:
This concludes the March honeypot report.
